Iris code generation method, individual authentication method, iris code entry device, individual authentication device, and individual certification program
A code generation and color code technology, applied in the field of personal authentication, can solve the problem of increasing the proportion of cameras, and achieve the effect of improving resolution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 Embodiment approach
[0049] figure 1 It is a flowchart showing a personal authentication method using iridescent recognition according to the first embodiment of the present invention. In this embodiment, the authenticatee uses figure 2 The kind of mobile phone with authentication function performs iridescent authentication.
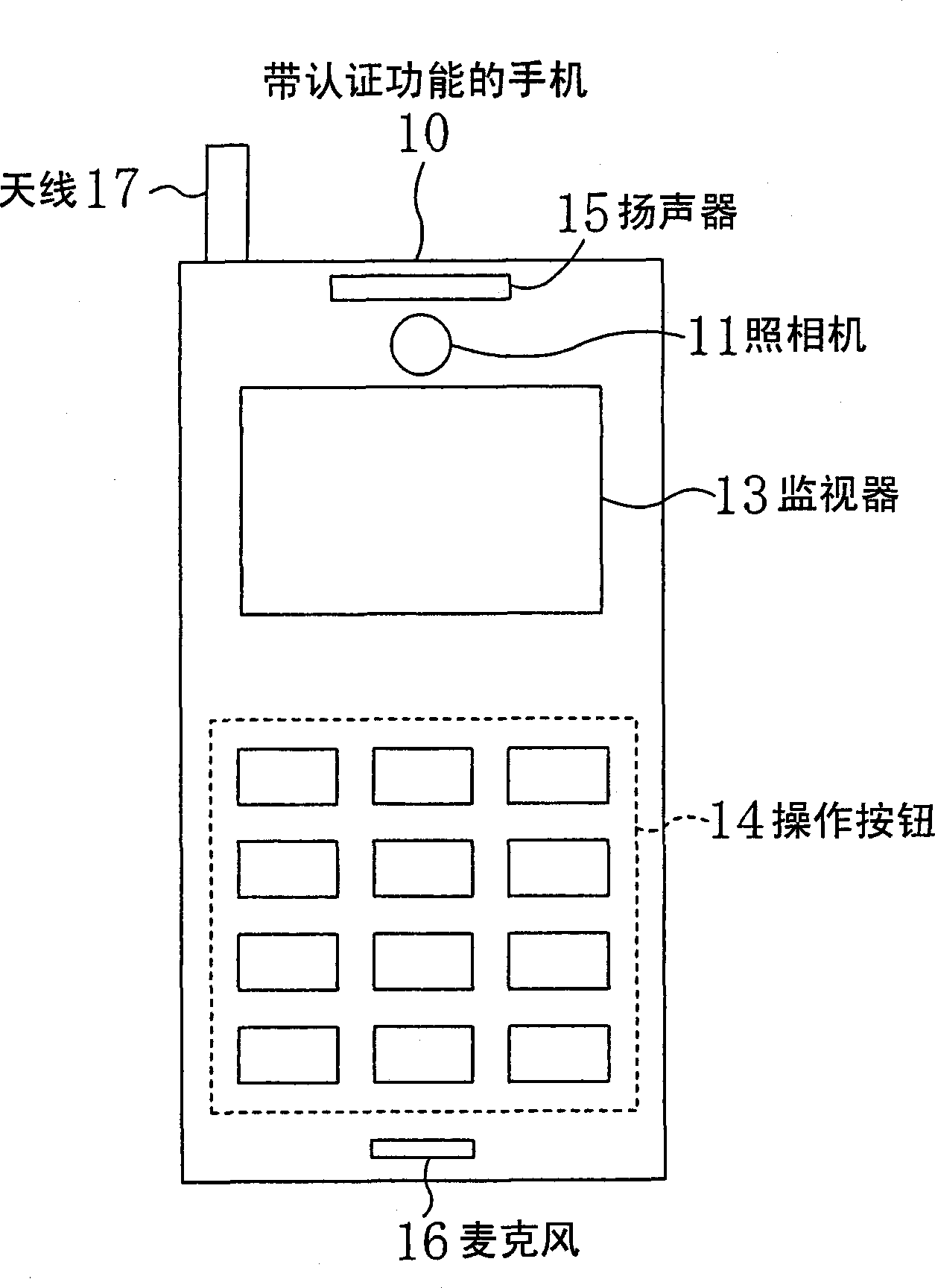
[0050] figure 2 A mobile phone with an authentication function is equipped with a camera 11 for iridescent image photography on an ordinary mobile phone. In addition to the camera 11, a monitor 13, operation buttons 14, a speaker 15, a microphone 16, an antenna 17, and the like are provided. The monitor 13 displays the iridescent image being photographed and the authentication result.
