A private key acquiring method for use in set-top box
An acquisition method and a set-top box technology, which are applied in the field of Internet key use and its secure transmission, can solve the problems of cumbersome process, high cost, and high production cost of smart cards, and achieve the effect of high privacy performance and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
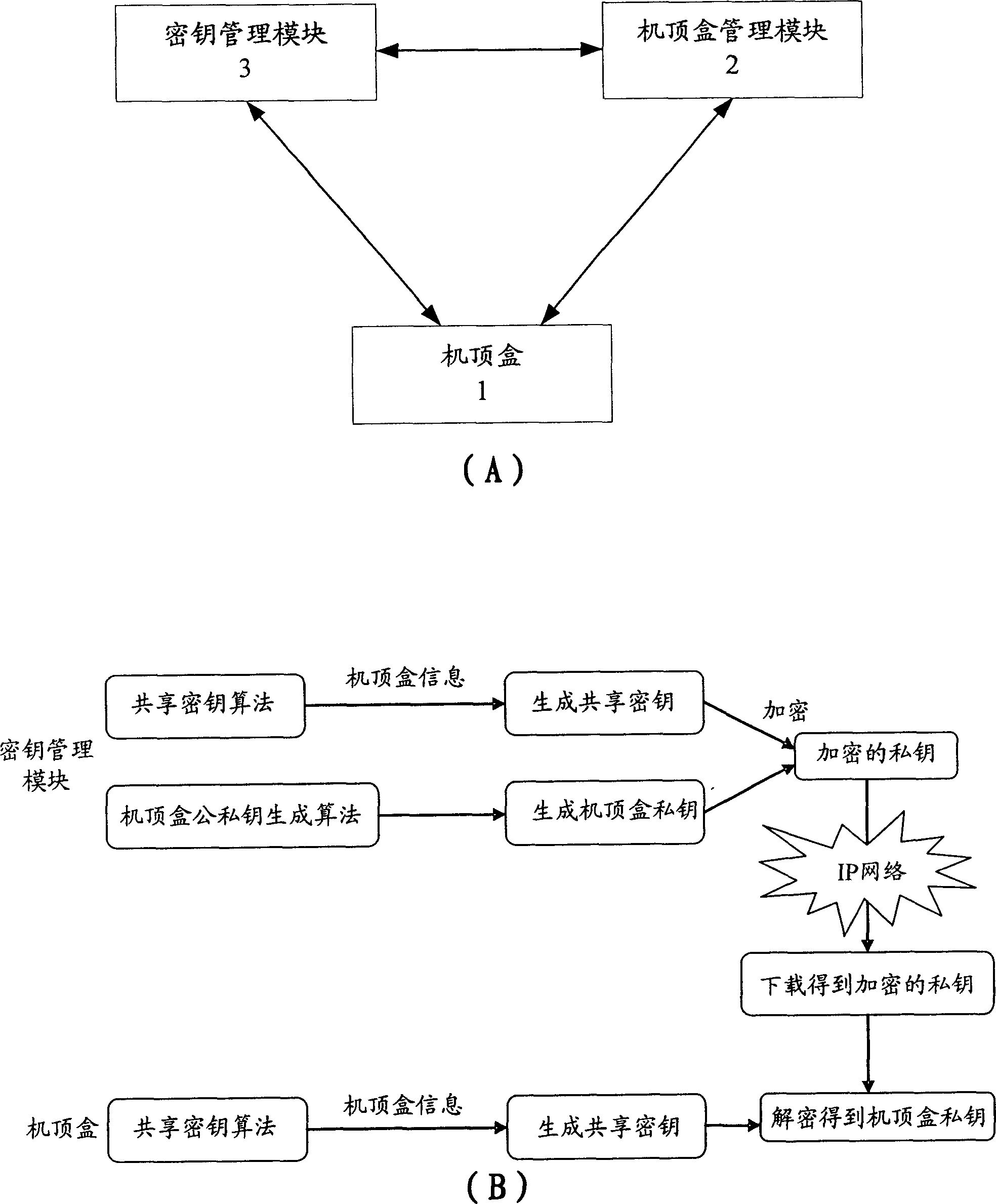
[0053] see image 3 , the present invention is a method for obtaining a private key used in a set-top box, and its applicable network system includes at least the following three functional components that are connected to each other to form a mutual information transmission channel:
[0054] Set-top box 1 is a client device that plays video and / or audio programs. During the account opening operation, it obtains software containing the latest calculation shared key algorithm, so as to use this algorithm to calculate and generate a shared key based on its own set-top box software and hardware information. key, and then use the shared key to decrypt the downloaded encrypted private key, and then use the private key to decrypt the content key, and then use the conten...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com