Method of using buffer area
A technology of buffer area and sub-cache, applied in the computer field, can solve the problems of reducing the number of buffer areas, insufficient buffer area, suspending work, etc., to achieve the effect of improving the utilization rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0056] First embodiment: AAL5 is a connection-oriented service. When data transmission is required, a permanent virtual circuit PVC (Permanent Virtual Circuit, permanent virtual circuit) between the sending end and the receiving end is established first, and data is transmitted through the permanent virtual circuit.
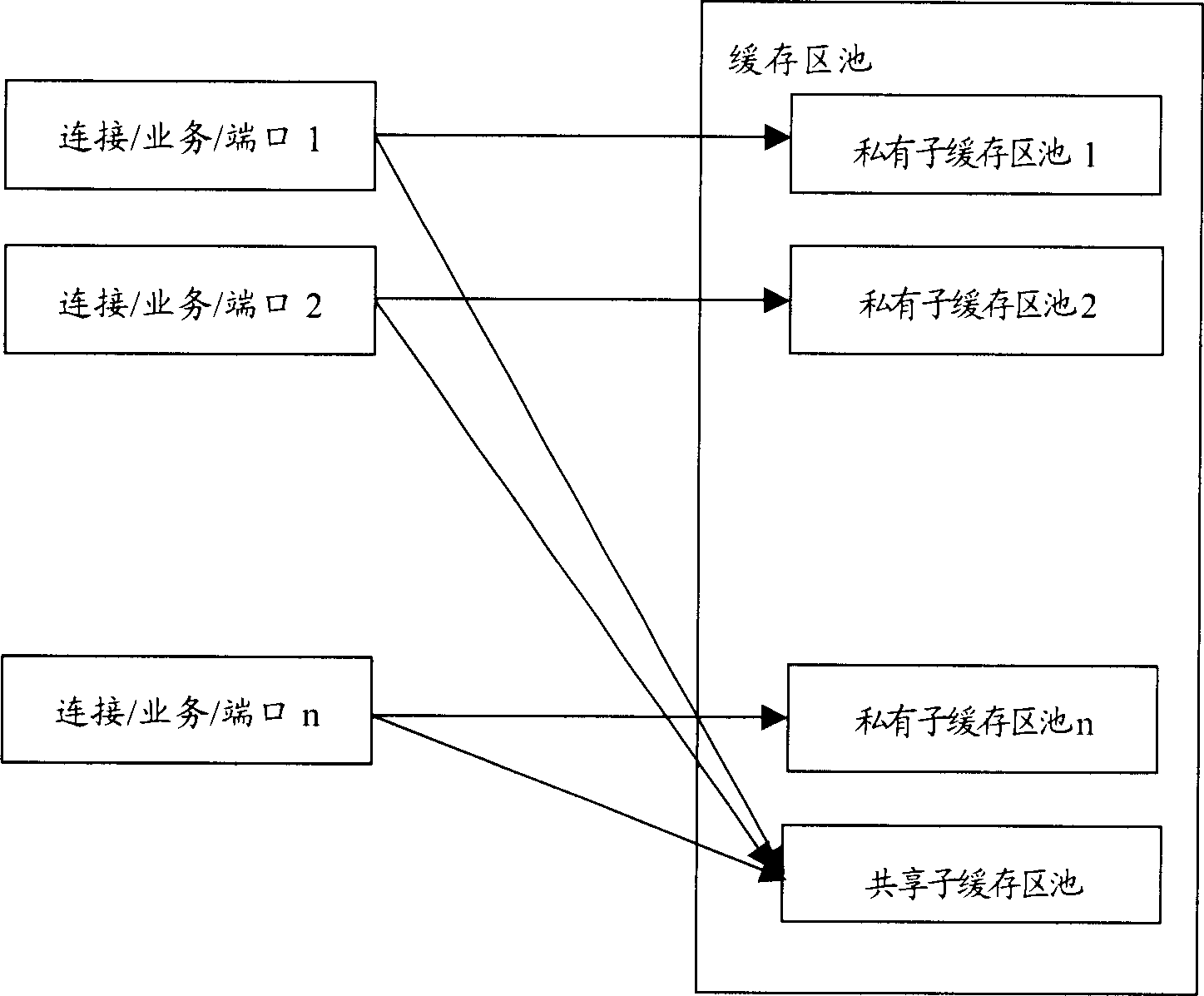
[0057] When the present invention is applied to the data transmission of AAL5, at first the cache area pool is divided into predetermined number of private sub-buffer area pools and shared sub-buffer area pools; Identification (VPI (Virtual Pass Identifier, virtual path identifier), VCI (Virtual Channel Identifier, virtual channel identifier)), therefore, the corresponding relationship between the channel for transmitting data and the private sub-buffer pool can be set according to the network identifier.
