Service safety authentication method based on smart card under controlled Internet network environment
A technology of security authentication and smart card, which is applied in the field of security authentication mechanism, can solve problems such as inability to adapt well, and achieve the effects of ensuring data security, simplifying the authentication process, and reducing construction costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
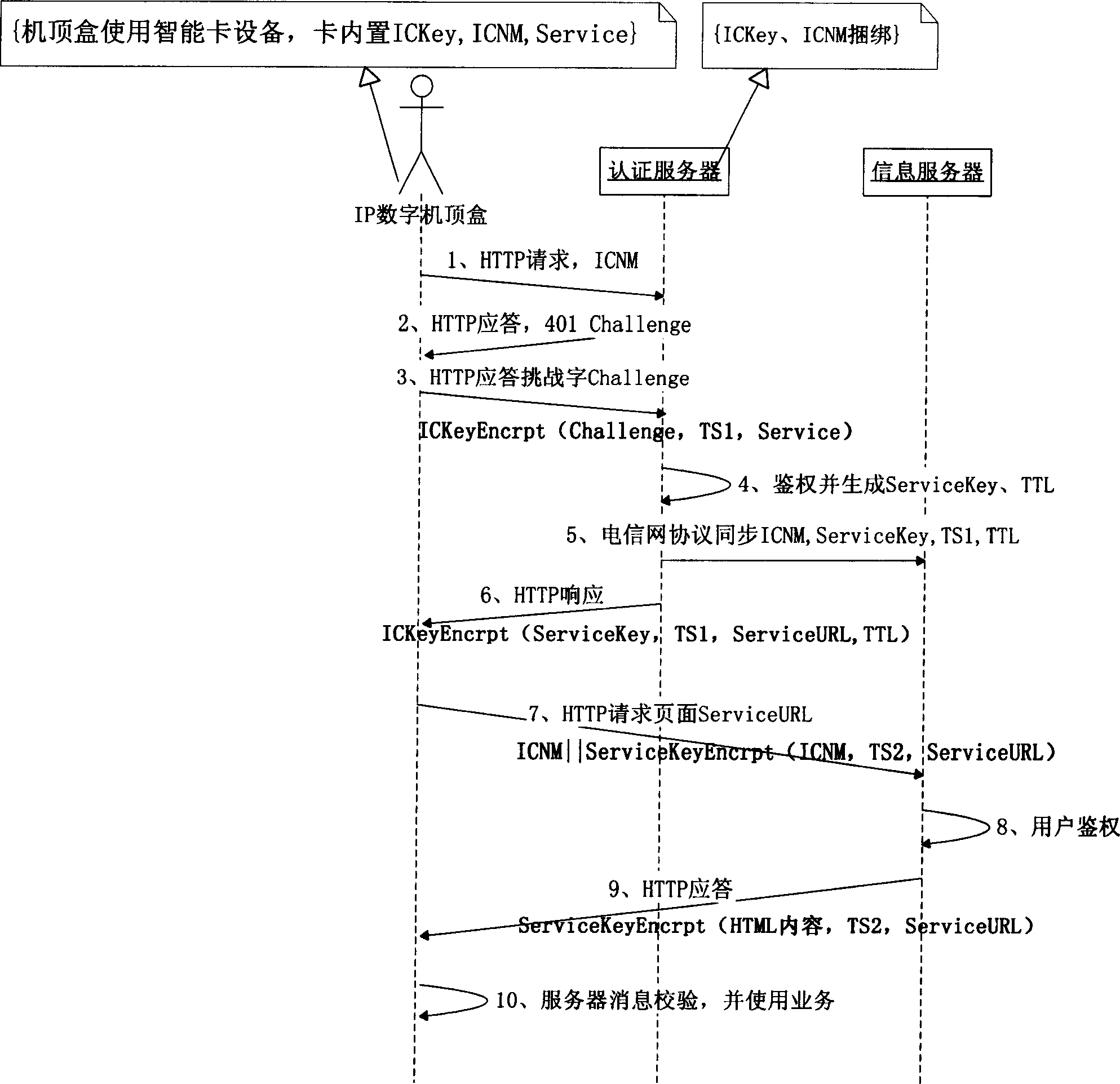
[0037] The following is based on figure 1 and figure 2 The preferred embodiments of the present invention are given and described in detail so that those skilled in the art can understand the present invention more easily, but they are not intended to limit the scope of the present invention.
