Batch host security scanning and reinforcing method
A security scanning and host technology, applied in the field of computer information, can solve problems such as system abnormal termination, inability to adapt, errors, etc., achieve robust batch management and avoid repetitive work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
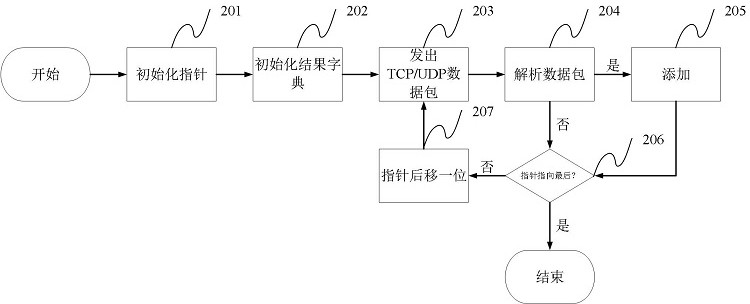
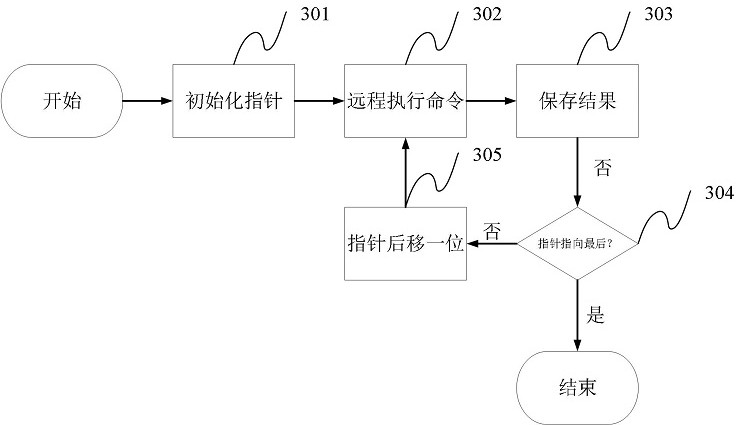
[0039] In a first aspect, the present invention provides a batch host security scanning and reinforcement method, including: an online host scanning method, a system vulnerability scanning method, and a host reinforcement method.
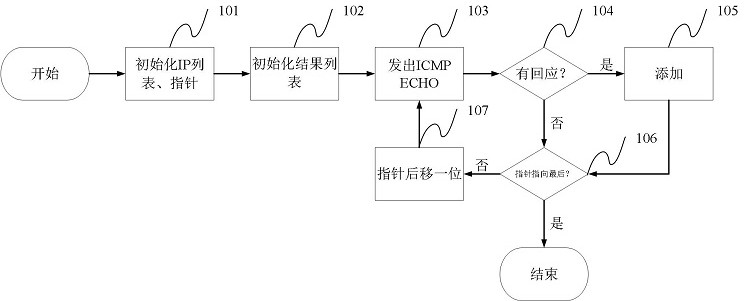
[0040] see figure 1 , in response to receiving an online host scanning instruction, use the host scanning method to scan all online hosts in the LAN, and the process is as follows:
[0041] Input: the address of the network segment to be scanned (format: network / network prefix length, for example: 192.168.24.0 / 24)
[0042] Output: List of online host IPs
[0043] 101) Generate a host IP address list in the network segment, initialize the pointer position as the first ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com