Method and device for executing multi-party secure multiplication
An execution method and an execution device technology, which are applied in the field of secure computing, can solve problems such as increased computation and communication traffic, and achieve the effects of improving computing efficiency and reducing data communication traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The technical solutions provided in this specification will be described below in conjunction with the accompanying drawings.
[0041] First, some concepts that may be involved in this specification are described.
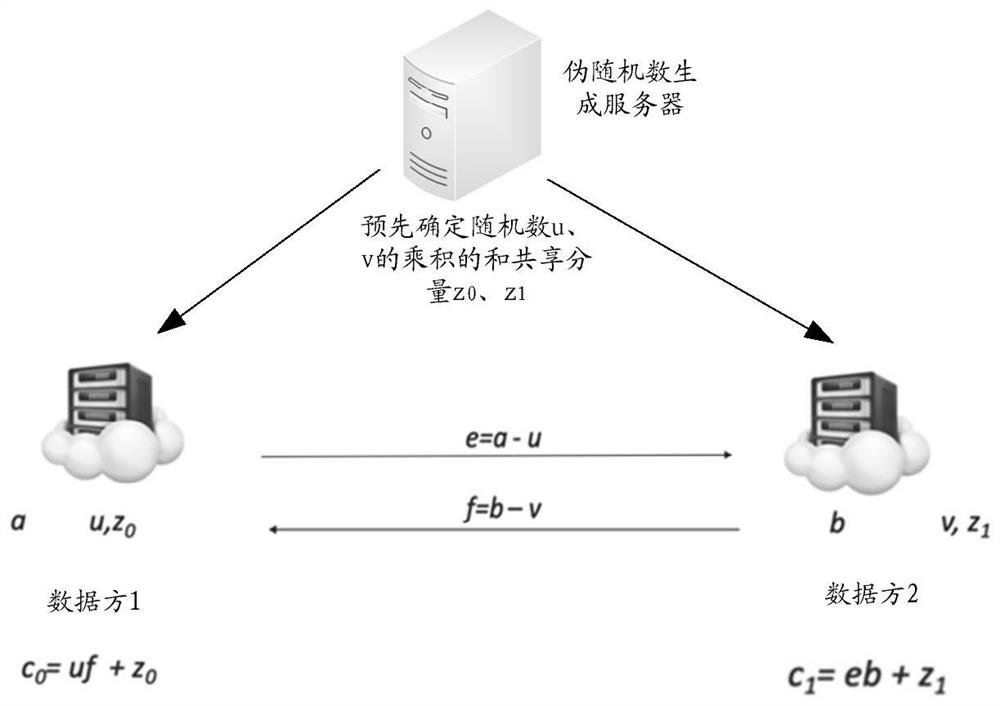
[0042] And sharing: In the two-party security calculation, an integer x from 0 to M-1 is set as x=x L +x R Distributed and stored in two parties in a shared form of modulo M, so that one party does not know x R , the other party does not know x L , neither of the two parties can get the complete form of x; further, the two parties can be expanded into multiple parties.
