Power distribution Internet of Things edge Internet of Things proxy network security protection method and system
A network security and Internet of Things technology, applied in the field of power distribution Internet of Things in the power Internet of Things, can solve problems such as power grid data leakage, Internet of Things management platform penetration attacks, tampering, etc., to improve security and privacy, and reduce illegal intrusions. probability, the effect of preventing leakage and tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
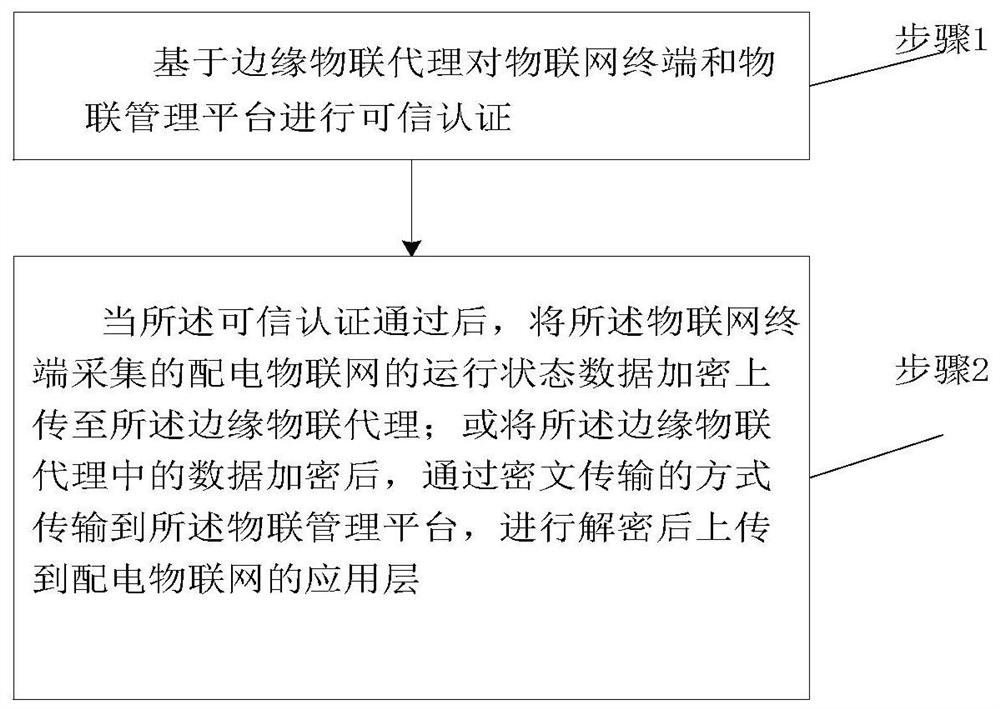
[0052] like figure 1 As shown, an embodiment of the present invention provides a network security protection method for an IoT agent at the edge of the power distribution IoT, including:
[0053] Step 1: Perform trusted authentication on the IoT terminal and the IoT management platform based on the edge IoT agent;
[0054] Step 2: After the trusted authentication is passed,
[0055] Encrypt and upload the operation status data of the power distribution IoT collected by the IoT terminal to the edge IoT agent; or encrypt the data in the edge IoT agent and transmit it to the edge IoT agent by means of ciphertext transmission. The IoT management platform is decrypted and uploaded to the application layer of the power distribution IoT.
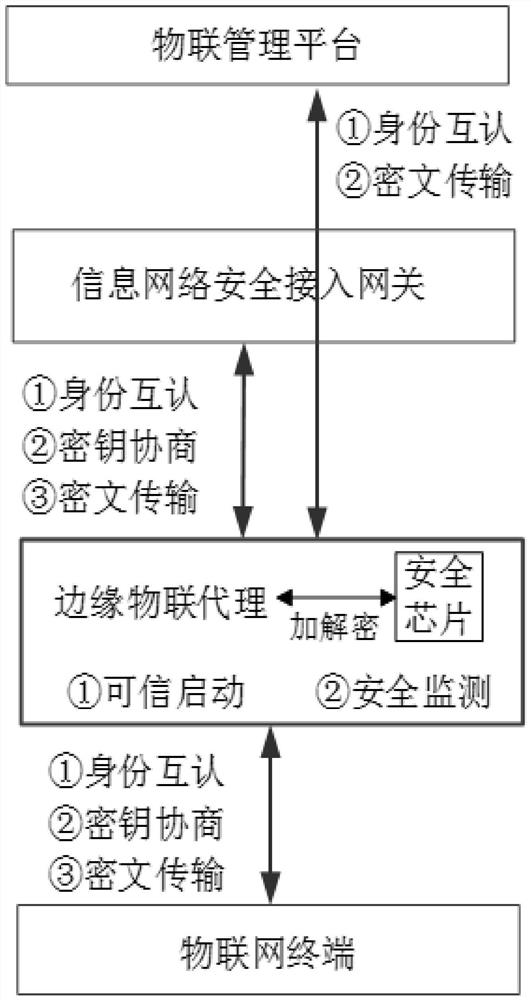
[0056] Combined with the security risks and requirements of the edge IoT agent, the security protection method in the present invention includes four aspects: edge IoT agent ontology security, access control, data protection, and security monitor...
