Technology for improving security of accessing computer application system by mobile phone
A mobile phone and application system technology, applied in computer security devices, computing, electronic digital data processing and other directions, can solve the problems of online banking customers' lack of self-protection awareness, low storage and computing capabilities, and insecure connection to servers. Achieve the effect of preventing theft of users' online bank account transactions, a wide range of applications, and many security algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment approach
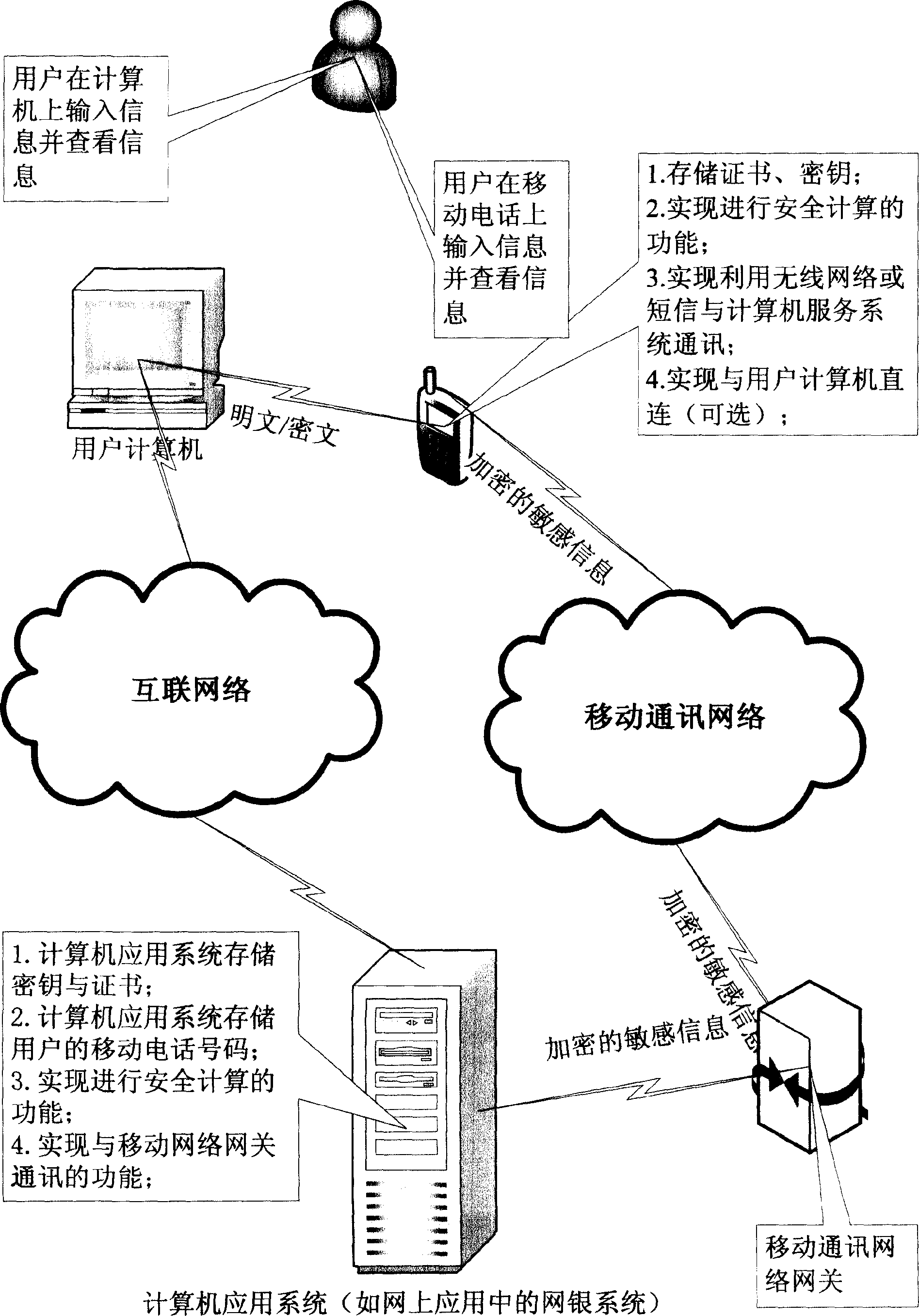
[0043] Taking the current online application with increasingly prominent security problems as an example, the implementation method of this technology is described.
[0044] Application 1: User authentication method for an online application:
[0045] 1. The operator (or third party) of the online application provides the key to the user;
[0046] 2. Install the key in the mobile phone (determined to be installed in its secure area according to the type and function of the SIM card and mobile phone);
[0047] 3. The user connects to the online application through the Internet browser;
[0048] 4. When the user starts the application on the mobile phone, he needs to enter the password and select the interactive online application;
[0049] 5. The user enters the user name and password to log in to the application (this step can be omitted, it is only used as a simple verification here, because the latter steps involve some complicated calculations and have some costs, without...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com