Cipher safety inputting method of intelligent communication terminal
An intelligent communication terminal and password security technology, which is applied in the field of password security input of intelligent communication terminals, can solve the problems of key interception and user privacy threat, and achieve the effects of ensuring security, easy implementation and avoiding theft.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
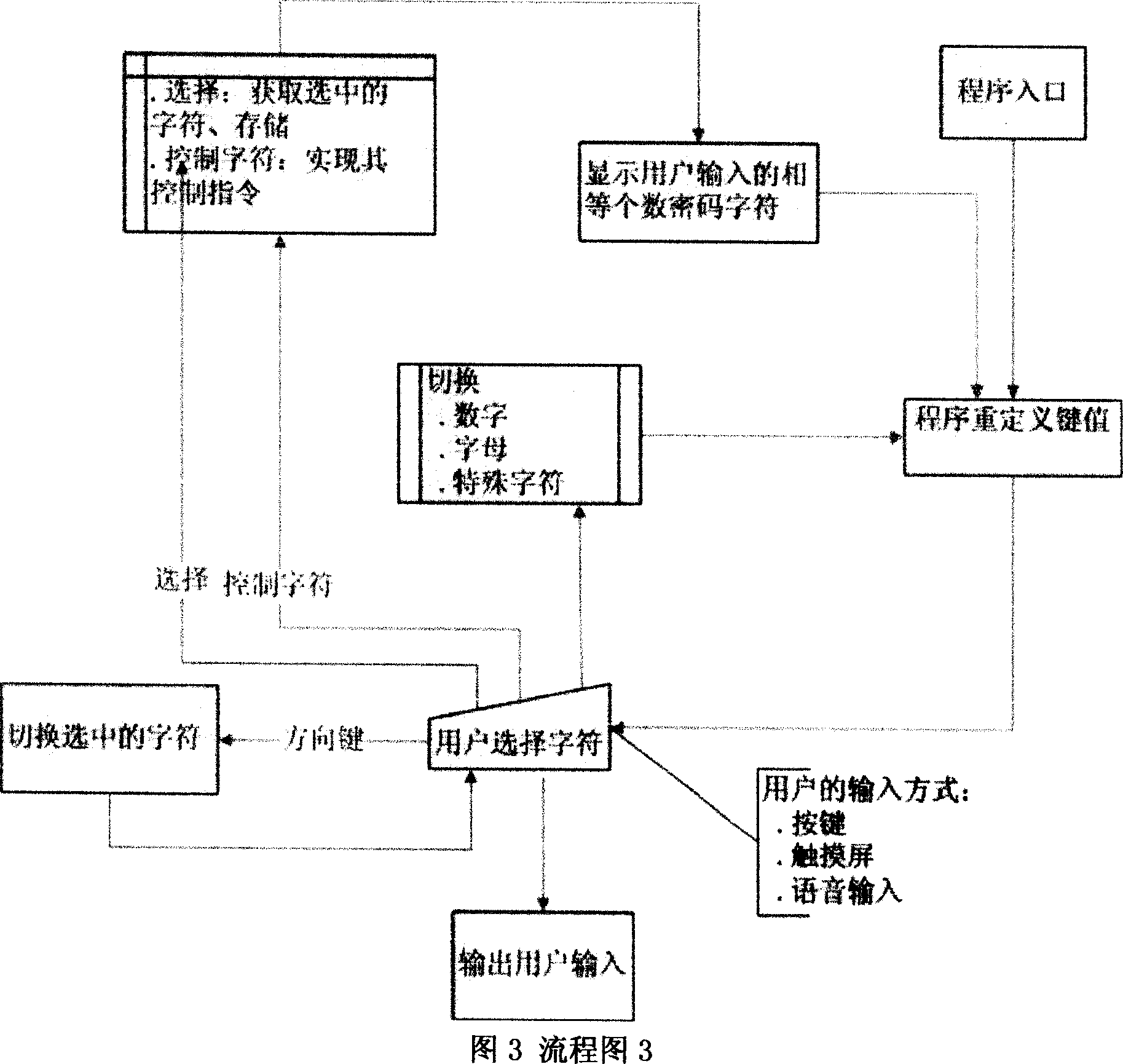