Embodiment 2
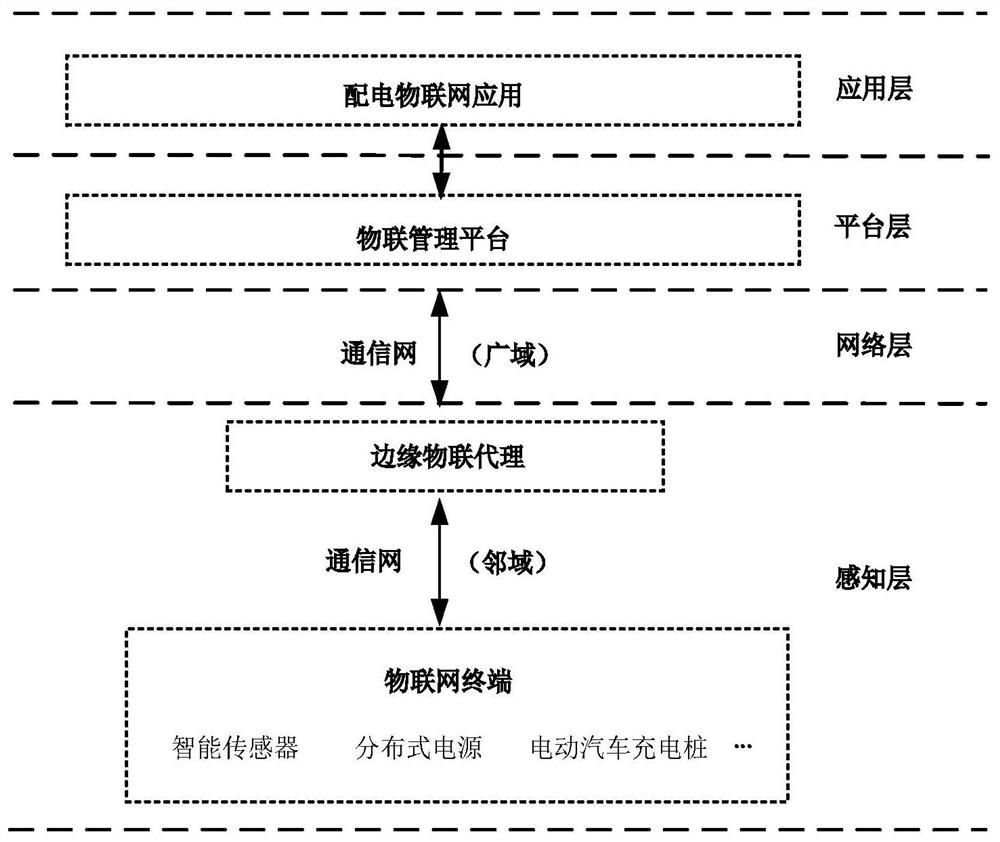
[0094] Based on the same inventive concept, the present invention also provides a network security protection system for the edge IoT agent of the power distribution IoT, because the principles of these systems for solving technical problems are similar to a security protection method for the edge IoT agent network of the power distribution IoT, The repetition will not be repeated. like Figure 7 shown, including:
[0095] The IoT terminal is used to collect the running status data of the power distribution IoT and upload it to the edge IoT agent;
[0096] The edge IoT agent is used for trusted authentication of IoT terminals and IoT management platforms; it is also used to receive the operating status data of the power distribution IoT collected by the encrypted IoT terminals; it is also used to encrypt the collected data Then, it is transmitted to the IoT management platform by means of ciphertext transmission;
[0097] The IoT management platform is used to decrypt the o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com