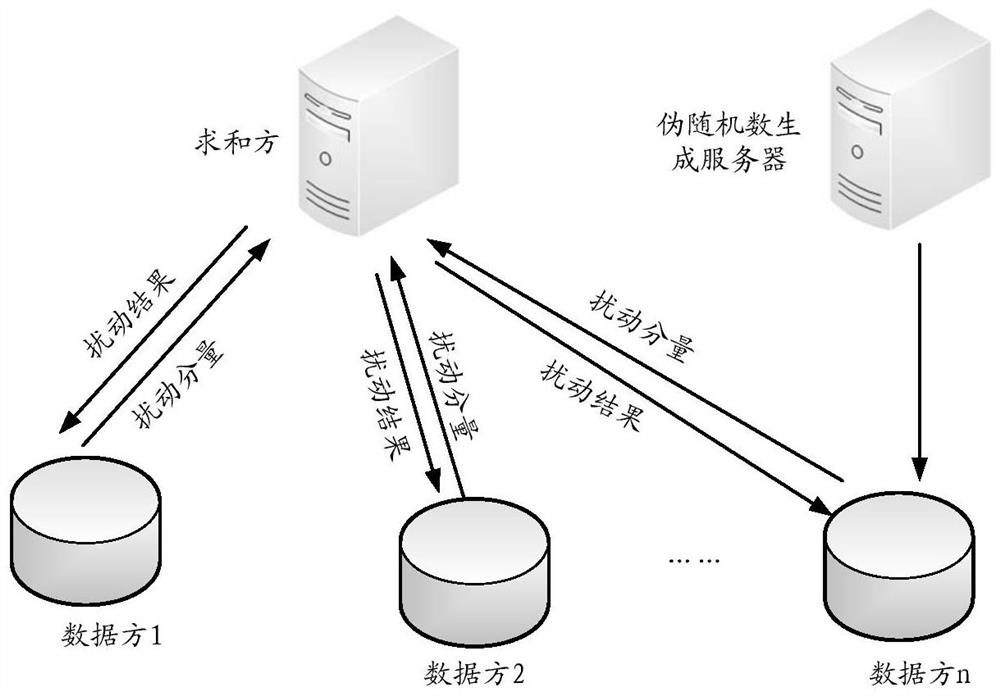
[0043] Secure computing in the form of sharing and sharing: computing in the form of maintaining and sharing. During the calculation process, one party can never deduce the part of each data saved by other parties, and the calculation results are still stored in the form of sharing and sharing.
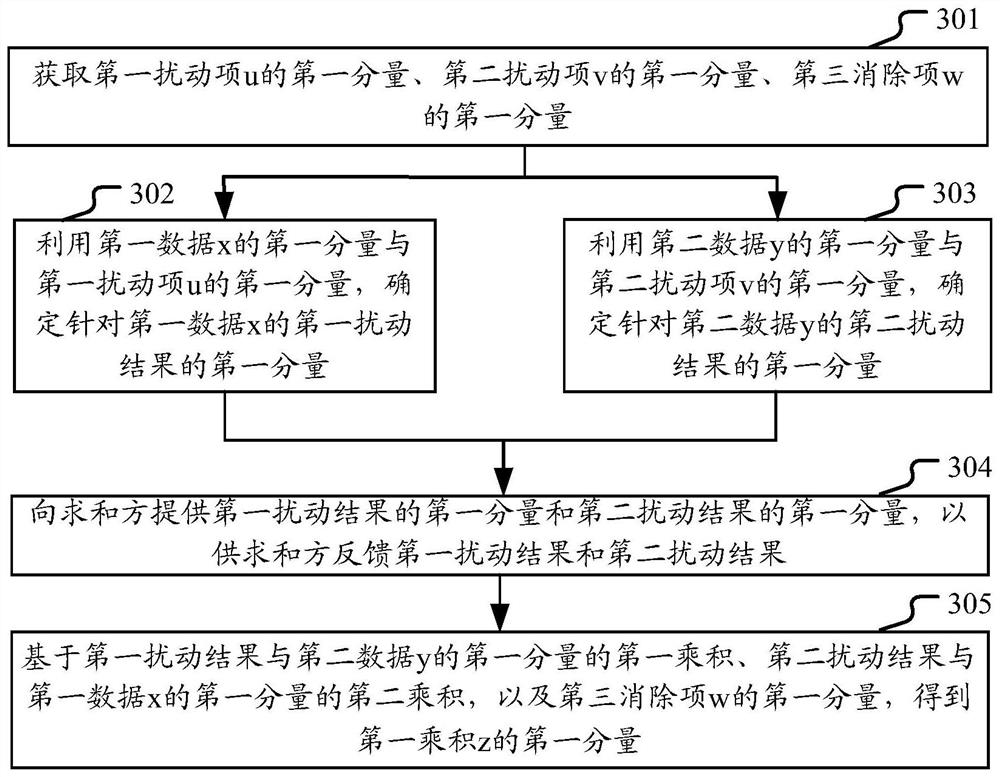
[0044] It can be understood that for the multiplication calculation performed by the two par...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com