Updating network encrypted pins method
A key code, encrypted technology, applied in the field of updating the wireless network encryption key code, can solve the problems of key code leakage, spending a lot of time, inefficiency, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
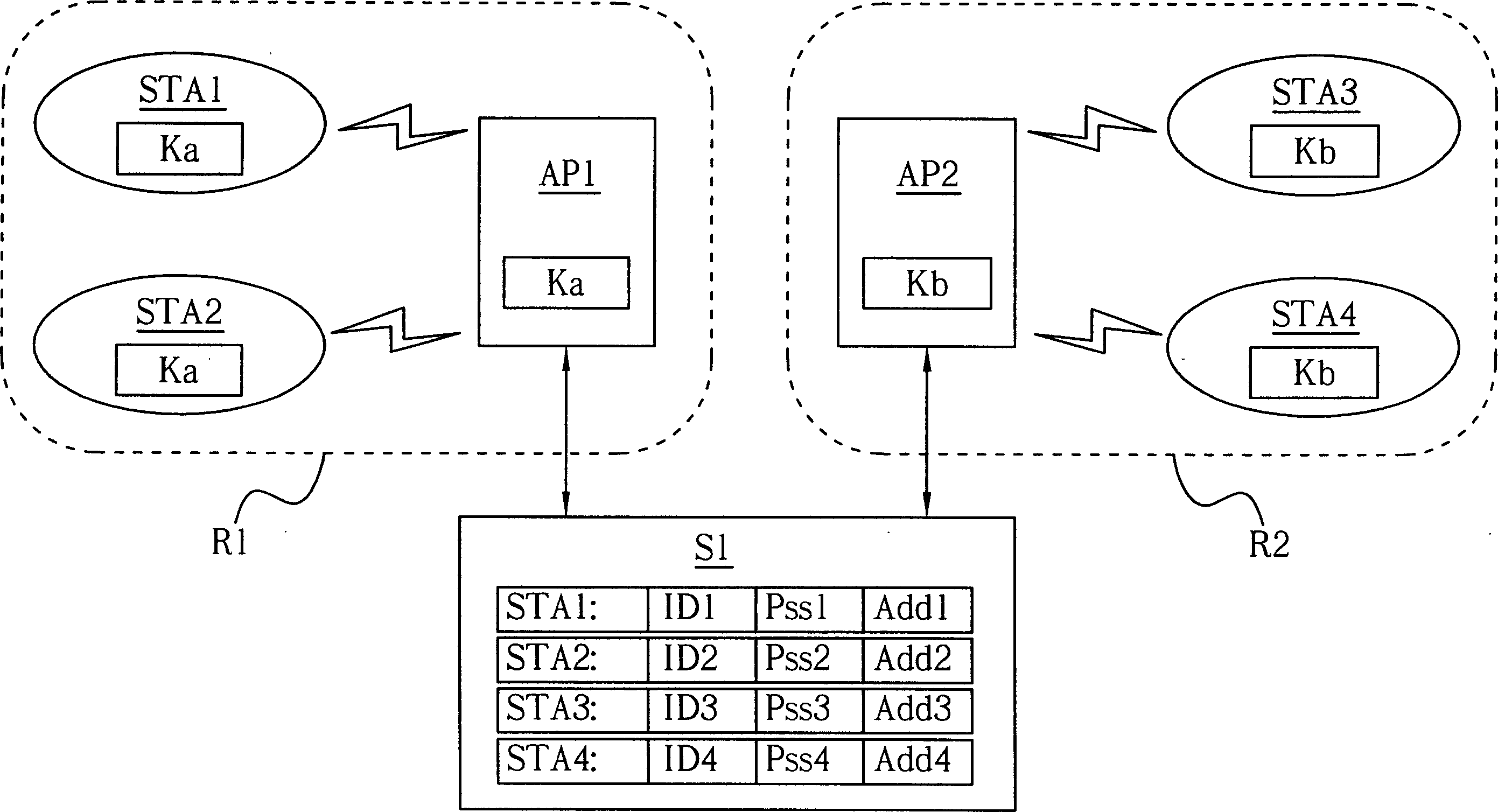
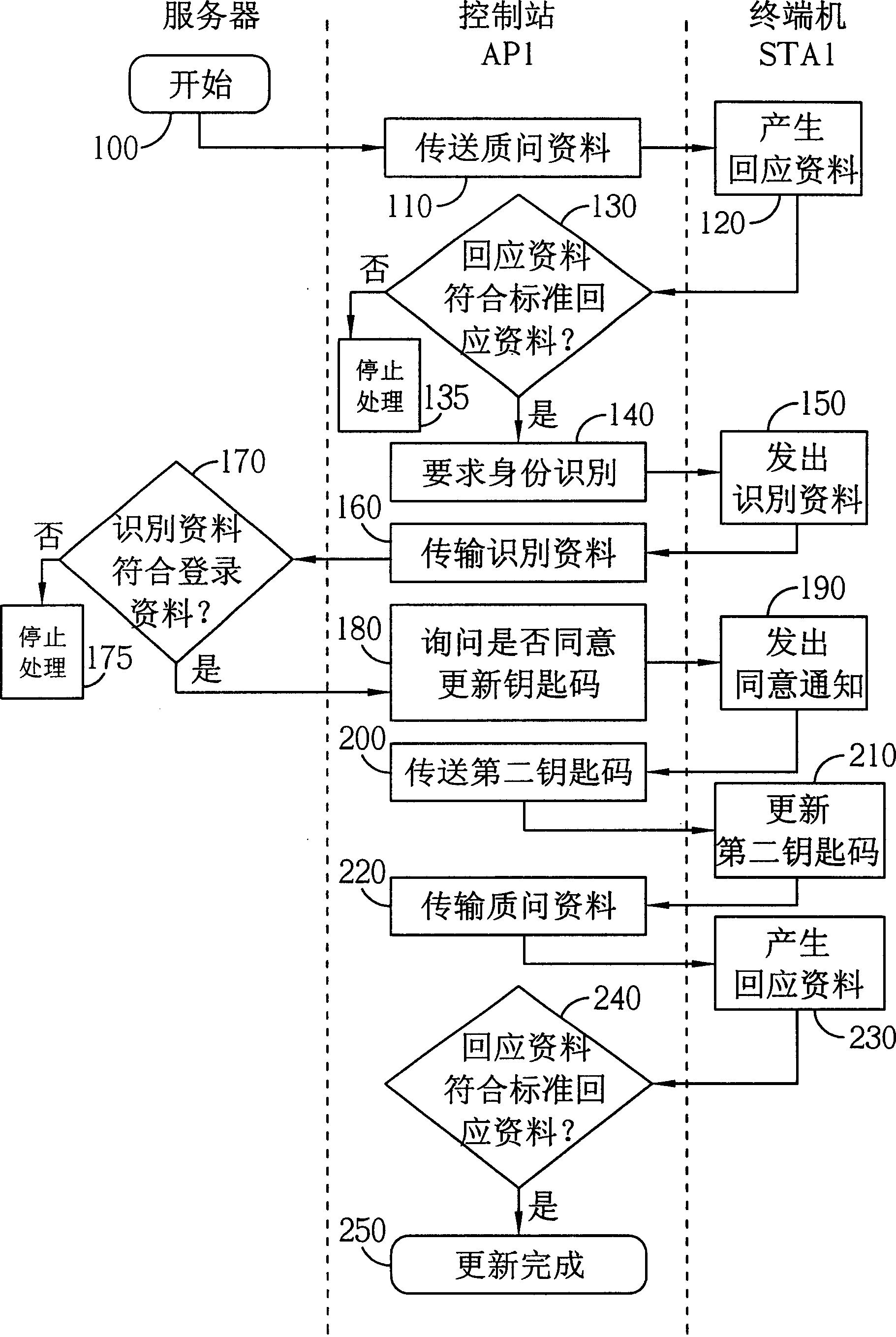
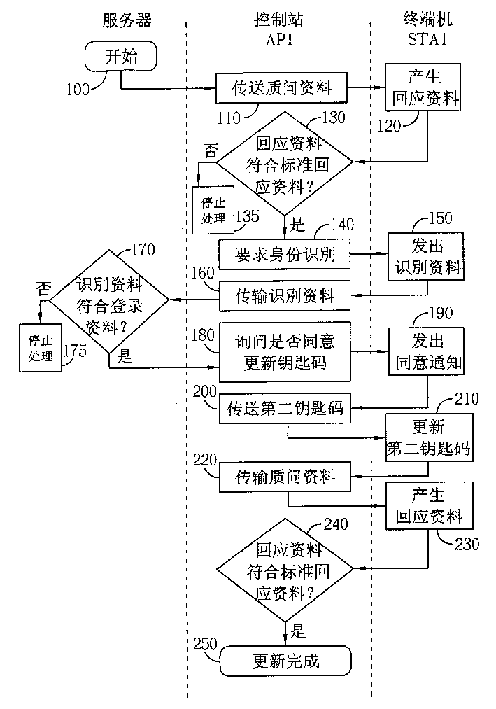
[0010] The main spirit of the present invention is to use the wireless network itself to update the key code used in Wired Equivalent Privacy (WEP), which can be widely used in figure 1 A typical wireless network; the terminal can be a portable computer such as a personal computer or a notebook computer. The following will be figure 2 The following flow chart is used to illustrate the steps performed by the present invention when updating the key code of a terminal. Please refer to figure 2 . figure 2 It is a schematic flow chart of the present invention; the three columns from left to right respectively represent the steps performed by the server, the control station and the terminal. The following assumes that the object to update the key code is figure 1 The terminal STA1 in the terminal (so its corresponding control station is AP1); assuming that the first key code is already stored in the terminal STA1, it needs to be updated to the second key code to update the wi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com