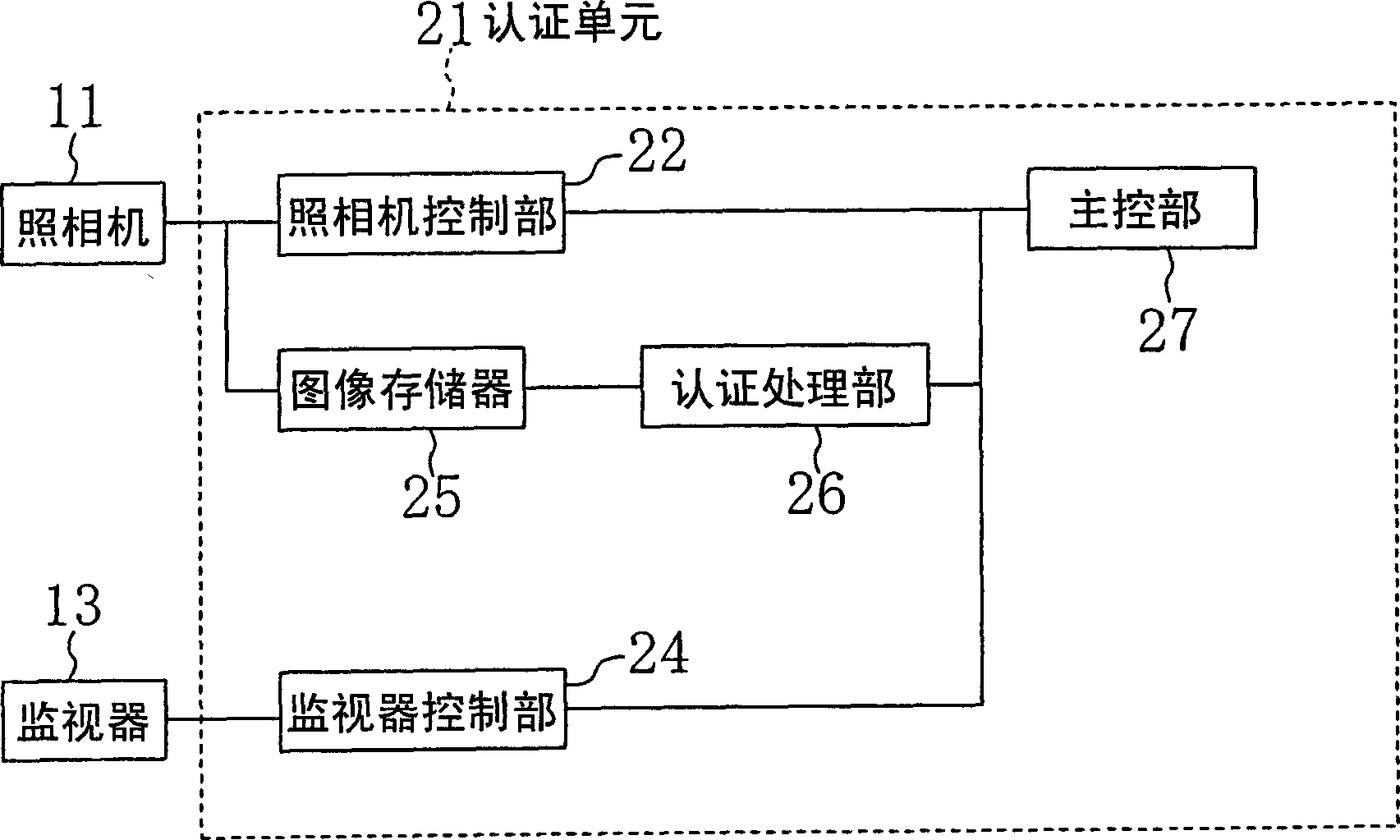
[0051] image 3 yes means figure 2 A diagram of the internal structure of a mobile phone with authentication function. exist image 3 Among them, the camera control unit 22 and the monitor control unit 24 of the authentication unit 21 are connected to the main control unit 27 . Th...