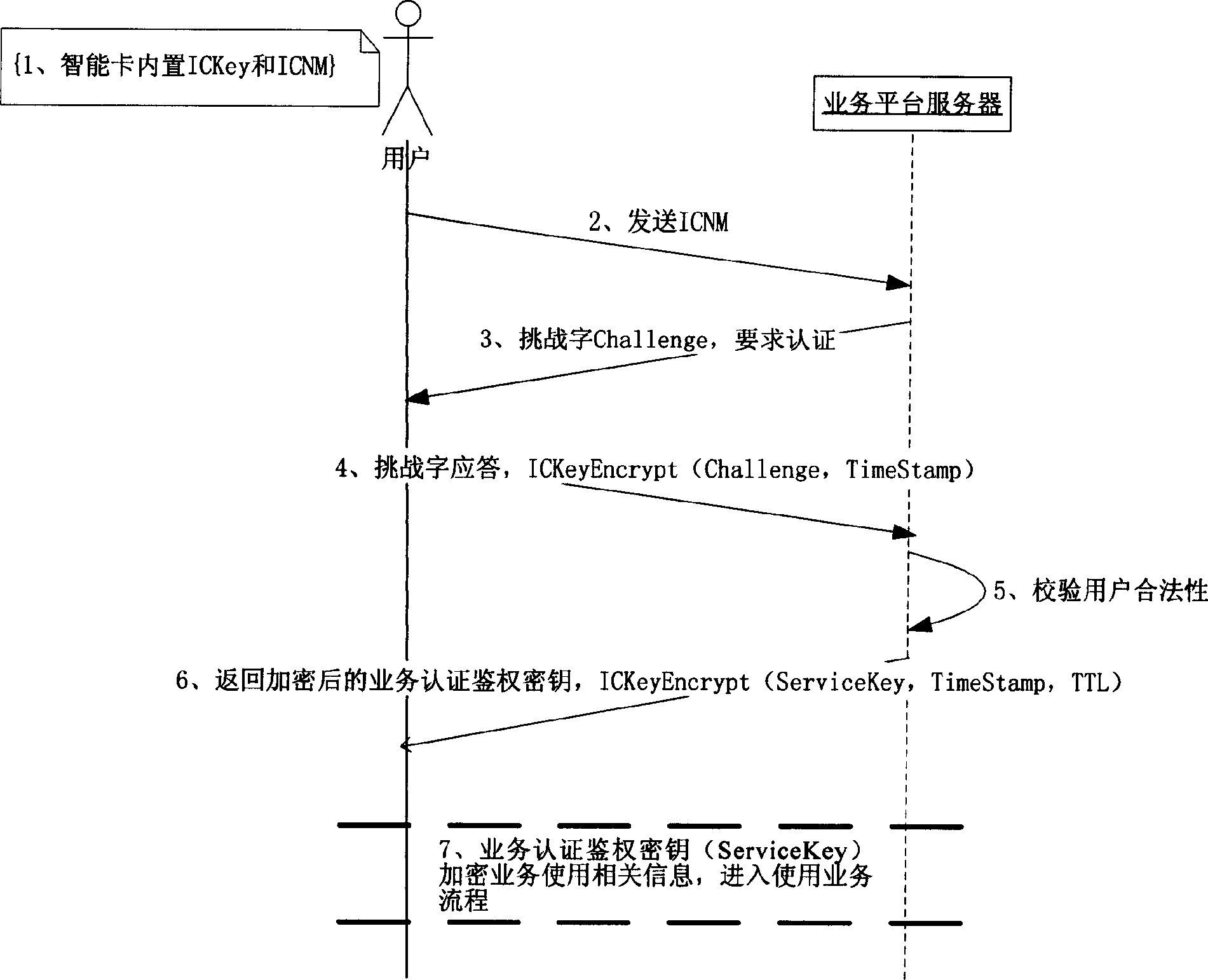
[0038] see figure 1 ,as the picture shows:
[0039] 1. Write the smart card key (ICKey) and smart card number (ICNM) in the smart card and distribute them to users;
[0040] 2. When the user uses related services for the first time, send the smart card number (ICNM) to the service server, that is, the service platform server;
[0041] 3. The business server initiates a challenge process, requiring the user to use the smart card key (ICKey) for identity verification;
[0042] 4. The user generates a time stamp (TimeStamp), uses the smart card key (ICKey) to encrypt the challenge word (Challenge) and time stamp (TS), and responds to the challenge word;
[0043] 5. The service server...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com