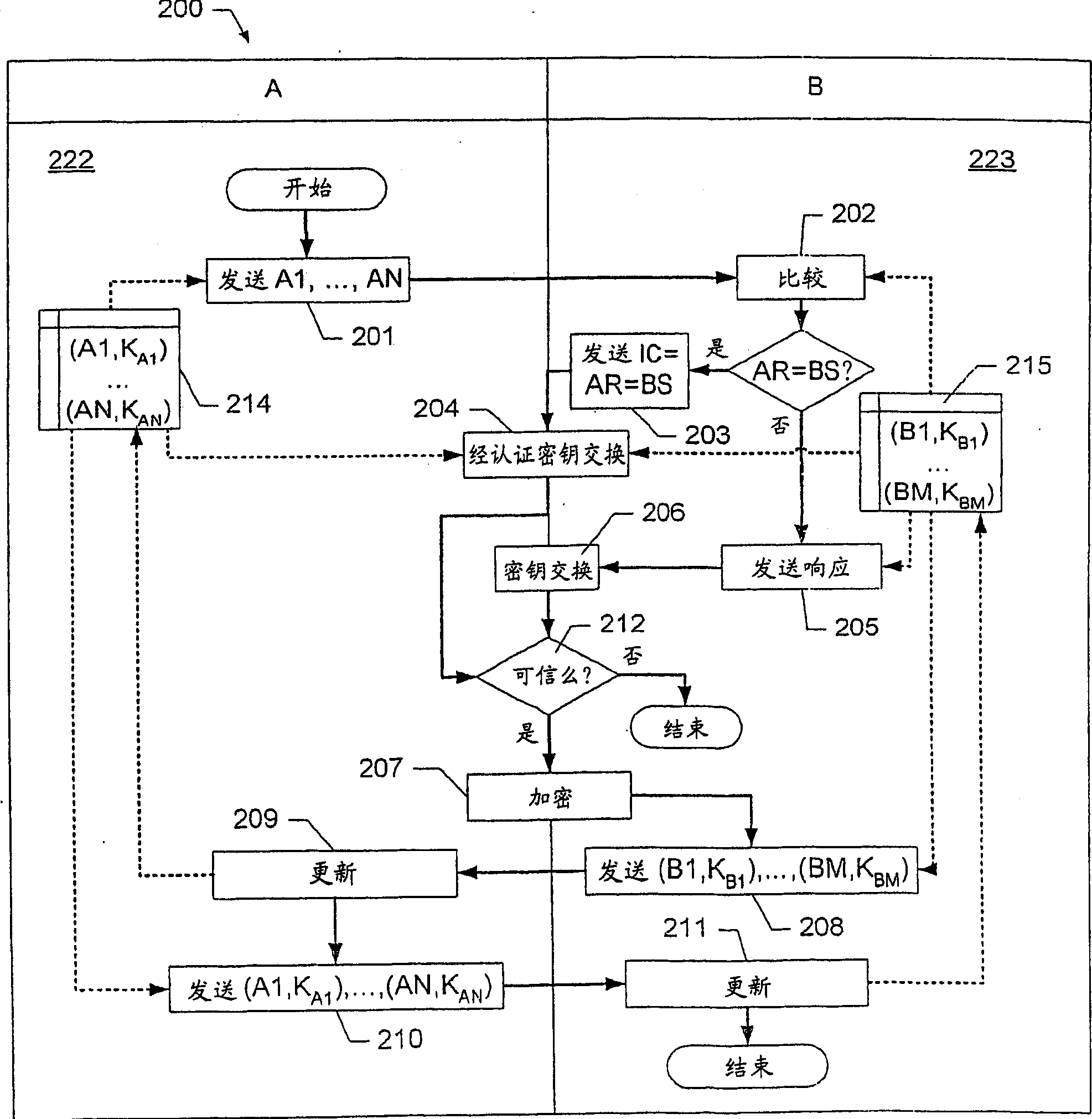
Security in a communications network
A technology of communication equipment and security association, which is applied in the field of communication to achieve the effect of a simple user interface
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
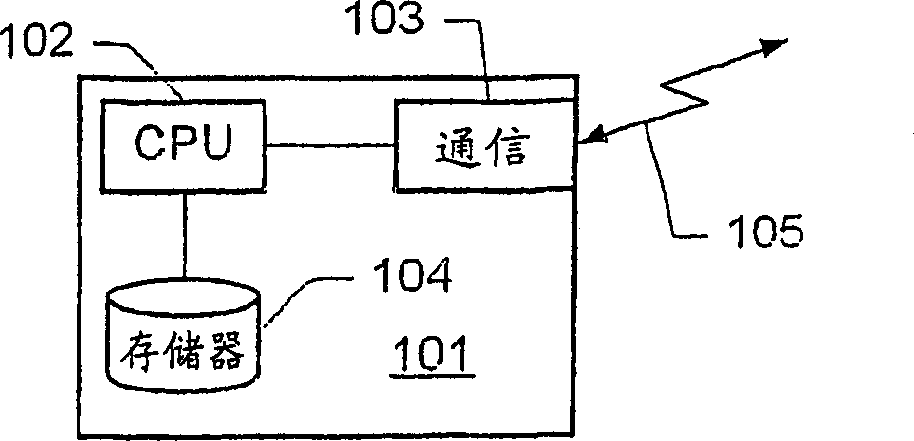
[0053] figure 1 A block diagram of a communication device is shown. The communication device 101 comprises a processing unit 102, a radio communication unit 103 connected to the processing unit, and a storage medium 104 connected to the processing unit.
[0054] The radio communication unit 103 transmits data received from the processing unit 102 via the radio channel 105 employed by the communication network, receives data from the radio channel, and forwards the data to the processing unit. For example, the radio communication unit 103 may be based on Bluetooth technology and transmit / receive within the ISM frequency band of 2.45 GHz. In one embodiment, the communication network is a Bluetooth piconet.
[0055] The processing unit 102 processes data received from other devices and data to be sent to other devices according to functions implemented by the communication device. In particular, the processing unit may be suitably programmed to perform security functions such ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com