[0059] Example: A user uses a mobile phone to inquire about mobile phone bills
[0060] 1. The user uses the mobile phone to check the call charge
[0061] 2. After the user enters some query information, the system prompts the user to enter a 5-digit password (for example, the user wants to enter the password "62F34")
[0062] 3. A password prompt input box and
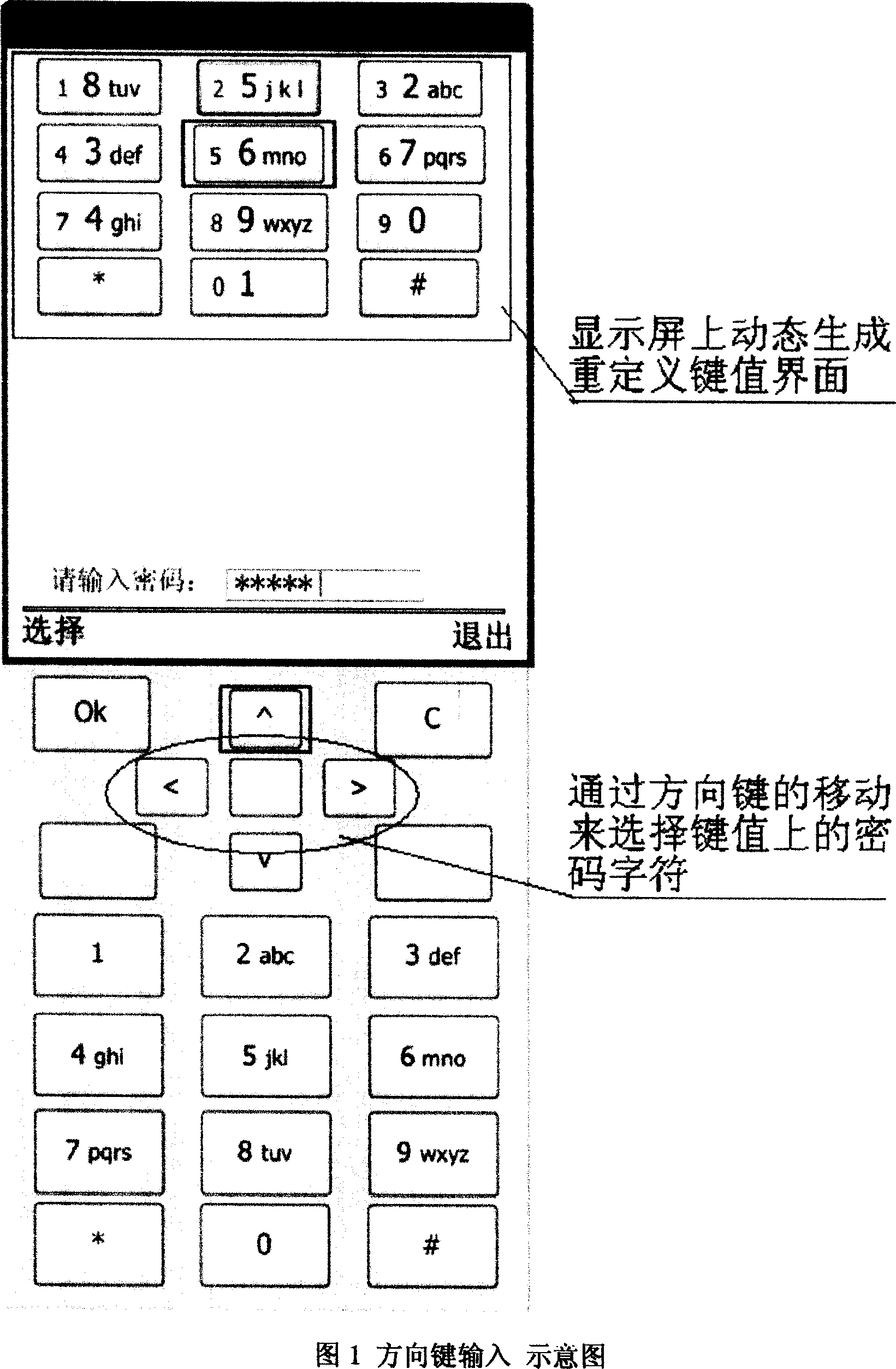
[0063] 12 (3×4) squares appear on the dynamic password input interface, and 0~9 numbers are randomly distributed among them.
