High-risk operation identification method and system based on user behavior analysis
A technology of behavior analysis and recognition method, which is applied in the field of network security and deep learning, can solve problems that cannot meet network security, achieve the effect of improving accuracy and preventing overfitting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
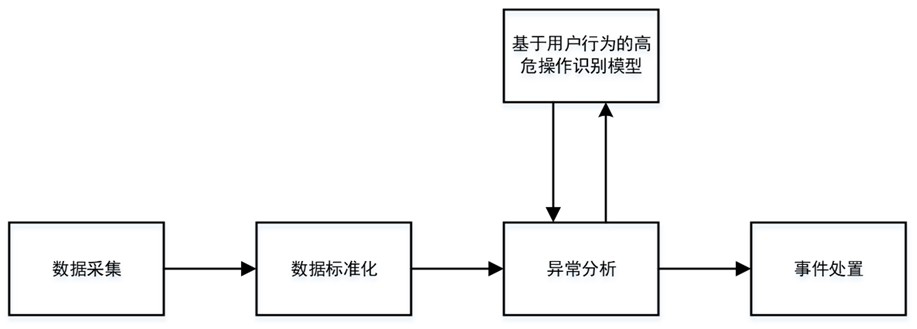
[0044] like figure 1 As shown, the high-risk operation identification method based on user behavior analysis in this embodiment includes the following steps:
[0045] (1) Data collection
[0046] Collect the log information to be tested corresponding to user behavior in the target network.
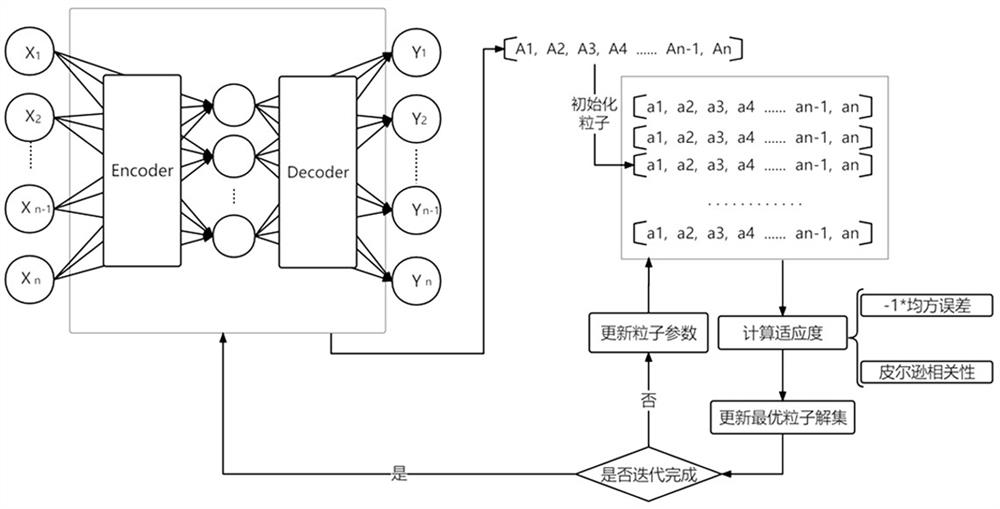
[0047] Specifically, relying on the log collection probe and big data architecture, the collection of different types of access logs, login logs, and operation logs such as hosts and applications in the target network is completed, and the collected log information is used as input for data standardization processing; mainly involves system Login logs, WEB access logs, operation and maintenance operation logs and other types, related devices include different data sources such as network devices, hosts, and application systems. The big data stream computing architecture is used to realize real-time data collection, and subsequent standardization of log information and metadata Extraction...
Embodiment 2
[0120] The difference between the method for identifying high-risk operations based on user behavior analysis in this embodiment and Embodiment 1 is that:
[0121] The high-risk operation identification method based on user behavior analysis also includes:
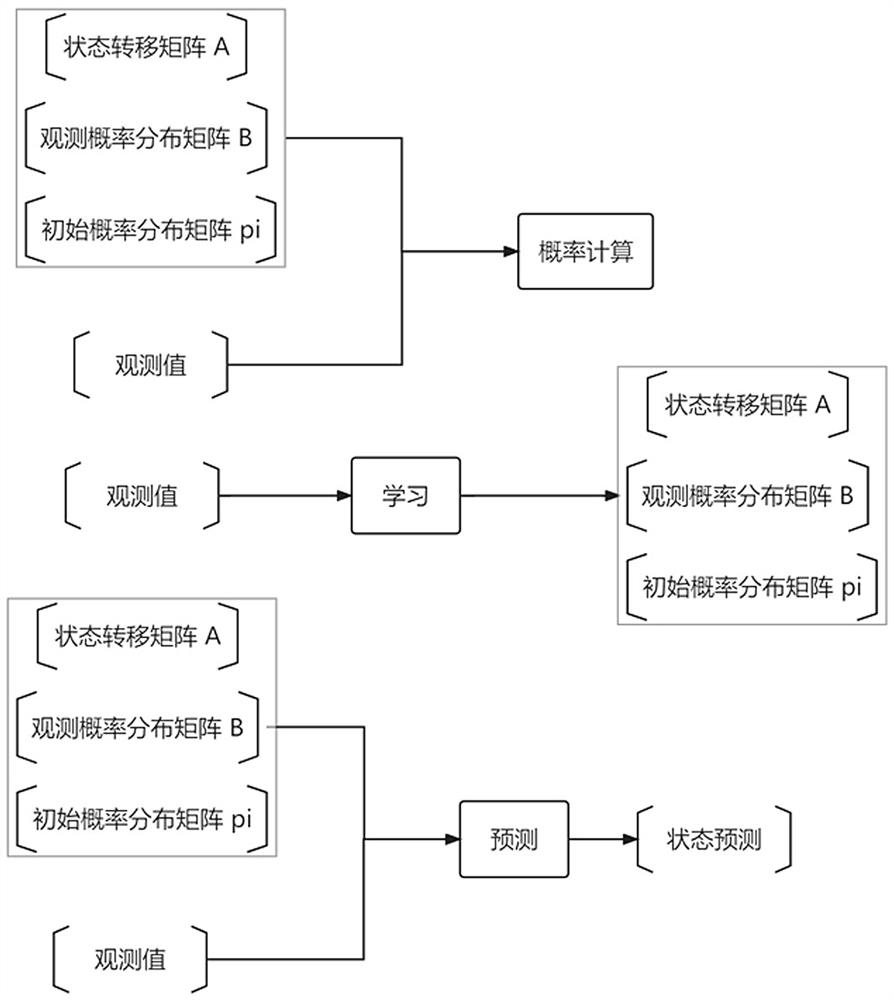
[0122] In the follow-up forecasting process, the output and status values of the three abnormal indicators are output once a day, and the status values of the seven-day observation sequence are predicted every week to calibrate and judge the daily output results to further improve the accuracy of recognition ;
[0123] Other steps can refer to embodiment 1;
[0124] The difference between the high-risk operation identification system based on user behavior analysis in this embodiment and Embodiment 1 is that:
[0125] It also includes a calibration module, which is used to output the output and status values of the three abnormal indicators once a day in the subsequent forecasting process, and forecast the status v...
Embodiment 3
[0128] The difference between the high-risk operation identification system based on user behavior analysis in this embodiment and Embodiment 1 is that:
[0129] Linkage with 4A and other account management platforms, connect with account blocking capabilities, and realize user account enable / disable, user logout and session logout operations;
[0130] For other frameworks, refer to Example 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com