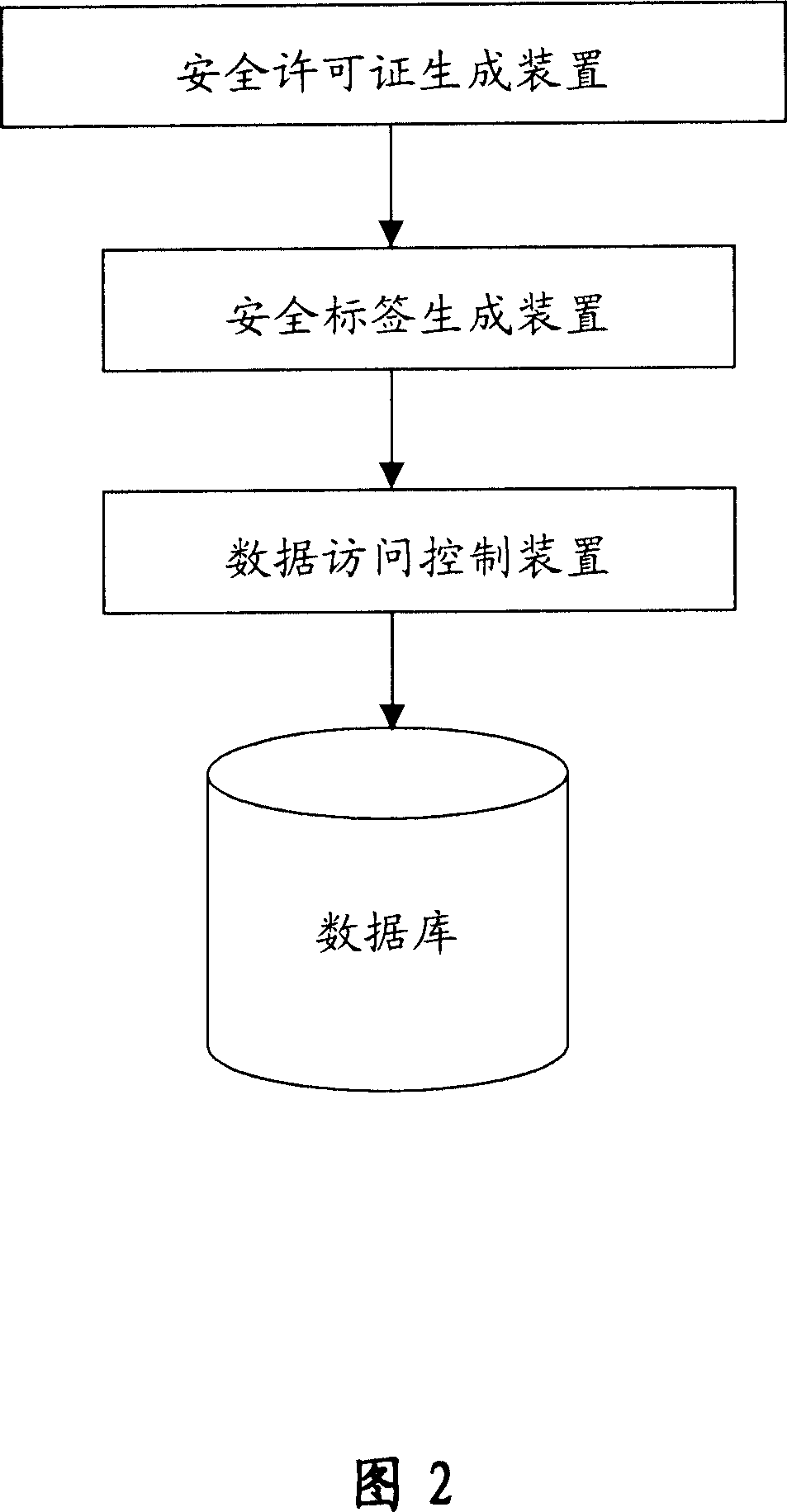
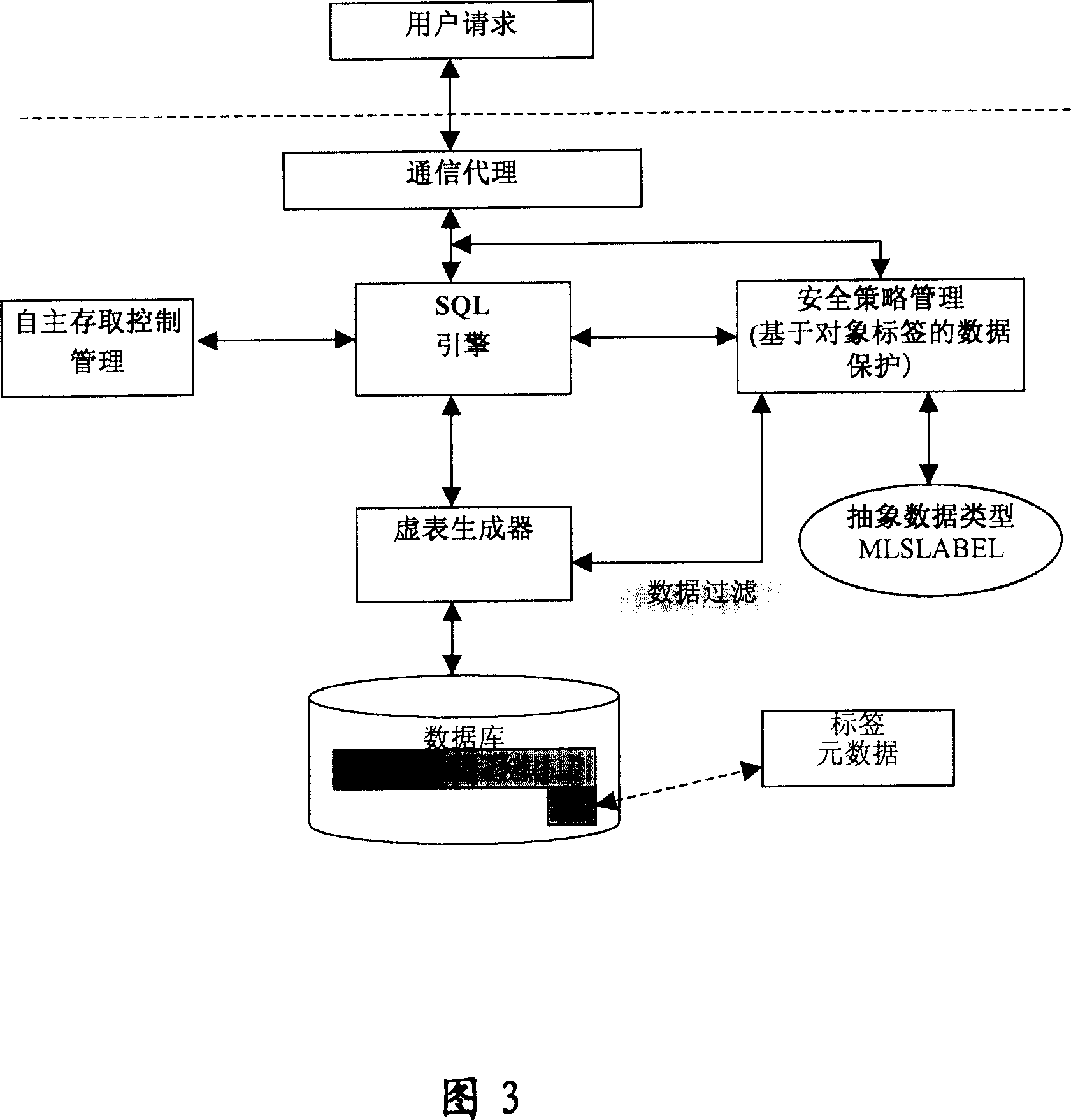
Data protecting method based on target labeling and operation device
A technology for data protection and execution device, applied in the field of object tag-based data protection method and execution device, can solve problems such as coarse granularity, and achieve the effects of improving security and being easy to understand and use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
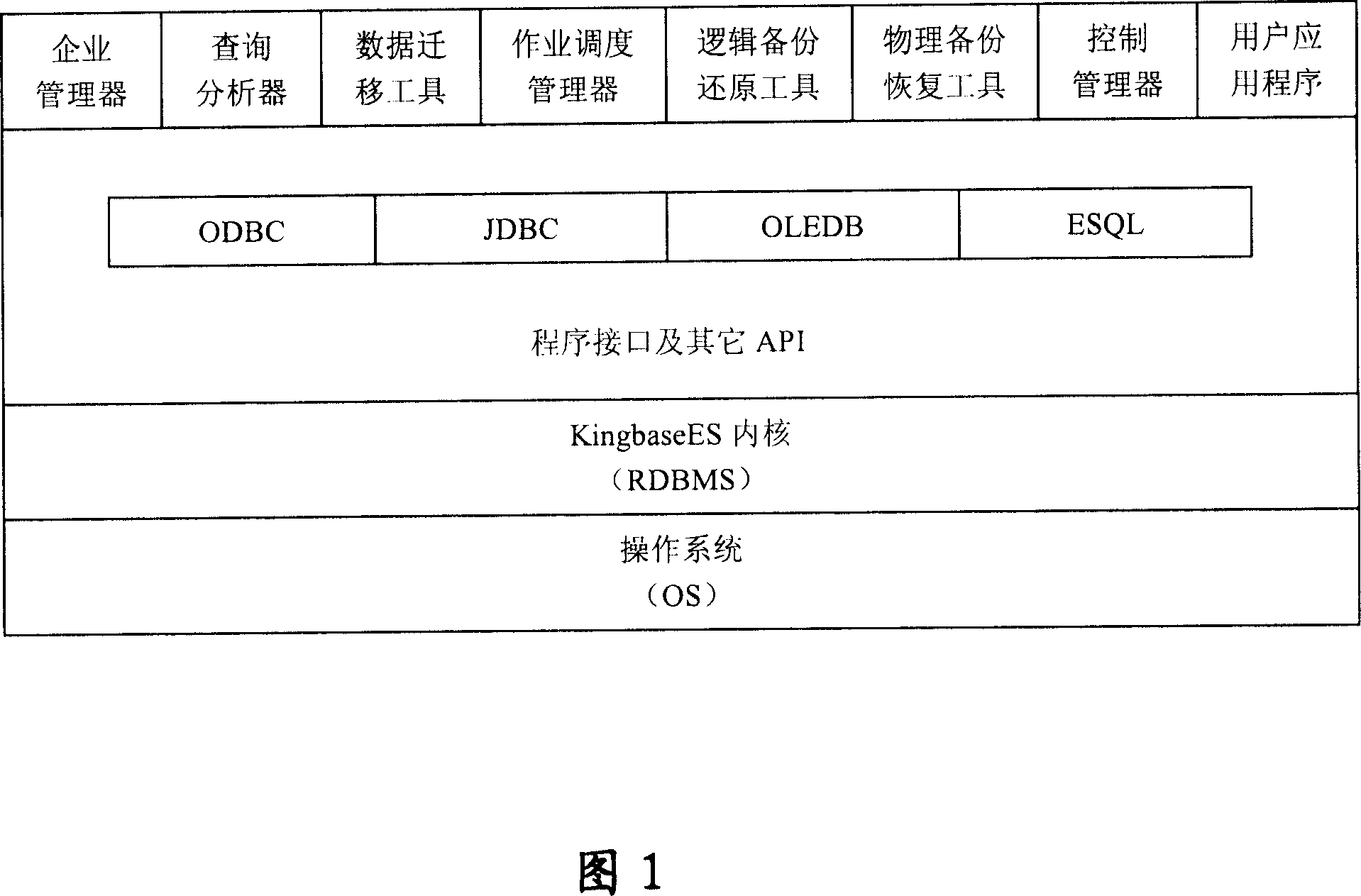
[0028] The specific embodiments of the present invention will be described below in conjunction with the drawings. Figure 1 shows the block diagram of the database management system, and its applicable platforms are:
[0029] One, server side
[0030] Hardware environment:
[0031] CPU: Pentium IV or above or compatible models;
[0032] Memory: 256M or more, 512M or more is recommended;
[0033] Hard disk: at least 1G free space. It is recommended to use NTFS or EXT-3 for the file system.
[0034] Software environment: Windows 2000, Windows XP, Windows 2003, Red Hat, Red Flag Linux, etc.
[0035] 2. Client:
[0036] Hardware environment:
[0037] CPU: Pentium III or higher or compatible models;
[0038] Memory: above 128M;
[0039] Hard disk: at least 100M free space.
[0040] Software environment: Windows 2000, Windows XP, Windows 2003, Red Hat, Red Flag Linux, etc.
[0041] 3. The database management system function:
[0042] Among them, the KingbaseES system consists of a batch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com