[0064] (Refer to the attached picture "Schematic Diagram 1") The cursor stays on the first frame on the upper left
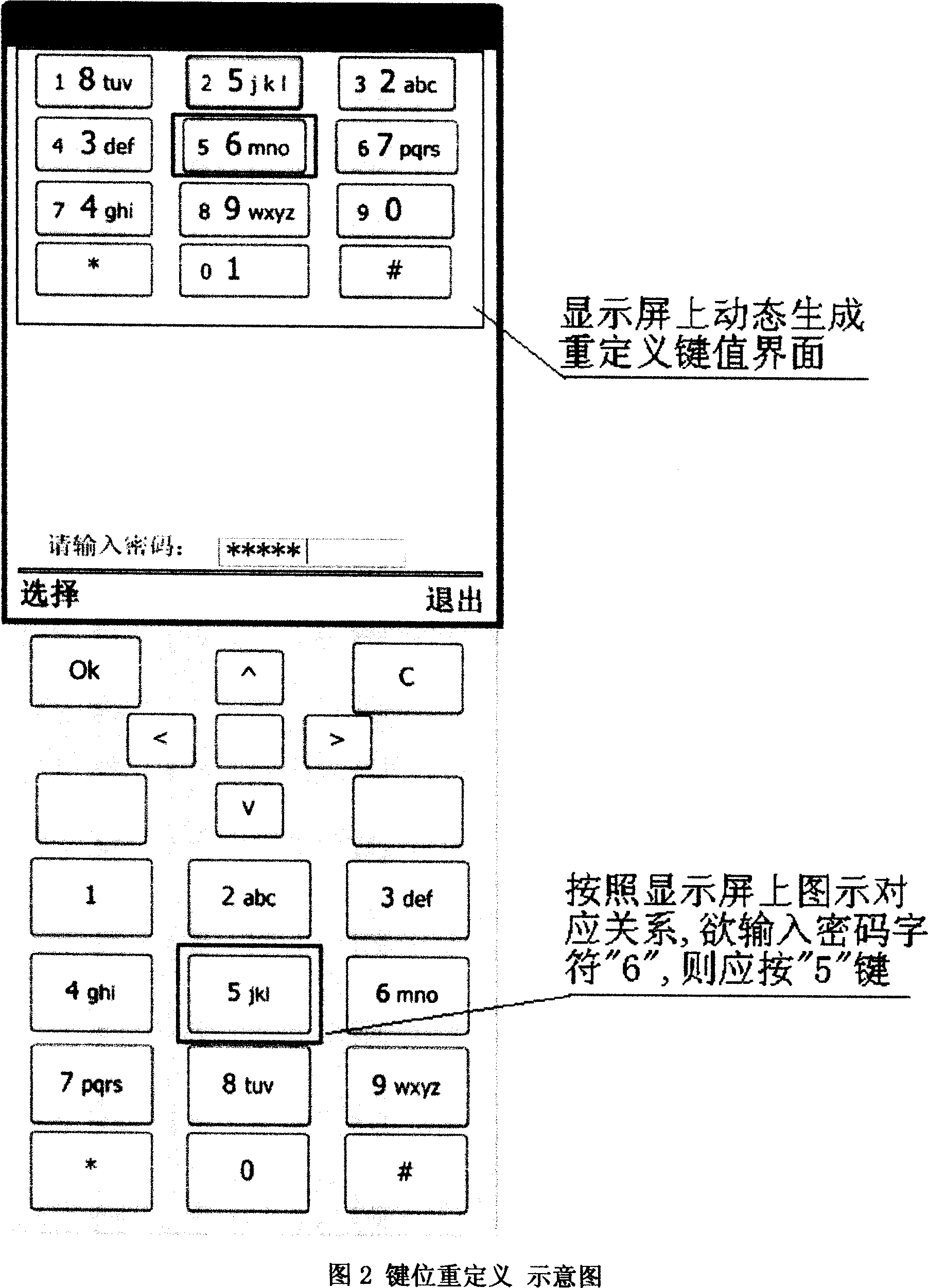
[0065] b Redefine the key-value interface and randomly regenerate each key with a new corresponding relationship on the interface.
[0066] For example, "key 6" on the display screen corresponds to key "key 5" on the mobile phone (see accompanying drawing "schematic diagram 2")
[0067] (Step 3 is completed" and the dynamic key-value arrangement interface appears)
[0068]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com