Distributed trust management system and method for obtaining distributed credential chain
A technology of trust management and trust certificate, applied in transmission systems, electrical components, etc., can solve the problems of insufficient attribute constraint support, insufficient attribute information support, affecting system availability and performance, etc., to strengthen information security, enhance description ability, The effect of enhancing flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
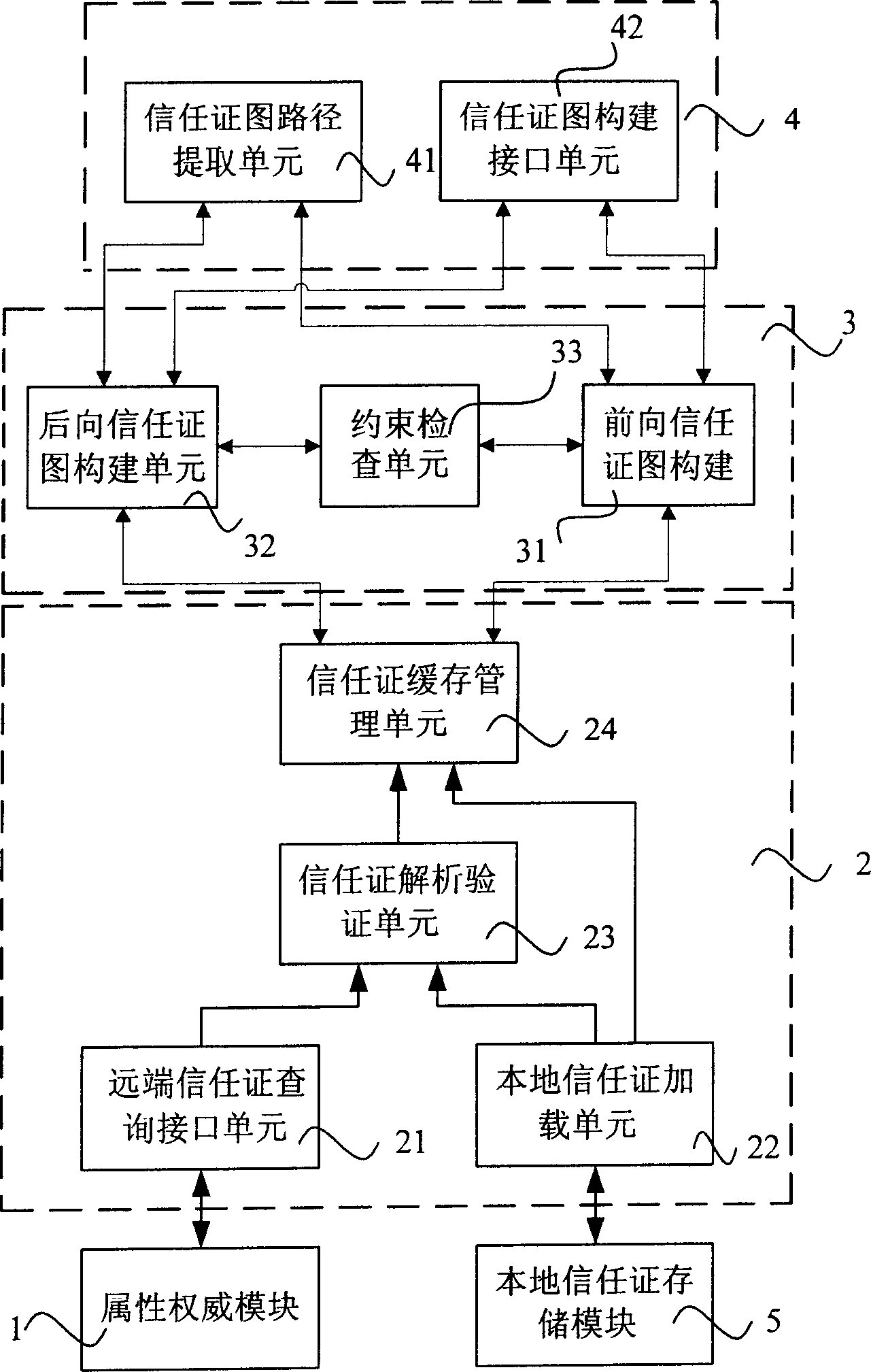
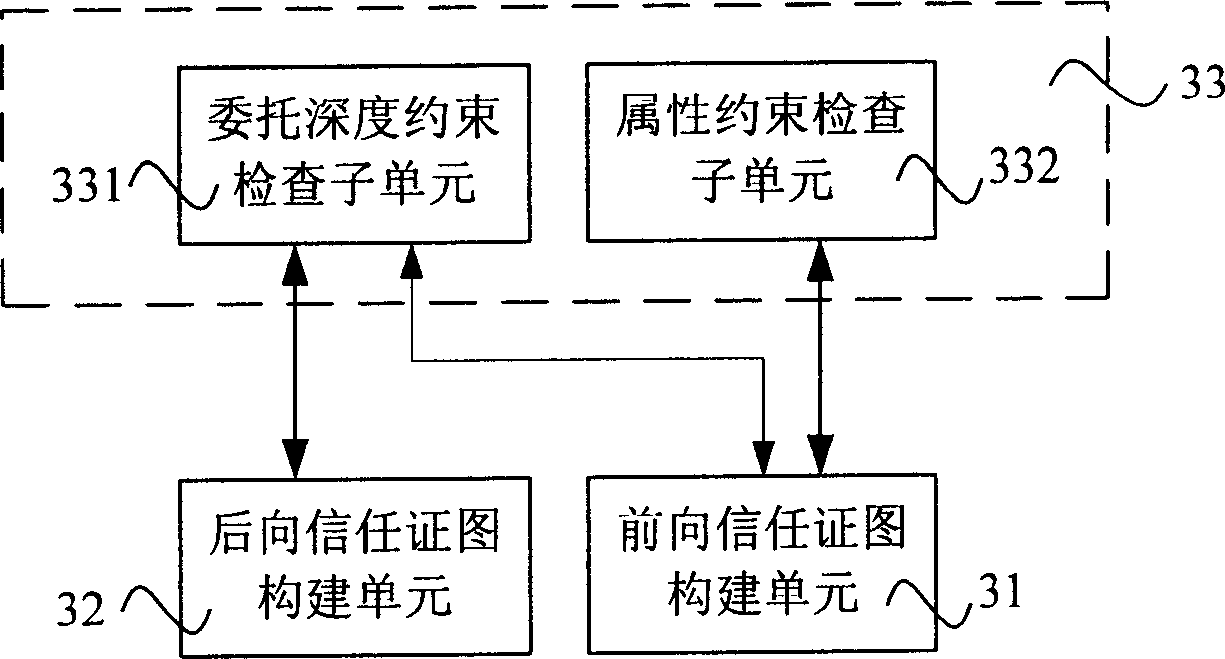
[0039] The present invention expands the role-based trust management language on the basis of RTML, increases the inspection of entrusted depth constraints and attribute constraints, thus increases the expressive ability of policies, and also improves the efficiency of the trust certificate discovery algorithm The present invention also realizes the search of distributed trust certificates. This search method solves the difficult problem of distributed trust certificate discovery, and improves the performance of the system while improving information security.
