Cloud computing data security processing system
A data processing and data security technology, applied in the field of data processing, can solve problems such as hidden dangers affecting data security, and achieve the effect of improving security, improving technical effects, and ensuring computing requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
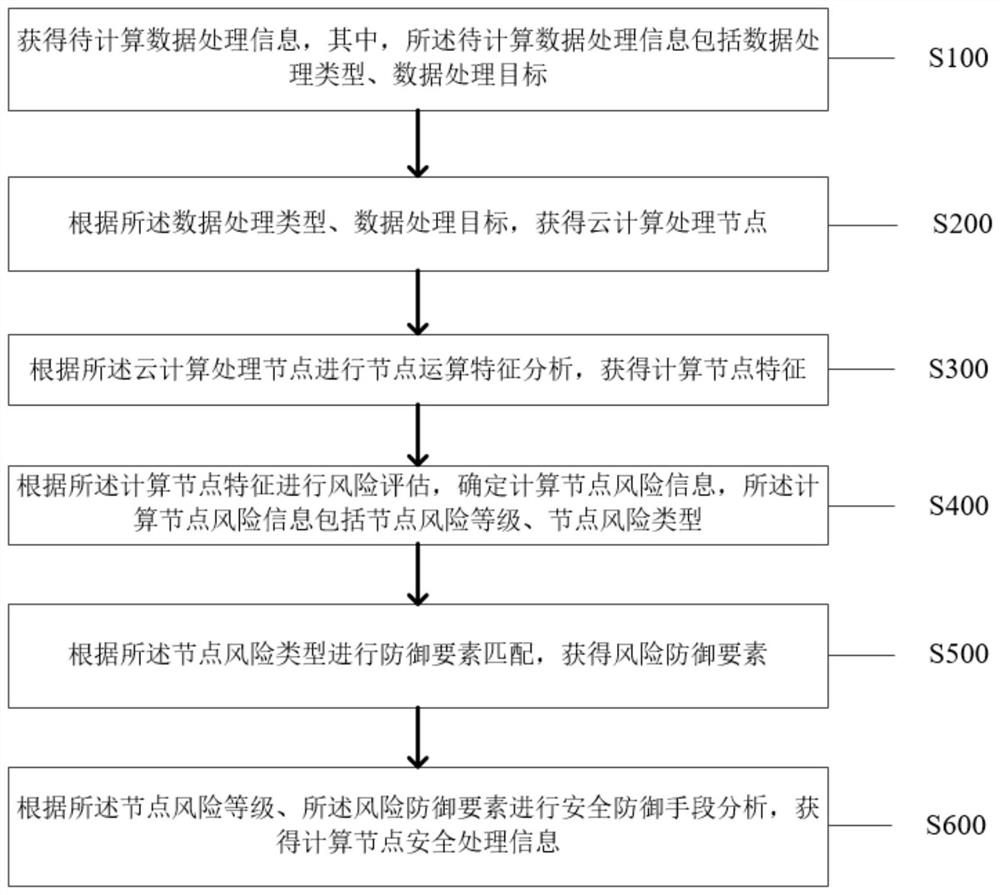
[0031] Please see attached figure 1 , an embodiment of the present application provides a cloud computing data security processing method, the method is applied to a cloud computing data security processing system, and the method includes:
[0032] Step S100: Obtain data processing information to be calculated, wherein the data processing information to be calculated includes a data processing type and a data processing target.
[0033] Specifically, the data processing information to be calculated includes the data information that needs to be processed currently, the data processing type, and the data processing target. The data information is the specific data content; the data processing type is the business feature that needs to be processed, that is, the specific processing Which operations are processed; the data processing targets are which cloud computing needs to be performed, and which cloud platforms and applets are to be transmitted and processed.
[0034] Step S...
Embodiment 2
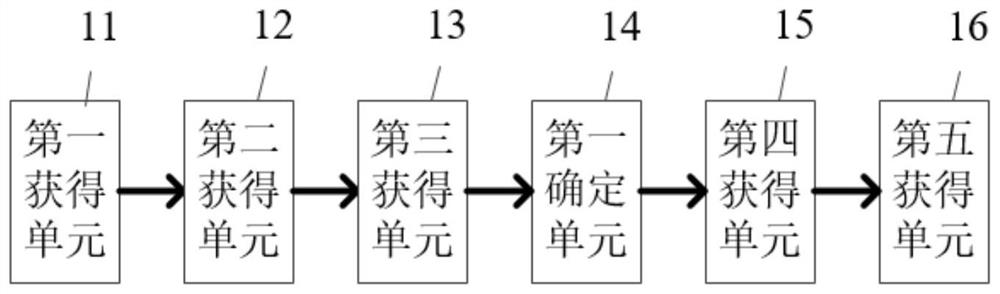
[0078] Based on the same inventive concept as the cloud computing data security processing method in the foregoing embodiment, the present invention also provides a cloud computing data security processing system, please refer to the appendix figure 2 , the system includes:
[0079] a first obtaining unit 11, the first obtaining unit 11 is configured to obtain data processing information to be calculated, wherein the data processing information to be calculated includes a data processing type and a data processing target;
[0080] a second obtaining unit 12, the second obtaining unit 12 is configured to obtain a cloud computing processing node according to the data processing type and data processing target;
[0081] The third obtaining unit 13, the third obtaining unit 13 is configured to perform node operation feature analysis according to the cloud computing processing node, and obtain the computing node feature;
[0082] a first determining unit 14, the first determining...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com