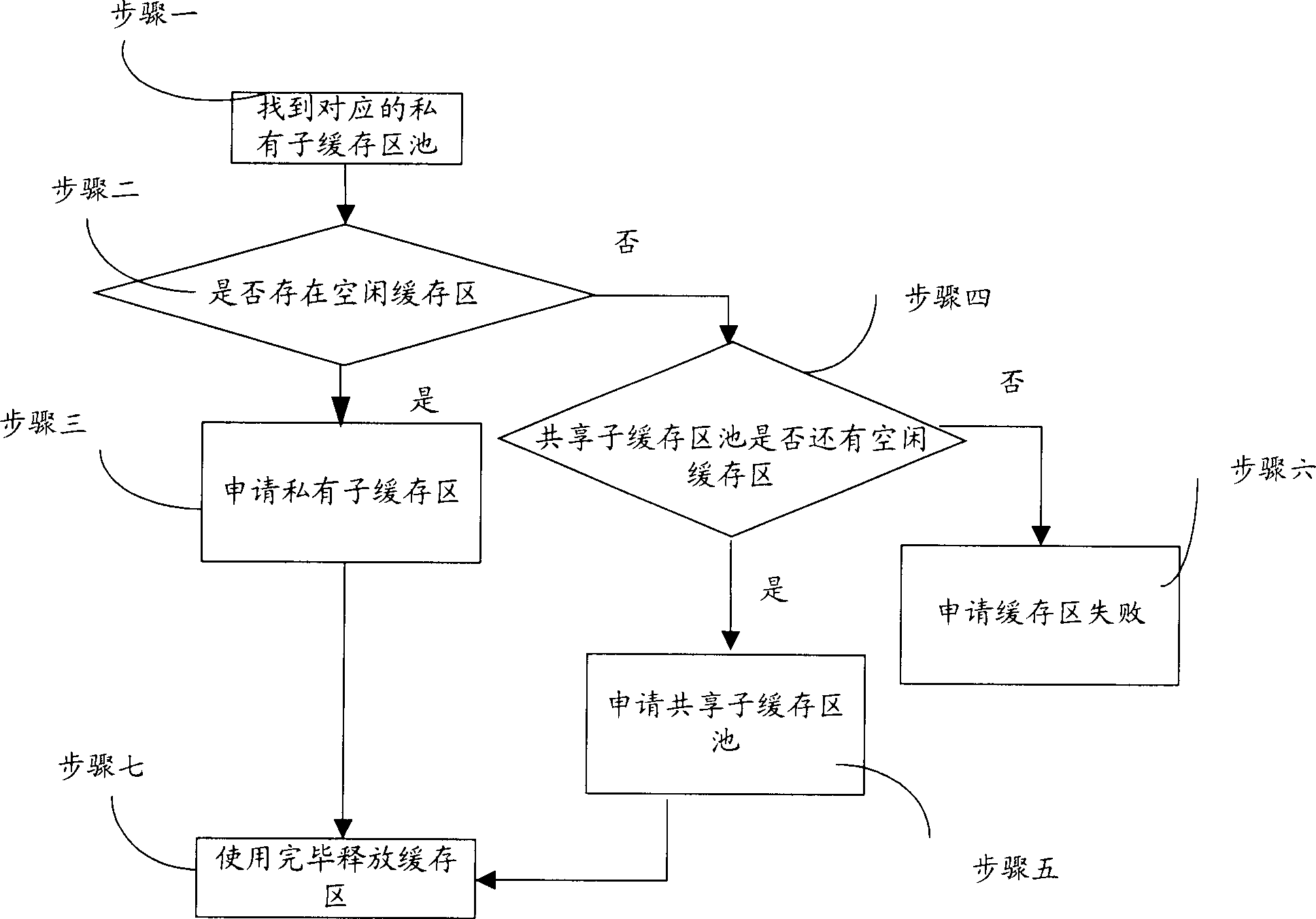
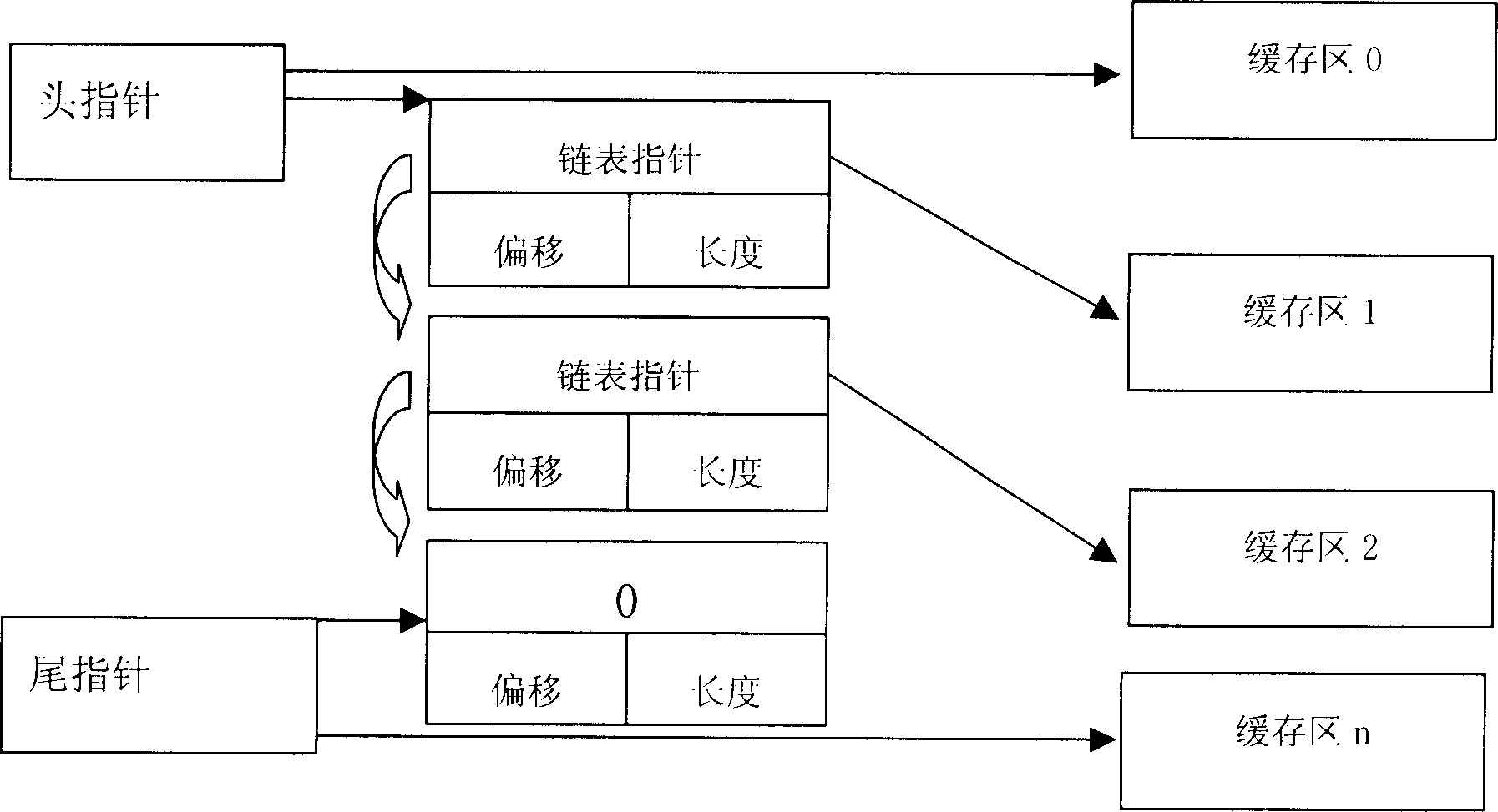
[0058] The method of using each private sub-cache pool is the same as the method of dynamically using the cache in the prior art. In order to facilitate the u...
no. 2 example
[0065] Second embodiment: SSCOP (Service Specific Conection Orientated Protocol, the connection-oriented protocol of specific service) IPOA (IP Over ATM) is based on the different upper layer services of AAL5 connection, and the protocol group is respectively SSCOP / AAL5 / ATM, IPOA / AAL5 / ATM .
[0066] In order to prevent different services from interfering with each other, it is usually necessary to allocate different buffer areas for different service types. When the present invention is applied to these two kinds of services, at first the buffer pool is divided into two private sub-buffer pools and a shared sub-buffer pool for the two types of business; then the private sub-buffer pools are assigned to For the channel corresponding to each service, for example, pool 1 is allocated to SSCOP, pool 2 is allocated to IPOA, and pool 3 is a shared buffer.
[0067] When needing to carry out data transmission, at first find corresponding private sub-buffer pool according to the busin...
no. 3 example
[0069] Embodiment 3: In a communication system, there are different trunk lines between different network nodes. In order to ensure that data from different ports do not interfere with each other, it is necessary to allocate different buffer areas for data from different physical ports during transmission. . When the present invention is applied, different private sub-buffer pools are allocated for data from different physical ports, and a buffer area is allocated as a shared buffer of each physical port. The current port types include trunk mapping ports, connection ports between circuit boards, and optical / electrical interfaces, etc. Therefore, the corresponding relationship between the channel for transmitting data and the private sub-buffer pool can be set according to the port type. The specific management method of the buffer is consistent with the previous example.
[0070] When data transmission is required, first find the corresponding private sub-buffer pool accordi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com