Software authorization method and software authorization system based on block chain
A technology of software authorization and blockchain, which is applied in the field of blockchain, can solve problems such as dependence and inability to achieve authorization control, and achieve the effect of increasing speed, improving training convergence speed, and facilitating intelligent control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
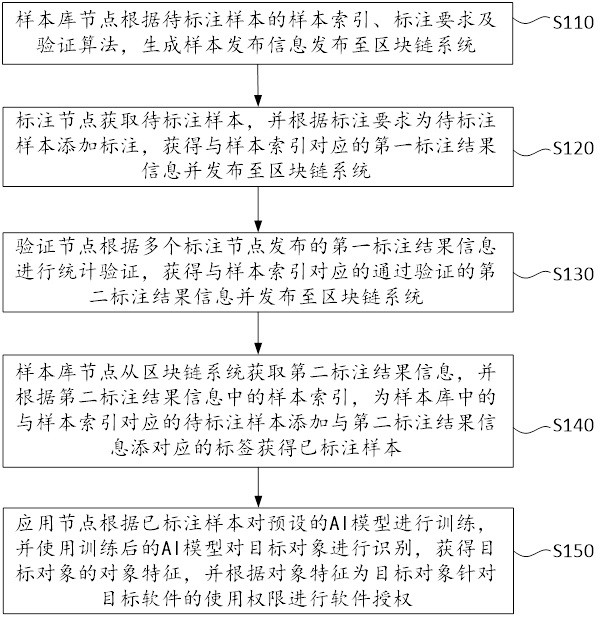
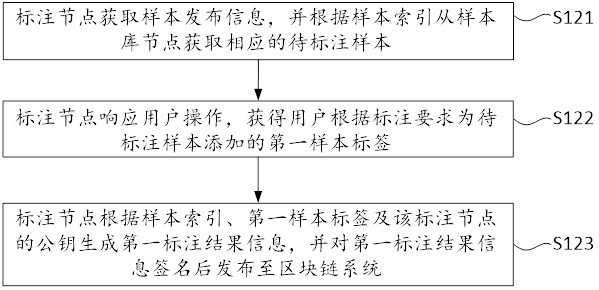
[0086] In order to make the purpose, technical scheme and advantages of the embodiment of the application clearer, the technical scheme in the embodiment of the application will be clearly and completely described below in combination with the attached drawings in the embodiment of the application. Obviously, the described embodiments are part of the embodiments of the application, not all of the embodiments. The components of the embodiments of the present application generally described and shown in the drawings herein may be arranged and designed in a variety of different configurations.
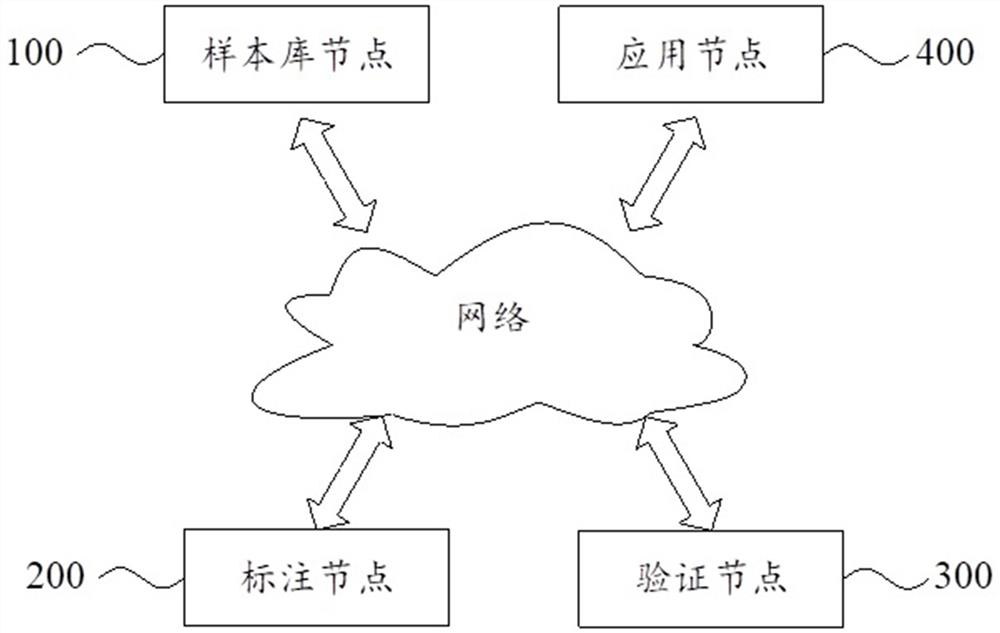
[0087] See Figure 1 , Figure 1 The node 400 and the software authorization Library of the system can provide a schematic diagram of the node 400 and the software authorization Library of the system. The sample library node 100, the annotation node 200, the verification node 300 and the application node 400 can communicate with each other through the network. The sample library node 100 can be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com