Network attack prediction method and device
A network attack and prediction method technology, applied in the field of network security, can solve the problems of maintaining network security, inability to predict network attack behavior, disadvantage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
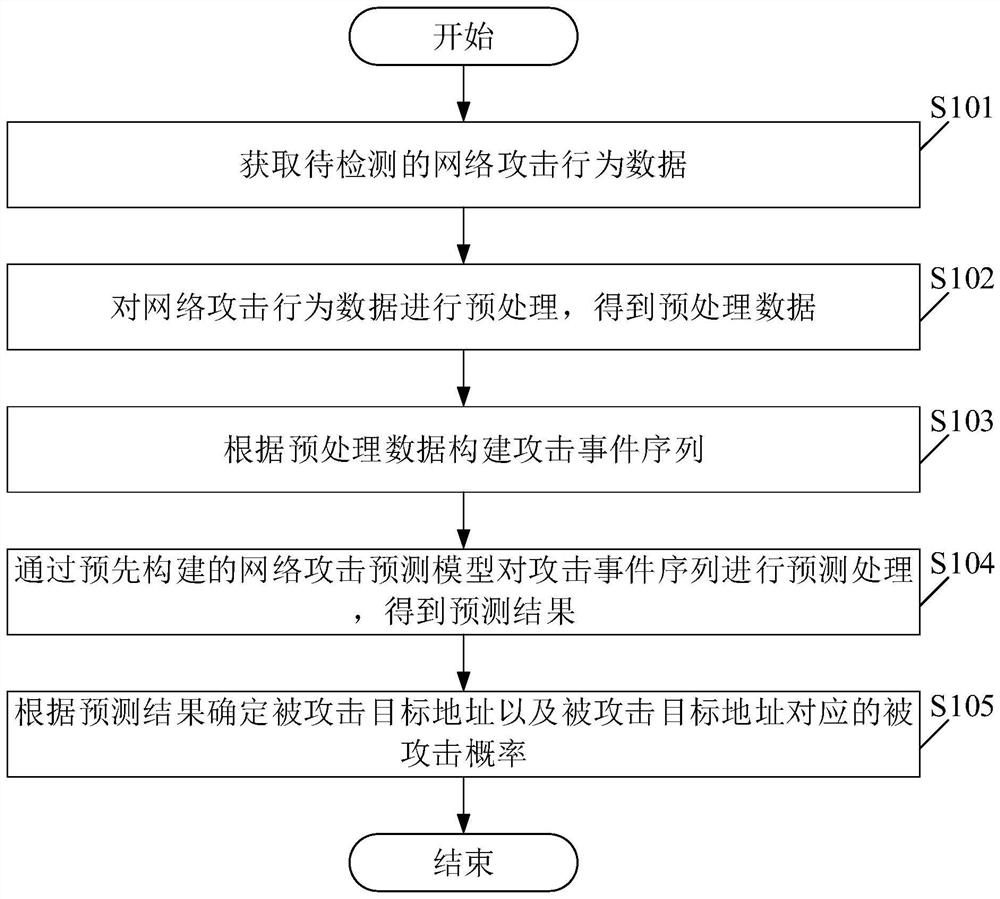
[0057] Please see figure 1 , figure 1 A schematic flowchart of a network attack prediction method is provided for the embodiment of the present application. Among them, the network attack prediction method includes:
[0058] S101. Obtain network attack behavior data to be detected.
[0059]In the embodiment of this application, the network attack behavior data includes network attack behavior data and associated log data in a long historical period, specifically including data related to attack events, such as attack program data, web page (WEB) attack data, and blasting data. etc., extract the attack source IP and target IP fields to obtain the relevant data of the attack event.
[0060] S102. Preprocessing the network attack behavior data to obtain preprocessed data.
[0061] In the embodiment of the present application, the preprocessing of the network attack behavior data mainly includes processing such as filtering invalid attack behaviors and extracting attack behavi...
