Method and device for realizing DDOS user matching based on Trie tree
A user and user information technology, applied in the field of network security, to achieve high query efficiency, improve overall response time, and reduce unnecessary comparisons
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0061] The relevant configurations to realize the DDOS user matching of the Trie tree are as follows:
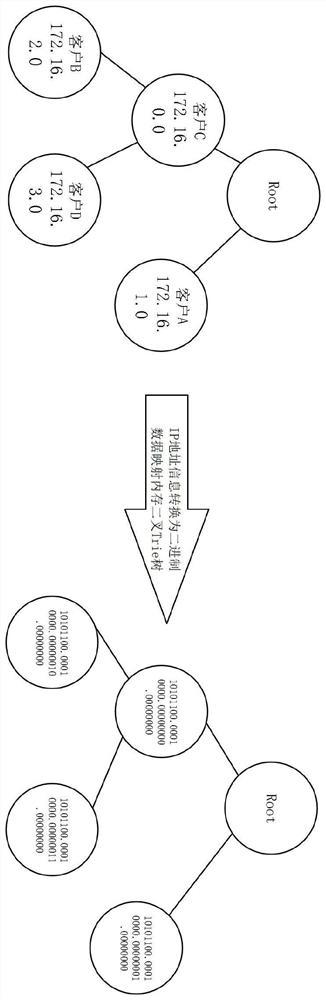
[0062] Target user A: the CIDR network segment information 172.16.1.0 / 24;
[0063] Target user B: the CIDR network segment information 172.16.2.0 / 24;
[0064] Target user C: the CIDR network segment information 172.16.0.0 / 16.
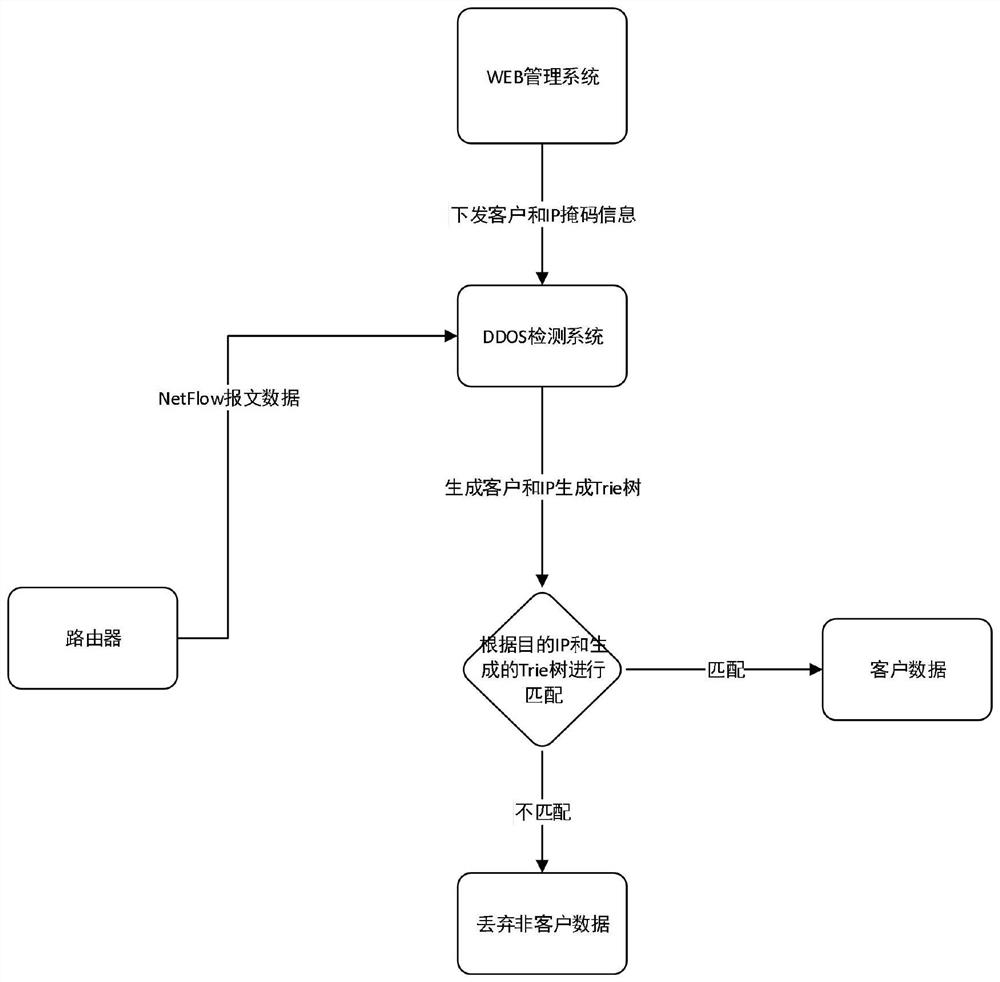
