Security and protection method and system based on multiple biological recognition technology
A technology of biometric identification and security, which is applied in the field of security methods and systems based on multiple biometric identification technologies, which can solve the problems of insufficient intelligence and accuracy of security, and the inability to accurately follow the security level, etc., to achieve the effect of improving the security effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
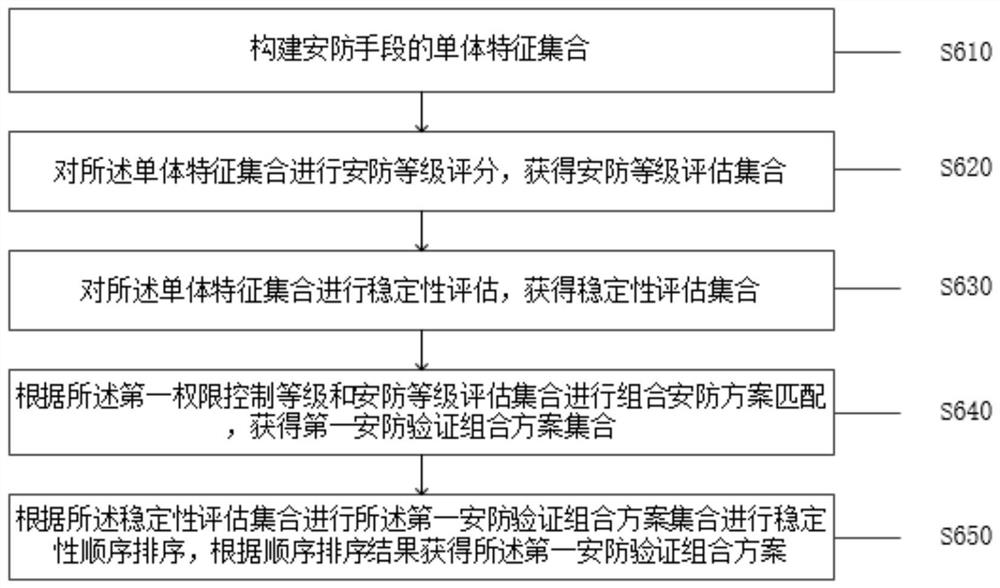
[0028] like figure 1 As shown, the present application provides a security method based on multiple biometric identification technologies, the method is applied to a security control system, and the method includes:
[0029] Step S100: obtaining current security level information, and obtaining a first security control scheme according to the security level information;
[0030] Step S200: Obtain the first authentication identification information of the first location, and match the first authentication user according to the first authentication identification information;
[0031] Specifically, the security control system is a system that performs overall security control, the security control system is connected to a plurality of security control devices in communication, and can perform security control of each security control device, and through the security control system, you can Real-time adjustment of the security level, according to the adjusted security level, upg...
Embodiment 2
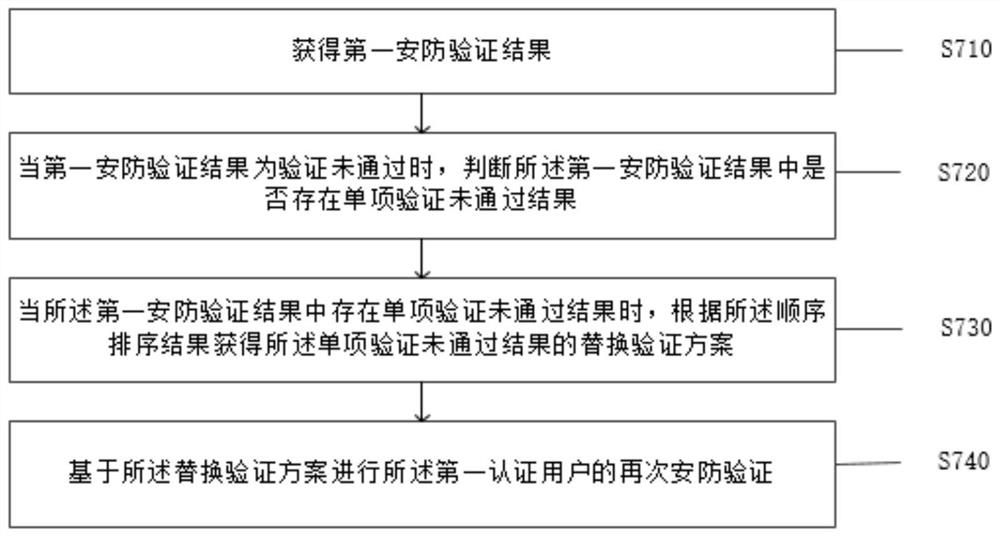
[0086] Based on the same inventive concept as the security method based on multiple biometric identification technologies in the foregoing embodiment, the present invention also provides a security protection system based on multiple biometric identification technologies, such as Figure 5 As shown, the system includes:
[0087] a first obtaining unit 11, the first obtaining unit 11 is configured to obtain current security level information, and obtain a first security control scheme according to the security level information;
[0088] a second obtaining unit 12, the second obtaining unit 12 is configured to obtain the first authentication identification information of the first location, and match the first authentication user according to the first authentication identification information;
[0089] a third obtaining unit 13, the third obtaining unit 13 is configured to obtain the first permission level of the first authenticated user according to the first security control...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com