Automatic excavating method for integer overflow loophole
A technology of loopholes and objects under test, applied in the field of software engineering, can solve problems such as constructing test data, abnormal parameter processing, etc., to achieve the effect of improving quality and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention provides an automatic mining method for integer overflow vulnerabilities. In order to make the purpose, technical solution, and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
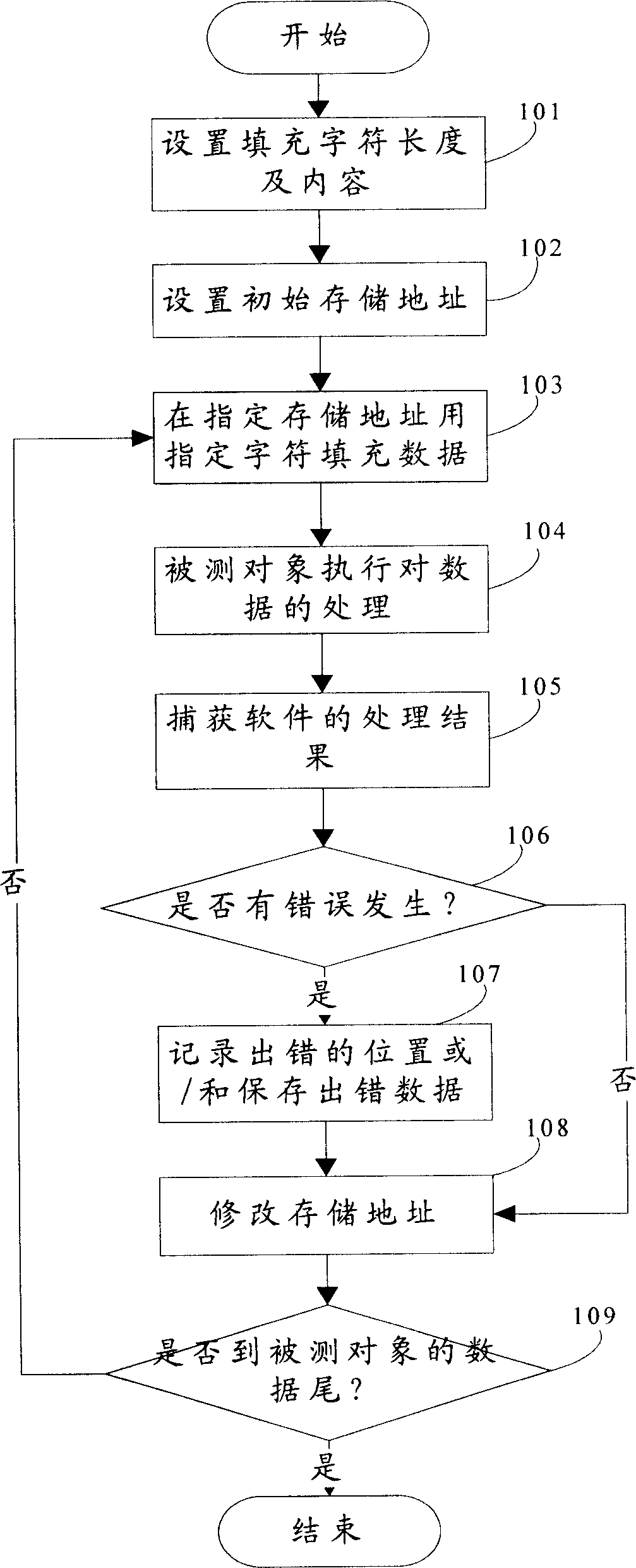
[0051] see figure 1 , realize the concrete flow process of the present invention as follows:
[0052] Step 101: set the length and content of the filling characters, that is, input parameters, and modify the data of the measured object to the set parameters when performing the test;
[0053] Step 102: Set the initial storage address of the object under test, and start testing from the set initial storage address during testing;
[0054] Step 103: filling data at the specified storage address with preset parameters, and saving it as a constructed test case;
[0055] Step 104: the object under test is the software, start running the program, and process the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com