Rapid detection method for multi-dimensional vulnerability of hardware system
A hardware system and detection method technology, applied in the field of hardware security, can solve problems such as lack of system-level hardware vulnerability detection technology and method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
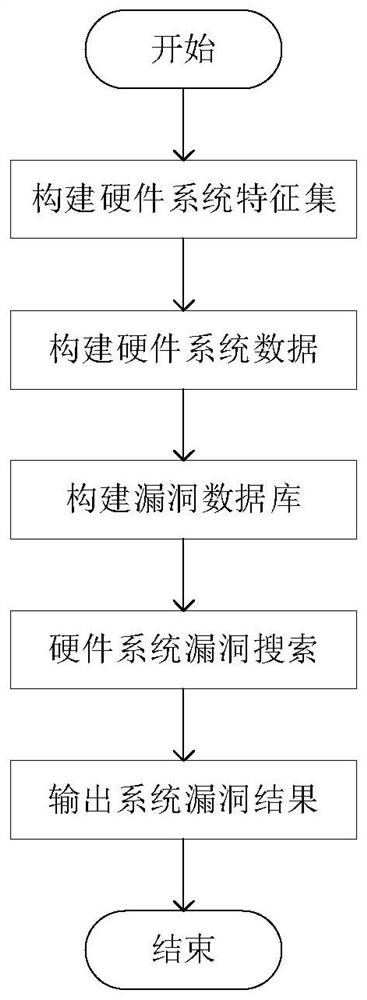
[0159] According to the content of the present invention, we selected several hardware systems from the cloud-pipe-end-terminal part of the IoT architecture, crawled the design information of all experimental hardware systems on the Internet, and constructed the design information of the hardware system through step 2 The data and experimental equipment are shown in Table 1.
[0160] Table 1 Experimental equipment information
[0161]
[0162]
[0163] Subsequently, through step 3, the vulnerability entries in the open source vulnerability database NVD are converted into vulnerability records, and a vulnerability database D is formed.
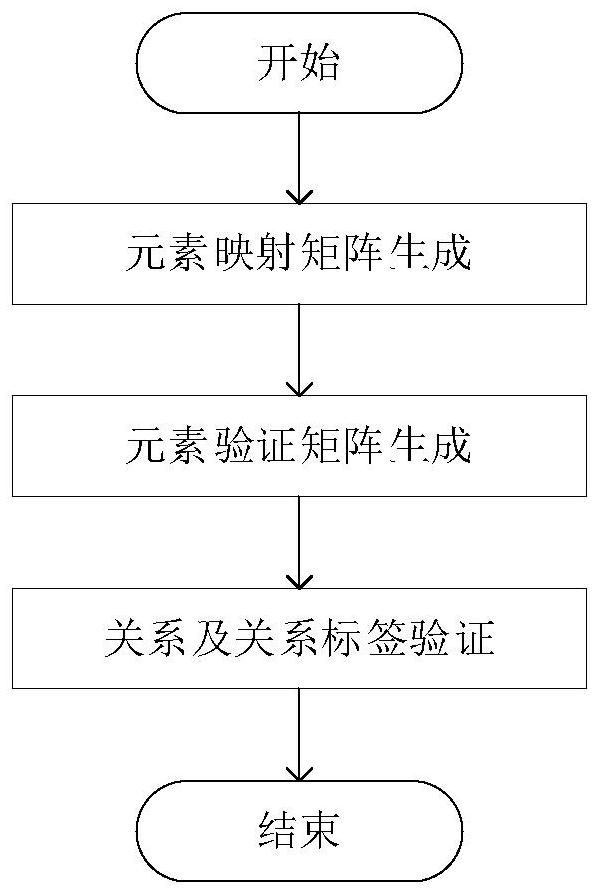
[0164] Finally, based on our defined vulnerability search algorithm, design data and vulnerability data, we conduct hardware system vulnerability detection. The search results are shown in Table 2.
[0165] As shown in Table 2, our method finds a total of 11 published vulnerabilities in the design information of 4 devices (Redmi Note4x, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com