Image visual security encryption method based on compressed sensing and least significant bits
A least significant bit, compressed sensing technology, applied in the field of information security, can solve problems that cannot meet the needs of scenarios
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0082] The present invention will be further described below in conjunction with the embodiments. Obviously, the described embodiments are only some of the embodiments of the present invention, not all of them. Based on the embodiments of the present invention, all other embodiments obtained by persons of ordinary skill in the art without making creative efforts belong to the protection scope of the present invention.
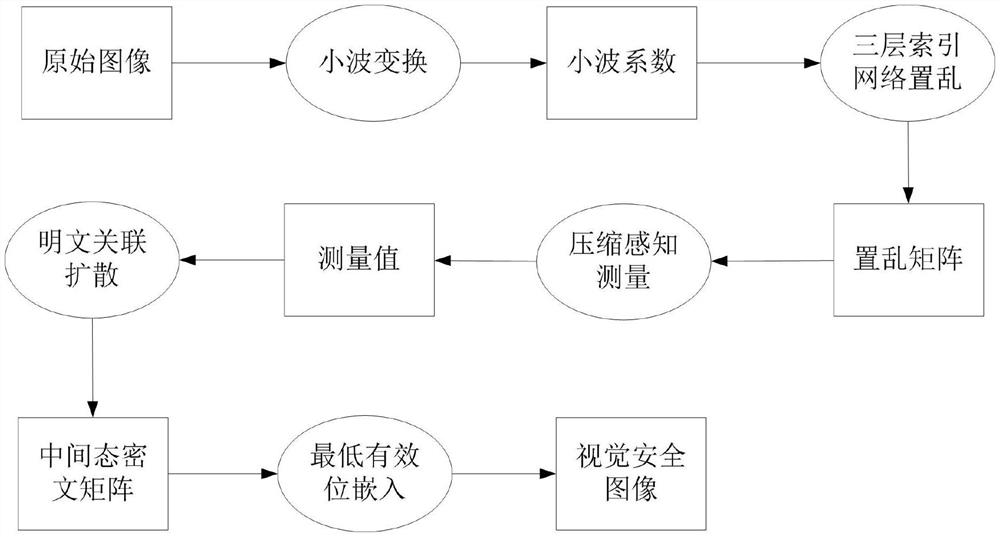
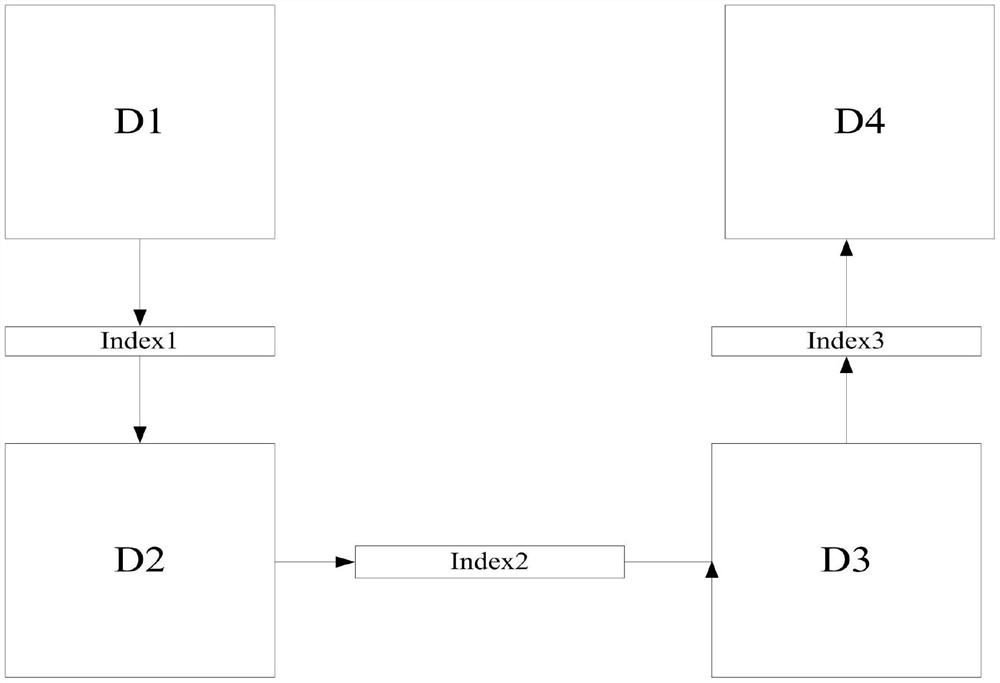
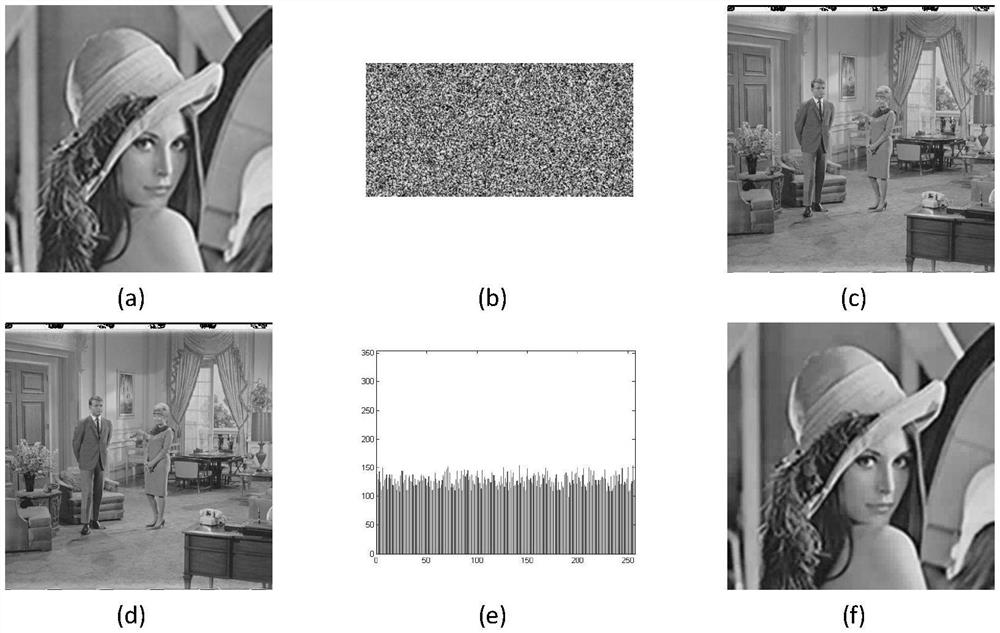
[0083] The image compression encryption method that the present invention proposes mainly has the following steps:
[0084] The first step is to select an image X with a size of M×N, and perform a hash operation on it to obtain a string of 512-bit binary numbers, which are converted into decimal numbers and decimalized to obtain the initial key x of the equation 0 ;
[0085] In the second step, the initial key x 0 Input it into the one-dimensional high randomness chaotic equation, iterate 4×M×N times, in order to ensure the randomness of the pseudo-random seq...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com