Unmanned aerial vehicle attack prediction method and system based on bidirectional long-short-term memory model
A technology of long short-term memory and prediction method, applied in the field of network security, can solve the problems of data confidentiality, sensitivity and volatility, and protection difficulties, and achieve the effects of good performance, improved prediction accuracy, and privacy protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described in detail below in conjunction with the accompanying drawings, which are to explain rather than limit the present invention.
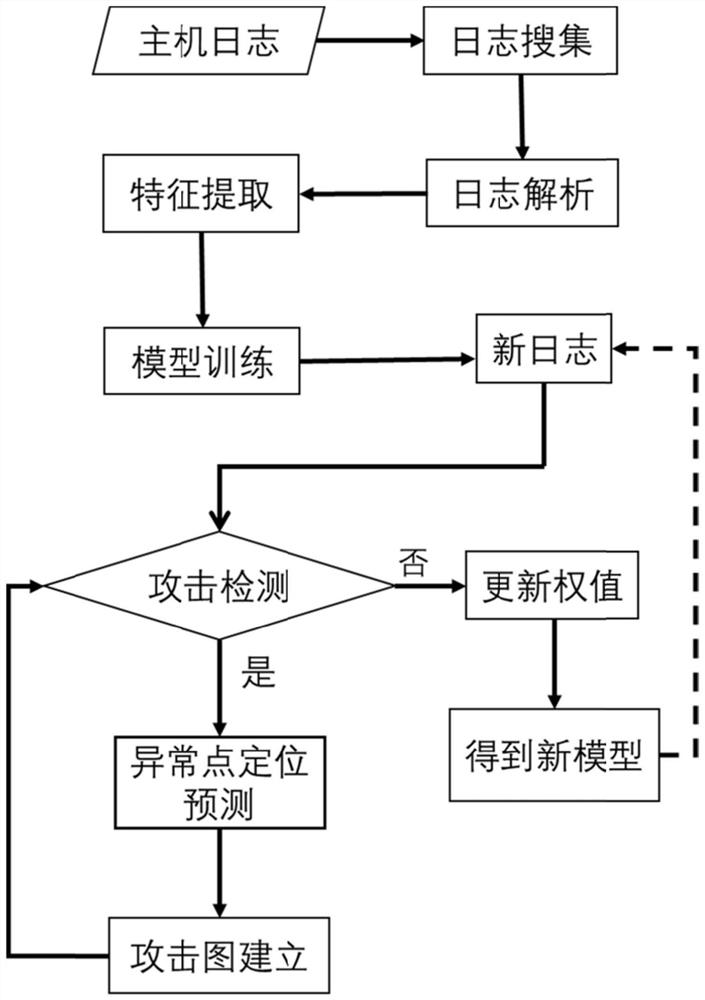
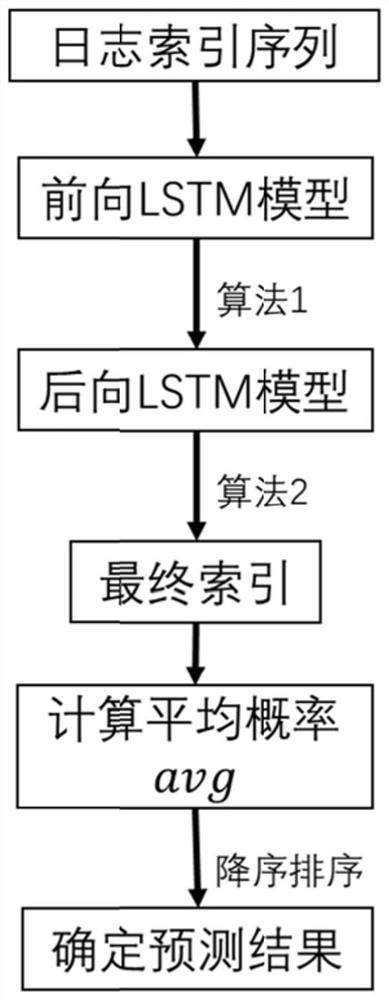
[0037] see Figure 1-3 , a UAV attack prediction method based on a bidirectional long short-term memory model, including the following steps:
[0038] Step 1: Train the encoder module of the Transformer model according to the constructed log semantic vector, and the trained encoder module is used to convert the log semantic vector into a log sequence vector output.
[0039] The encoder module in the Transformer model includes a multi-head attention layer and a feed-forward network layer (FFN). The feed-forward network layer consists of two ReLU activation layers. The training method of the encoder module is as follows:
[0040] S1.1. Obtain the UAV system log, delete the variables in the UAV system log and extract the log constant field, that is, the log template, and then vectorize the log templa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com