Method for locking terminal attaching region
A technology of belonging area and terminal, applied in the direction of network data management, security device, access restriction, etc., it can solve problems such as failure to consider, loss of terminal cost, high cost of subsidized terminal, etc. The effect of business development security and order, development and stability of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
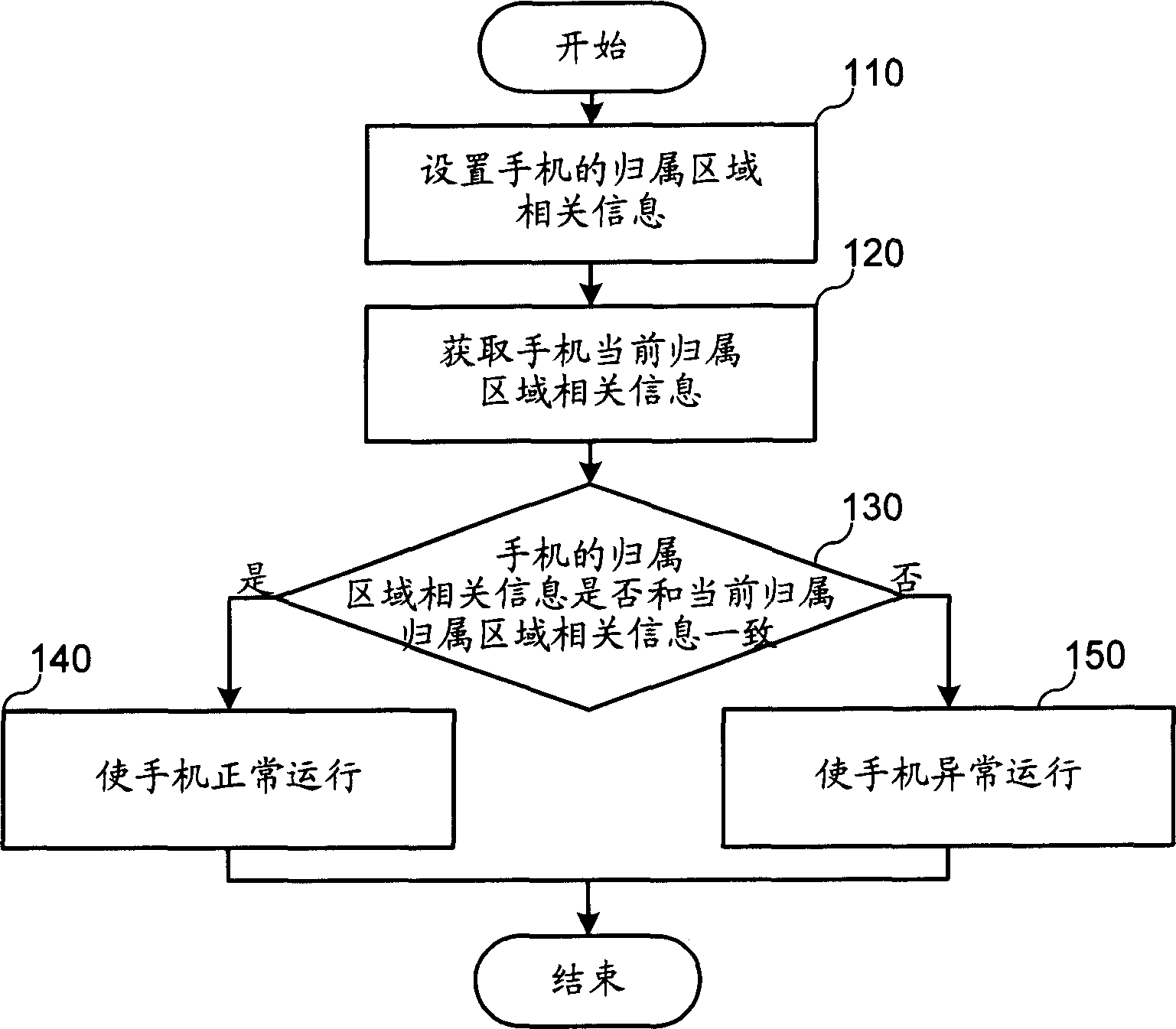
[0027] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0028] In general, the principle of the present invention is to pre-set the relevant information of the terminal's home area, and only when the terminal's current home area-related information is consistent with the preset terminal's home area-related information, the terminal can be used normally; otherwise, abnormal processing is performed , so that the terminal cannot operate normally or use network services. Since the solution of the present invention can limit the terminal to be used in a specified area or network, if the terminal is resold to other operator networks or used in other areas, because its new home area related information is inconsistent with the set terminal home area related information or It is because the current operator information is inco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com