no. 2 Embodiment approach
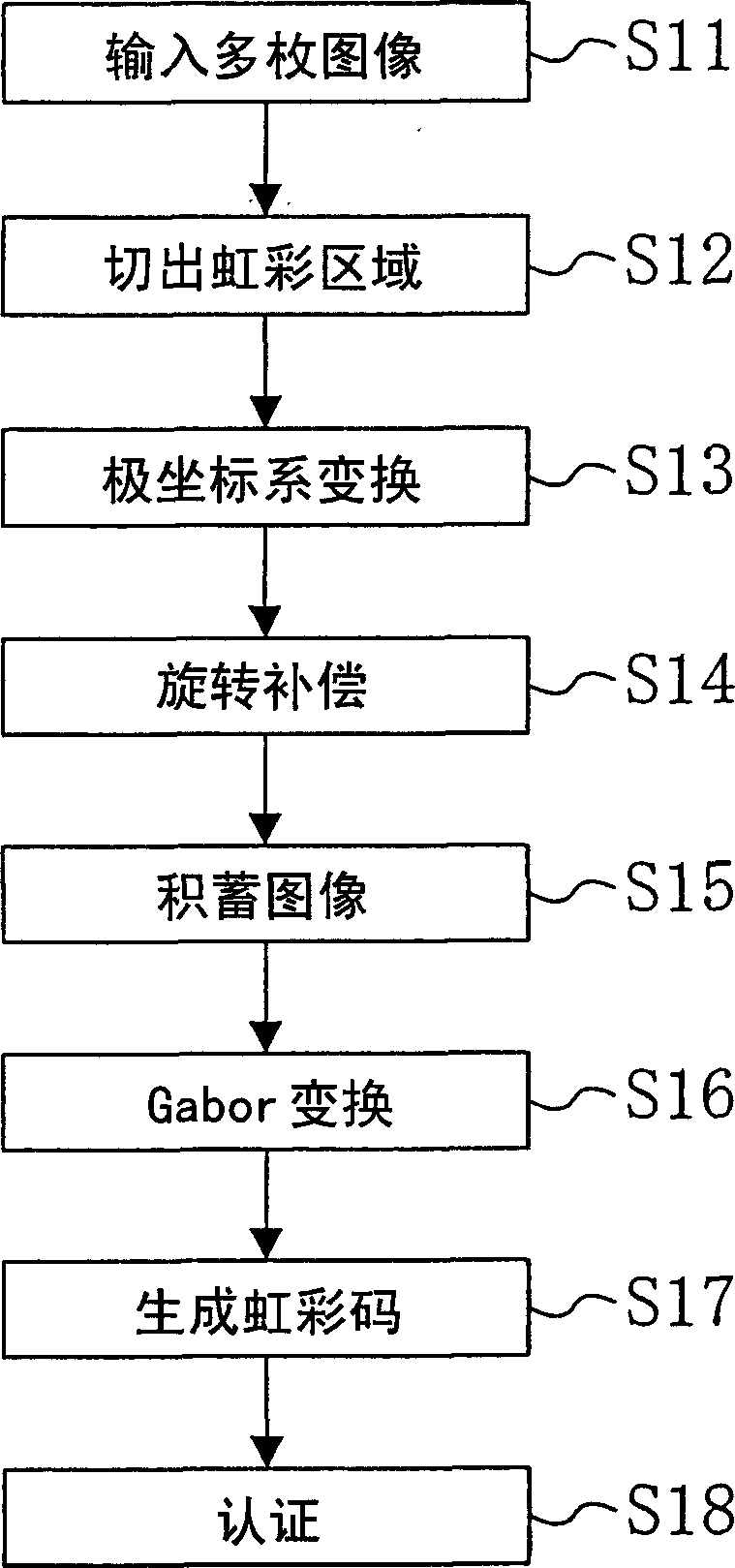
[0083] Figure 16 It is a flowchart showing a personal authentication method using iridescent recognition according to the second embodiment of the present invention. In this embodiment, for the plurality of iridescent images (S21-S23) that have undergone polar coordinate transformation, Gabor transformation is first performed for band limitation (S24), and then the transformed data, that is, the band-limited image Carry out rotation compensation (S25), accumulate after weighted addition (S26), and generate iridescent code (S27). exist Figure 16 In, steps S11~S23, S27, S28, respectively carry out and figure 1 S11 to S13, S17, and S18 are processed in the same manner. By steps S21-S27, the iridescent code generation method is constituted.
[0084] In step S25, to the Gabor transformation data of many (N) images obtained in step S24, such as Figure 17 Rotation compensation is performed as shown. That is, with one of the N pieces of Gabor transformed data (for example, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com