Dynamic deletion encryption system
An encryption system and dynamic technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as insufficient security performance, and achieve the effect of increasing the difficulty of cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
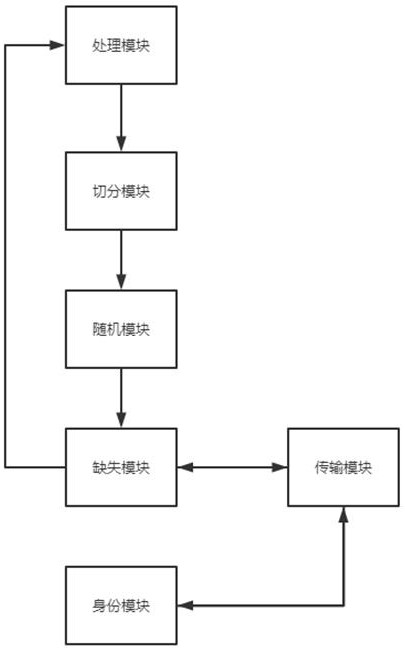
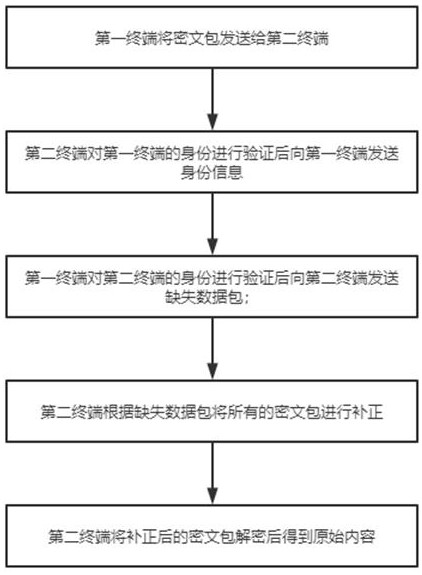
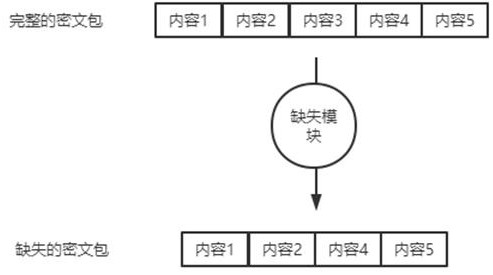
[0036] This embodiment provides a dynamic deletion encryption system, which combines figure 1 , including a processing module, a segmentation module, a random module, a missing module, a transmission module and an identity module, the processing module is used to encrypt the plaintext to obtain the ciphertext and decrypt the ciphertext to obtain the plaintext, the segmentation module It is used to segment the ciphertext to obtain several ordered ciphertext packets, the random module is used to generate a series of random number sequences, and the missing module extracts the corresponding ciphertext packets from the ciphertext packets according to the random number sequence. content, the missing module constructs the extracted content and the random number sequence into missing data packets, the transmission module is used to transmit data between two terminals containing the system, the identity module is used to The transmitted terminal is authenticated;
[0037] combine f...
Embodiment 2
[0056] This embodiment includes all the content in the first embodiment, and provides a dynamic missing encryption system, including a processing module, a segmentation module, a random module, a missing module, a transmission module, and an identity module. The processing module is used to encrypt the plaintext Perform encryption processing to obtain ciphertext and decrypt the ciphertext to obtain plaintext, the segmentation module is used to segment the ciphertext to obtain several ordered ciphertext packets, and the random module is used to generate a series of random Sequence of numbers, the number in the sequence is the same as the number of the ciphertext packets, the missing module extracts the corresponding content from the ciphertext packets according to the random number sequence, and the missing module will extract the content and the random number sequence is constructed into a missing data packet, the transmission module is used to transmit data between two termina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com