Power grid line vulnerability analysis method based on HITS algorithm
An analysis method and vulnerability technology, applied in calculation, computer-aided design, electrical digital data processing, etc., can solve problems such as complex power grid structure, and achieve the effect of fast calculation speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] Below in conjunction with accompanying drawing, technical scheme of the present invention is further described:
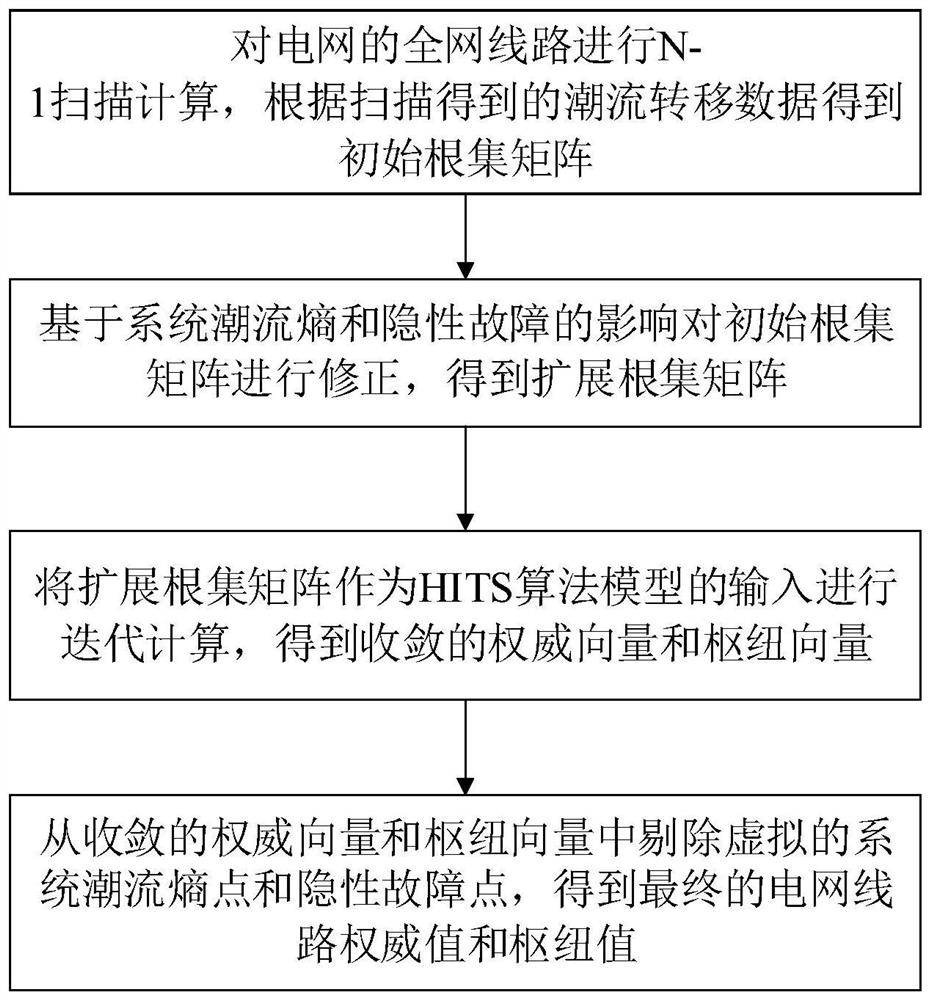
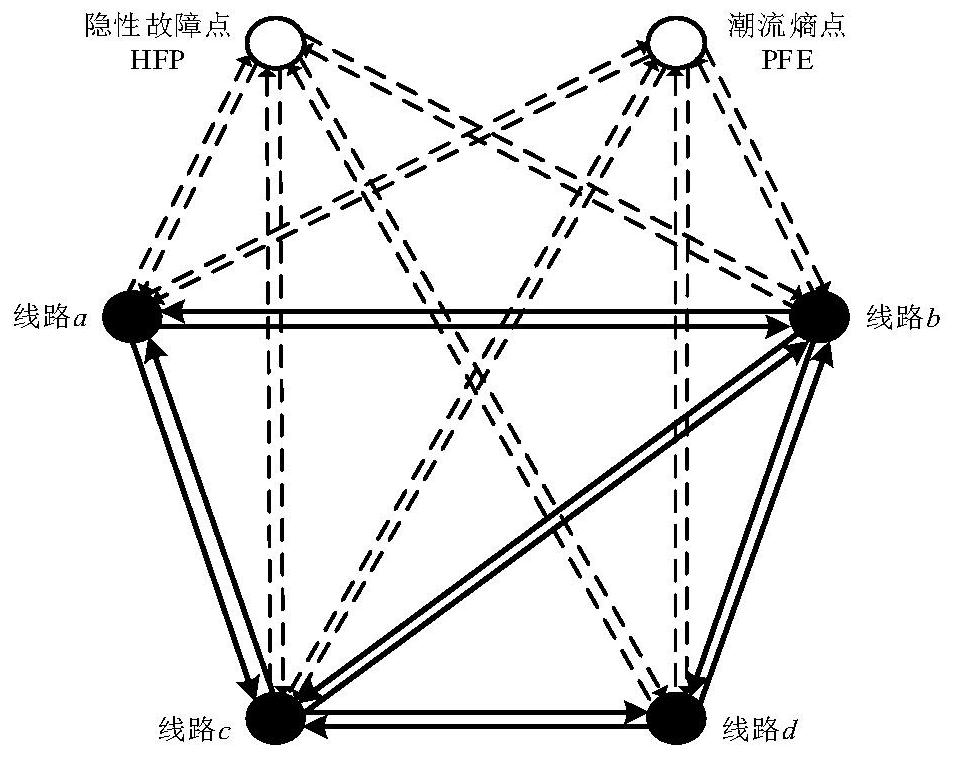
[0068] The present invention proposes a power grid line vulnerability analysis method based on HITS algorithm, such as figure 1 shown, including the following steps:
[0069] Step A: Perform N-1 scanning calculation on the entire network lines of the power grid, and obtain an initial root set matrix according to the power flow transfer data obtained by scanning.
[0070] Step A01, read the topology structure and system operation data of the power grid, carry out N-1 scanning calculation to the entire network line, obtain the power flow transfer data of the power grid, and form a power flow transfer matrix TP, and the expression of each element in the power flow transfer matrix TP is as follows;
[0071]
[0072] where ΔP ij Indicates the influence on line j after line i is disconnected in the power grid, P j i represents the active power transmitted o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com