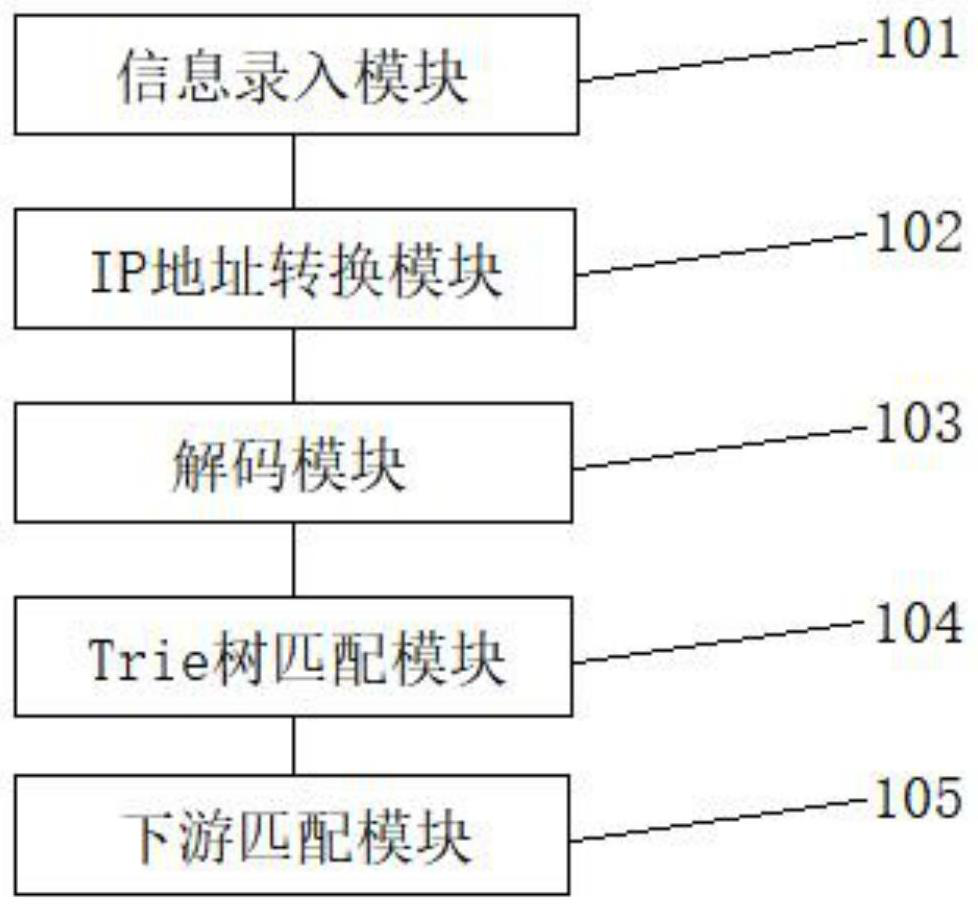
[0065] S01. Send the above configuration target user and the CIDR network segment information to the downstream detection system through the web management system, and the downstream system stores the information in the system after receiving the request information;
[0066] S02. After the detection system receives the user and CIDR network segment information, it generates a Trie tree structure for the information and places it in the memory. The generated Trie tree class is as follows figure 2 shown;
[0067] S03. The router sends the netflow message to the detection system. After receiving the netflow message, the system parses the netflow mes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com