Embodiment 2
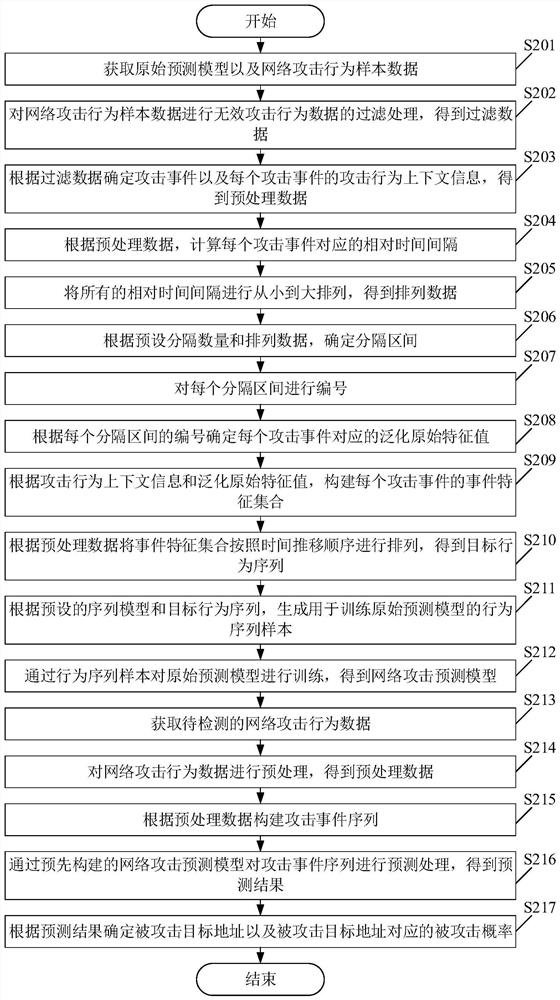
[0080] Please see figure 2 , figure 2 It is a schematic flowchart of another network attack prediction method provided in the embodiment of the present application. Such as figure 2 As shown, wherein, the network attack prediction method includes:
[0081] S201. Obtain an original prediction model and network attack behavior sample data.
[0082] In the embodiment of the present application, the network attack behavior sample data in the range of the most recent period before the current moment may be used for sequence behavior modeling and model training.
[0083] In the embodiment of the present application, the network attack behavior sample data includes network attack behavior sample data and associated log sample data in a long historical period, and specifically includes related sample data of attack events, such as attack program sample data, webpage (WEB) Attack sample data, blasting sample data, etc., extract the attack source IP and target IP fields to obtain...
Embodiment 3
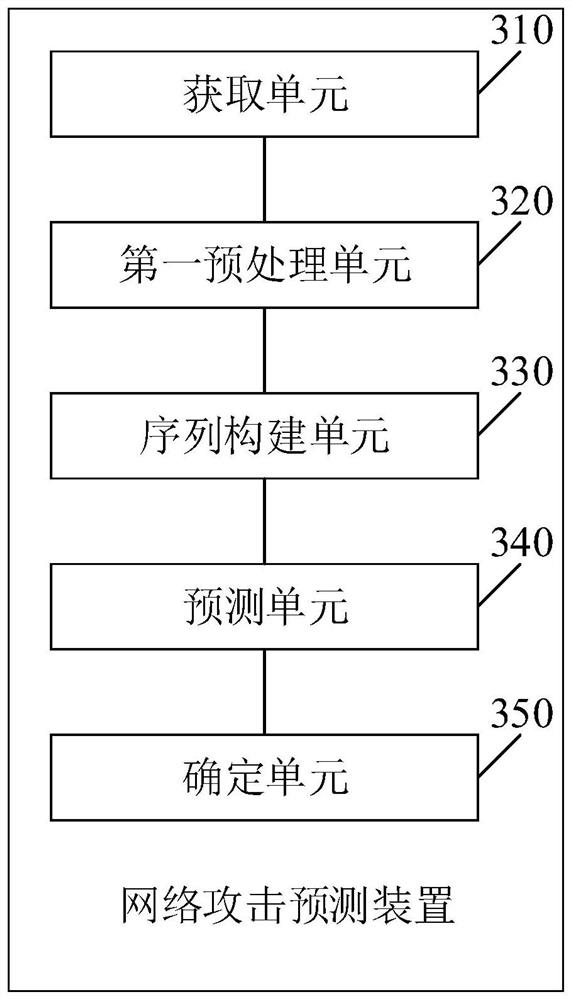
[0152] Please see image 3 , image 3 It is a schematic structural diagram of a network attack prediction device provided in an embodiment of the present application. Such as image 3 As shown, the network attack prediction device includes:
[0153] An acquisition unit 310, configured to acquire network attack behavior data to be detected;
[0154] The first preprocessing unit 320 is configured to preprocess the network attack behavior data to obtain preprocessed data;
[0155] A sequence construction unit 330, configured to construct an attack event sequence according to preprocessed data;
[0156] The prediction unit 340 is configured to perform prediction processing on the attack event sequence through a pre-built network attack prediction model to obtain a prediction result;
[0157] The determining unit 350 is configured to determine the attacked target address and the attack probability corresponding to the attacked target address according to the prediction result....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com