Java vulnerability detection positioning method based on GGNN and hierarchical attention network
A technology for vulnerability detection and localization methods, applied in neural learning methods, error detection/correction, biological neural network models, etc., can solve problems such as increasing research complexity, inability to locate vulnerabilities quickly, and lack of high quality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
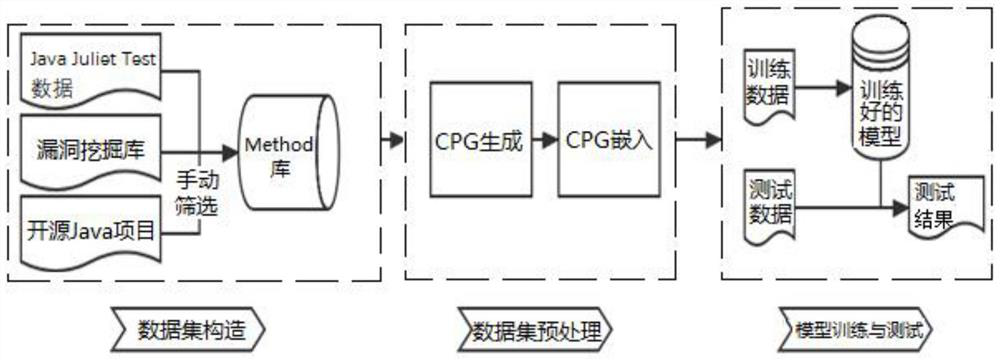
[0055] like figure 1 As shown, it is the overall flowchart of the Java vulnerability detection and location method based on GGNN and hierarchical attention network of the present invention. The process specifically includes the following steps:
[0056] Step 1. Construct a vulnerability dataset, detect and classify vulnerabilities based on machine learning (ML), and obtain a vulnerability dataset with clear granularity, considerable quantity, and excellent quality. The sources of the vulnerability data set in the present invention include Java Juliet Test data, public data sets collected by predecessors, and vulnerability data sets collected from github open source software. in:
[0057] ①The Java Juliet Test data of SARD is manually screened at the Method granularity, and the vulnerability data set at the Method ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com