Urban planning domain block chain consensus verification method and system based on aggregation encryption
A technology for urban planning and verification methods, applied in user identity/authority verification, climate change adaptation, etc., can solve problems such as insufficient computing resources, and achieve the effect of reducing complexity and verification complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
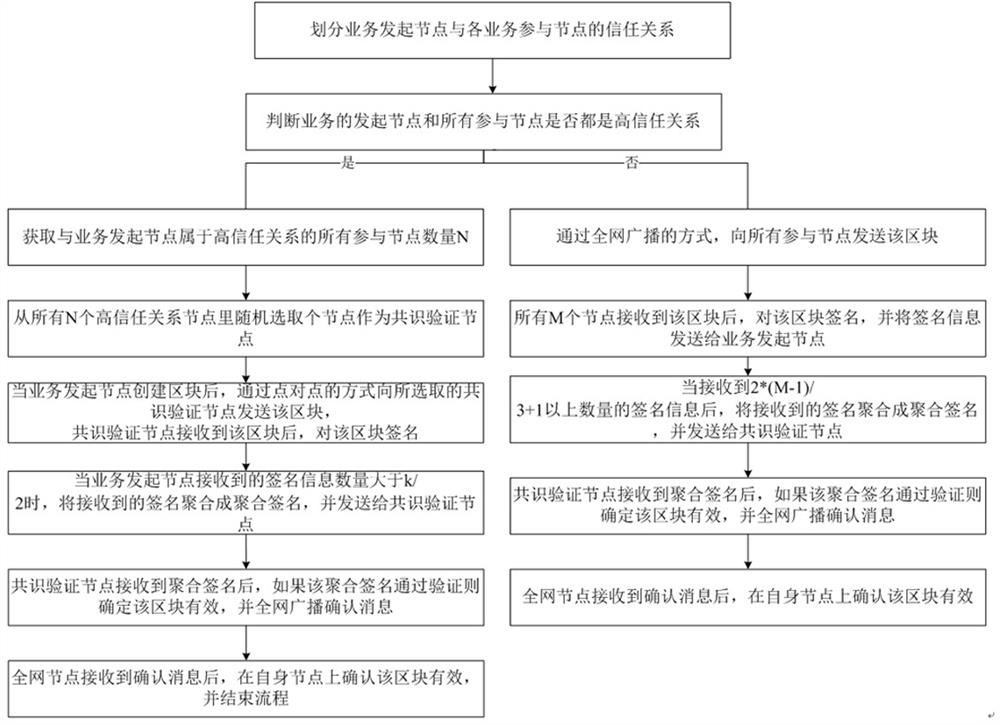
[0054] The specific steps of the first embodiment are as follows figure 1 shown, including:
[0055] Step 1: Divide the trust relationship between the service initiating node and each service participating node, namely high trust relationship and low trust relationship. The same group of initiating nodes and participating nodes can present different trust relationships in different services. The specific division rules are as follows:
[0056] (1) The internal nodes of the same subnet can be set to a high trust relationship, or the internal nodes belonging to the same functional department can be set to a high trust relationship; this is because the nodes within the same subnet or within a functional department are generally In a trusted environment, the possibility of malicious nodes appearing is very low;
[0057] (2) If they are all internal nodes, but do not belong to the same functional department or the same subnet, when jointly processing a business with a low level o...
Embodiment 2
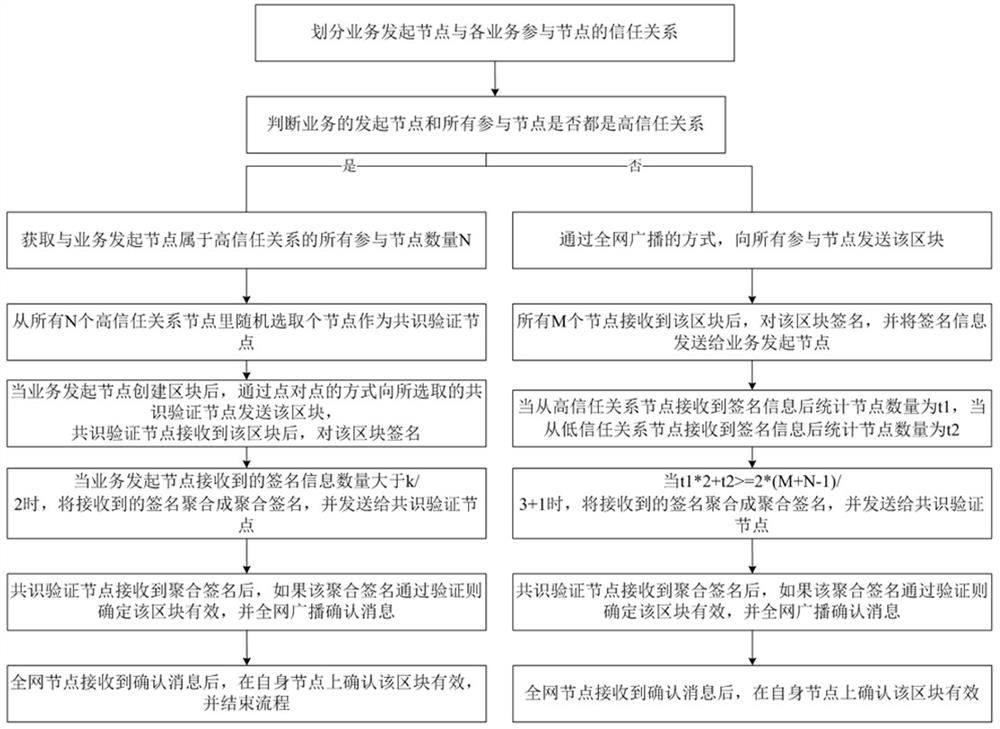
[0075] The concrete steps of embodiment two are as follows figure 2 shown, including:
[0076] Step 1: Divide the trust relationship between the service initiating node and each service participating node, namely high trust relationship and low trust relationship. The same group of initiating nodes and participating nodes can present different trust relationships in different services. The specific division rules are as follows:
[0077] (1) The internal nodes of the same subnet can be set to a high trust relationship, or the internal nodes belonging to the same functional department can be set to a high trust relationship; this is because the nodes within the same subnet or within a functional department are generally In a trusted environment, the possibility of malicious nodes appearing is very low;
[0078] (2) If they are all internal nodes, but do not belong to the same functional department or the same subnet, when jointly processing a business with a low level of con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com