Communication encryption method and device of SE chip and storage medium
An encryption method and chip technology, applied in the field of Internet of Things, can solve problems such as loss of corporate and national interests, and achieve the effects of enhancing security, occupying less resources, and increasing the difficulty of deciphering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
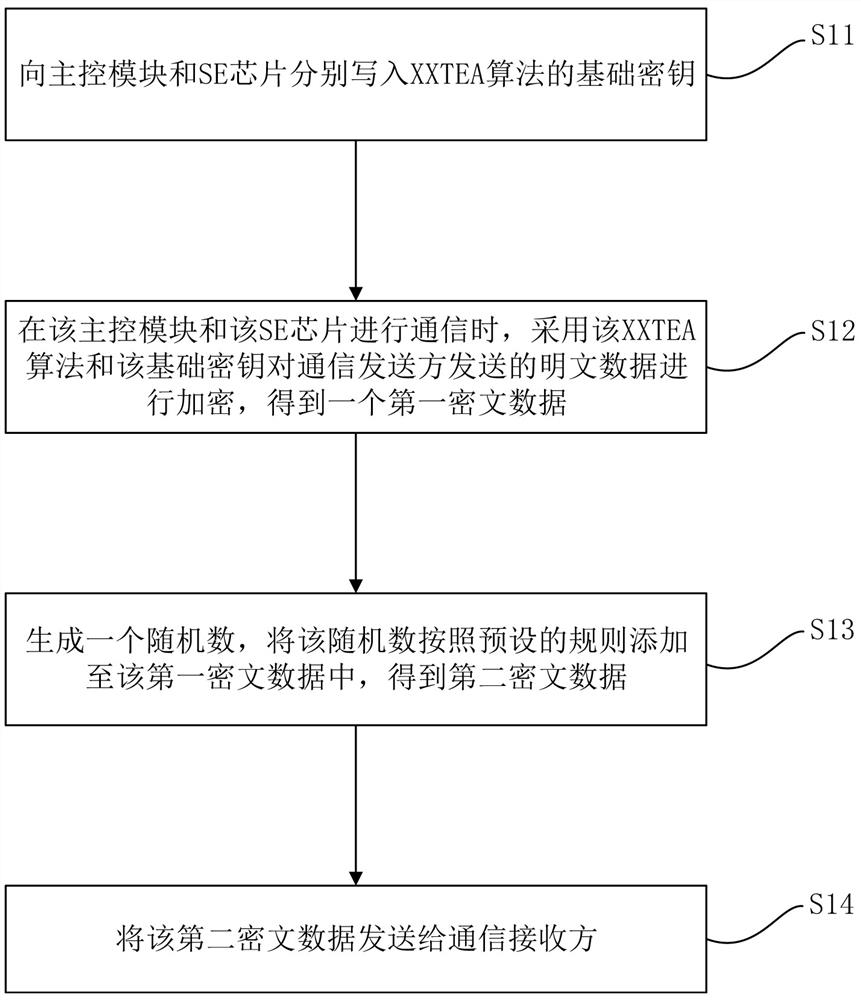
[0033] see figure 2 , figure 2 It is a schematic flowchart of an embodiment of the communication encryption method of the SE chip of the present invention. like figure 2 As shown, the method includes the steps:
[0034] S11: Write the basic key of the XXTEA algorithm to the main control module and the SE chip respectively;
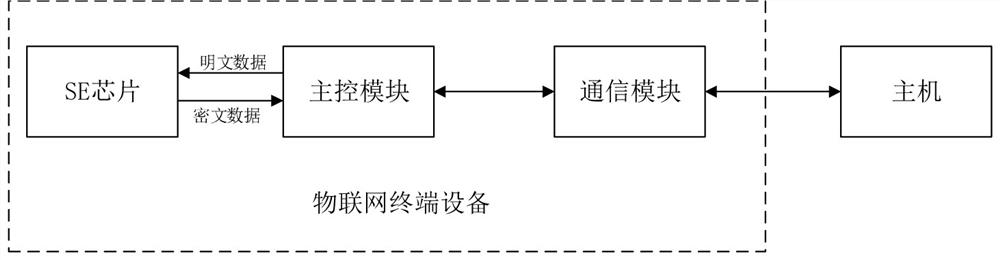
[0035] In step S11, the SE chip is set on the IoT terminal device.
[0036] Preferably, before the product leaves the factory, the basic key is written into the main control module and the SE chip respectively. That is to say, only the manufacturer of the terminal device knows the basic key, and other personnel cannot know the basic key.
[0037] S12: when the main control module communicates with the SE chip, use the XXTEA algorithm and the basic key to encrypt the plaintext data sent by the communication sender to obtain a first ciphertext data;
[0038] In step S12, since the XXTEA algorithm encrypts the 64-bit data block as a unit, the plainte...
Embodiment 2
[0050] see Figure 4 , Figure 4 It is a schematic flowchart of an embodiment of the communication encryption method of the SE chip of the present invention. like Figure 4 As shown, steps S21 to S23 of the method are the same as figure 2 Steps S11~S13 are the same, and step S25 is the same as figure 2 is the same as step S14, the method is the same as figure 2 The difference is that there are also steps:
[0051] S24: Perform an exclusive OR operation on the second ciphertext data, and convert the second ciphertext data into third ciphertext data.
[0052] In step S24, the method of performing the XOR operation on the second ciphertext data may be: Next, taking the example of the first embodiment as an example, the data of the second ciphertext data with a length of 16 bytes is denoted as A 1 B 1 A 2 B 2 A 3 B 3 A 4 B 4 A 5 B 5 A 6 B 6 A 7 B 7 A 8 B 8 , the A 1 and B 1 XOR the A 1 and B 1 The XORed value is placed in B 1 position, the B 1 and A ...
Embodiment 3
[0056] see Figure 5 , Figure 5 It is a schematic flowchart of another embodiment of the communication encryption method of the SE chip of the present invention. like Figure 5 As shown, steps S31 to S34 of the method are the same as figure 2 The steps S11~S14 are the same, the method is the same as figure 2 The difference is that there are also steps:
[0057] S35: Decrypt the second ciphertext data at the communication receiver;
[0058] In step S35, it can be understood that the communication receiver has the basic key of the XXTEA algorithm, so the second ciphertext data can be decrypted at the communication receiver to obtain plaintext data.
[0059] S36: If the decryption fails, count the number of decryption failures;
[0060] In step S36, if the second ciphertext data is tampered with other forms of data due to human intervention, the data decrypted in step S35 does not conform to the format of plaintext data, or the second ciphertext data cannot be obtained b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com