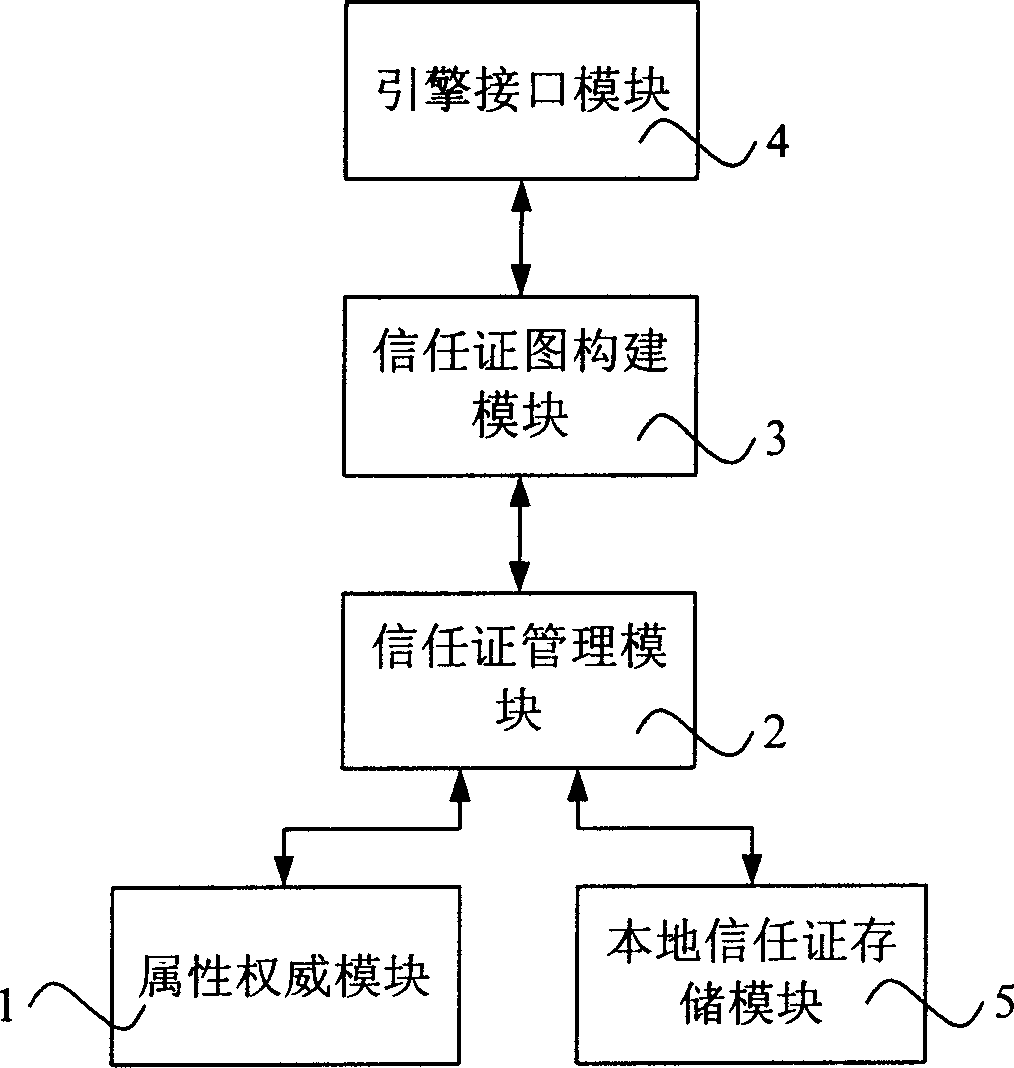
[0040] Such as figure 1 As shown, it is a schematic diagram of the basic structure of the distributed trust management system of the present invention, including the following modules: attribute authority module 1, trust certificate management module 2, trust certificate graph construction module 3, engine interface module 4 and local trust certificate storage module 5. Compared with the local, the attribute authority ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com