Honeypot and sandbox mutually enhanced malicious program behavior processing method and system
A processing method and technology for malicious programs, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as no technical implementation, and achieve the effect of improving comprehensive performance, identification and compatibility capabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] This embodiment provides a method for processing malicious program behaviors in which honeypots and sandboxes reinforce each other;
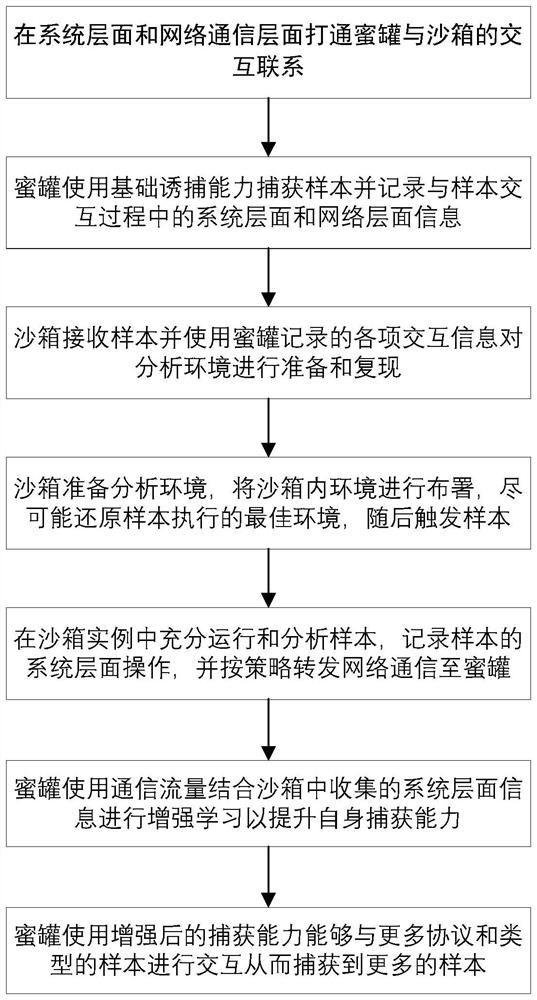
[0047] like figure 1 As shown, the honeypot and sandbox mutually enhance the malicious program behavior processing methods, including:
[0048] S101: establish a communication connection between the honeypot system and the sandbox system;
[0049] S102: the honeypot system induces and captures malicious codes;
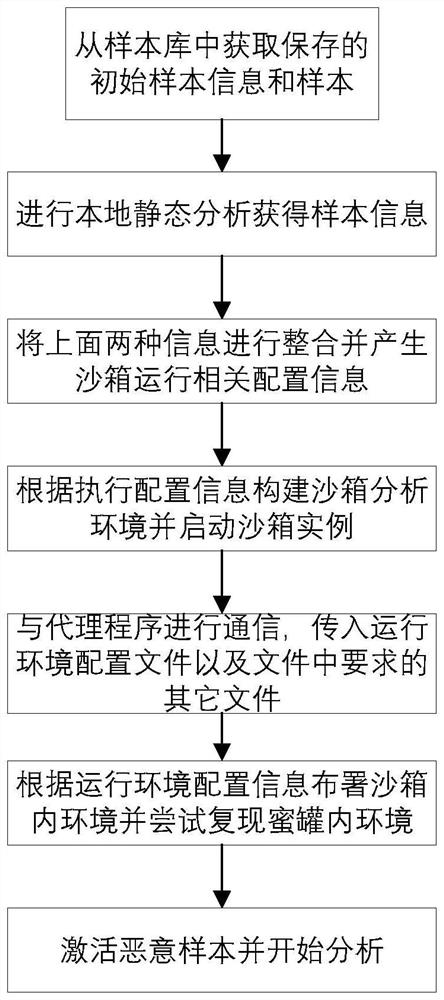
[0050] S103: The honeypot system sends the captured malicious code, the information on the interaction between the honeypot system and the malicious code, and the information generated during the capture process to the sandbox system; the sandbox system generates the execution of the malicious code based on the information passed by the honeypot system. Environment configuration file;
[0051] S104: The sandbox system generates a malicious code running environment according to the malicious code running environment configuratio...
Embodiment 2
[0153] Embodiment 2 This embodiment provides a malicious program behavior processing system in which honeypots and sandboxes reinforce each other;
[0154] A malicious program behavior processing system in which honeypots and sandboxes reinforce each other, including:
[0155] A communication connection module configured to: establish a communication connection between the honeypot system and the sandbox system;
[0156] The induction and capture module is configured to: induce and capture the malicious code by the honeypot system;
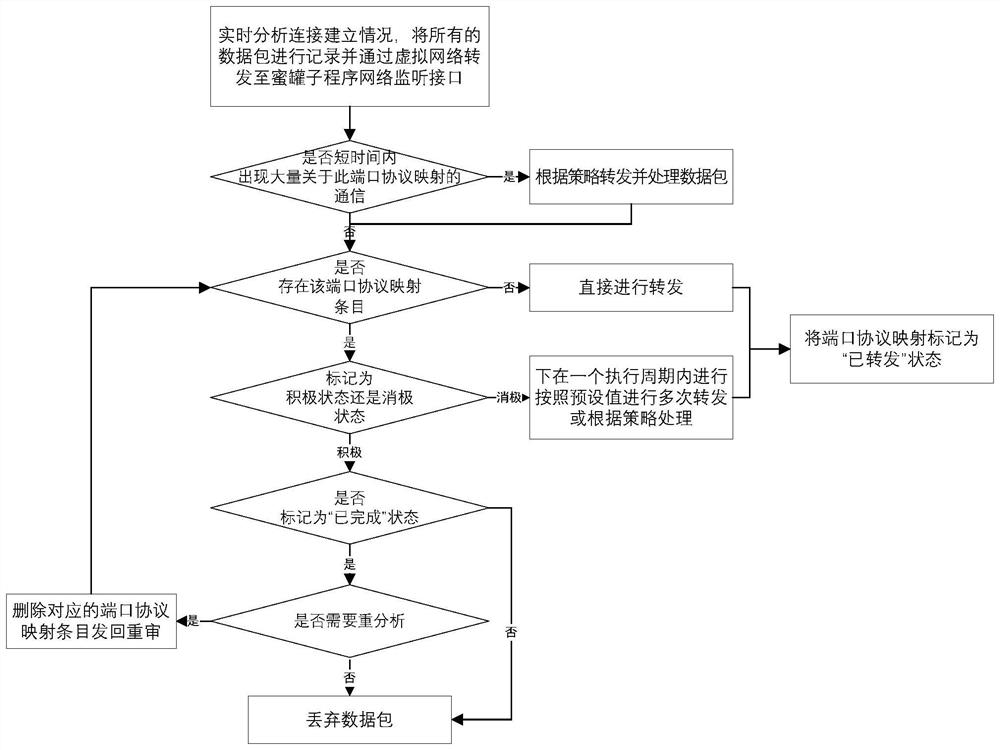
[0157] The configuration file generation module is configured as follows: the honeypot system sends the captured malicious code, the information on the interaction between the honeypot system and the malicious code, and the information generated during the capture process to the sandbox system; the sandbox system transmits it according to the honeypot system information to generate the operating environment configuration file for malicious code; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com