Cloud native state secret key management method
A technology of key management and management methods, which is applied in digital transmission systems, secure communication devices, electrical components, etc., can solve the problems of technical unified key centralized management, etc., to improve security and confidentiality, realize security protection, and facilitate unified maintenance sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, so that those skilled in the art may better understand the present invention and can be implemented, but the embodiments given are not intended as a qualification of the present invention.
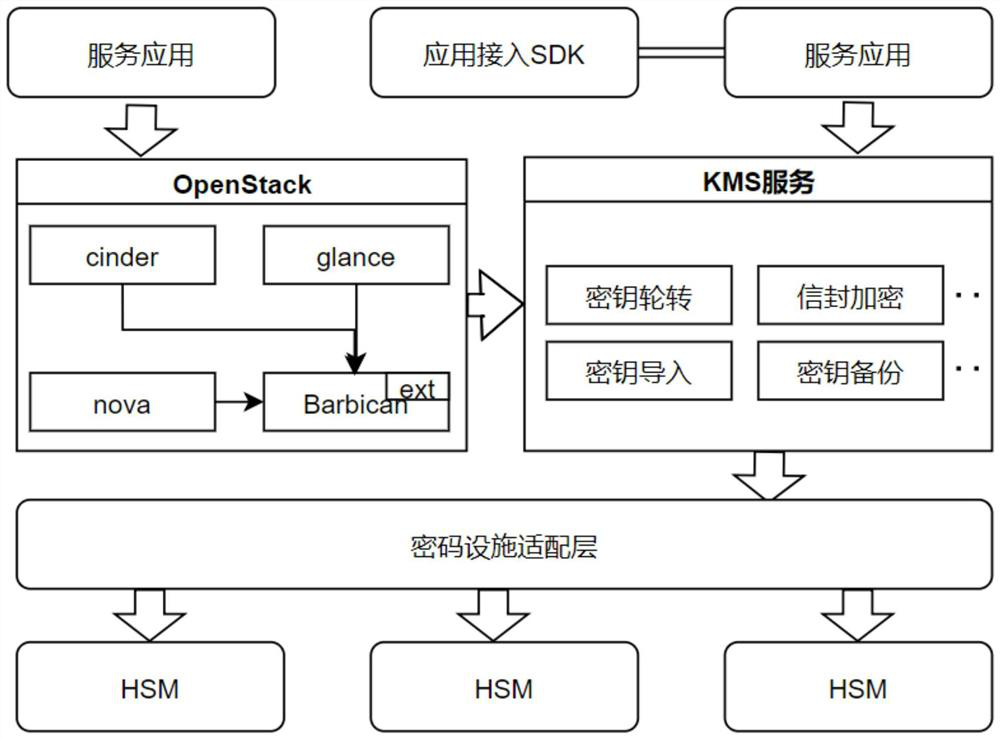
[0035] The present invention provides a cloud-native state secret key management method, comprising managing the key of the cloud platform and the key of the product on the cloud,
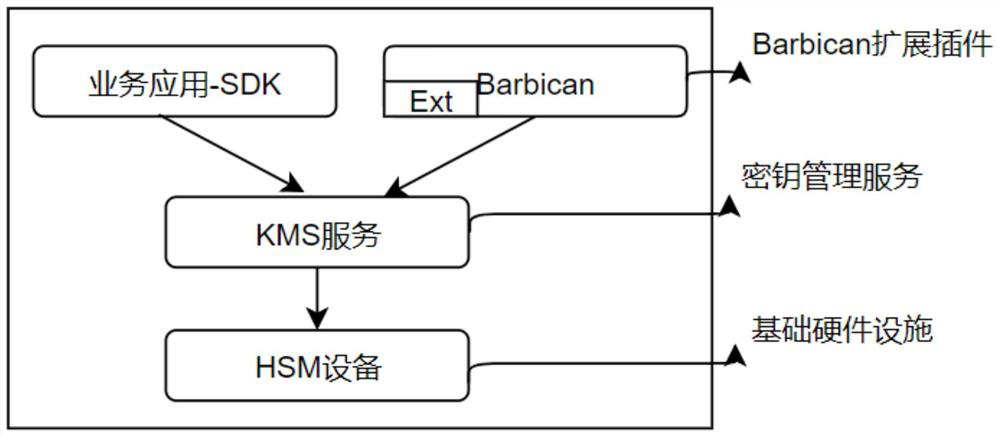
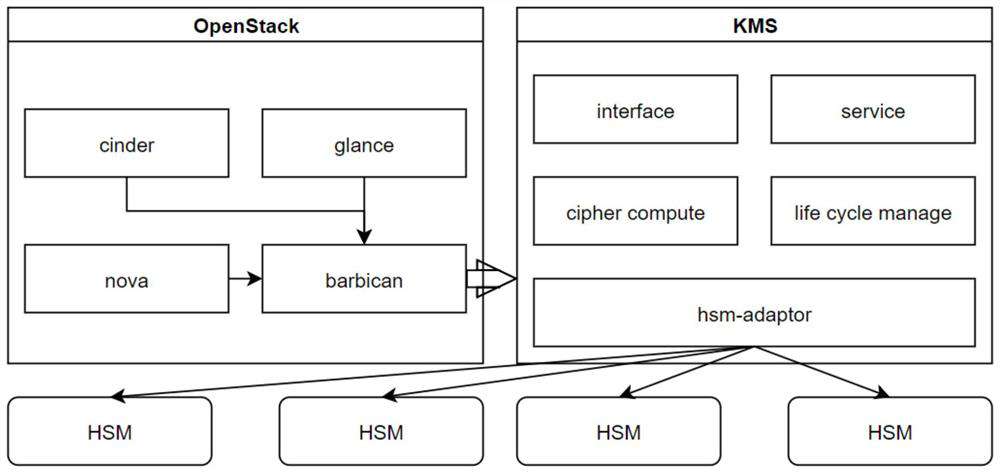
[0036] The key of the management cloud platform, comprising: according to the user's business request, calling the back-end service transposing the underlying node, calling the Barbican component through the underlying node, transposing the KMS service by using the Barbican extension plug-in through the Barbican component, completing the data mapping with the underlying hardware device and other internal processing through the KMS service, and transposing different hardware devices ad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com