Method of transacting a purchase
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
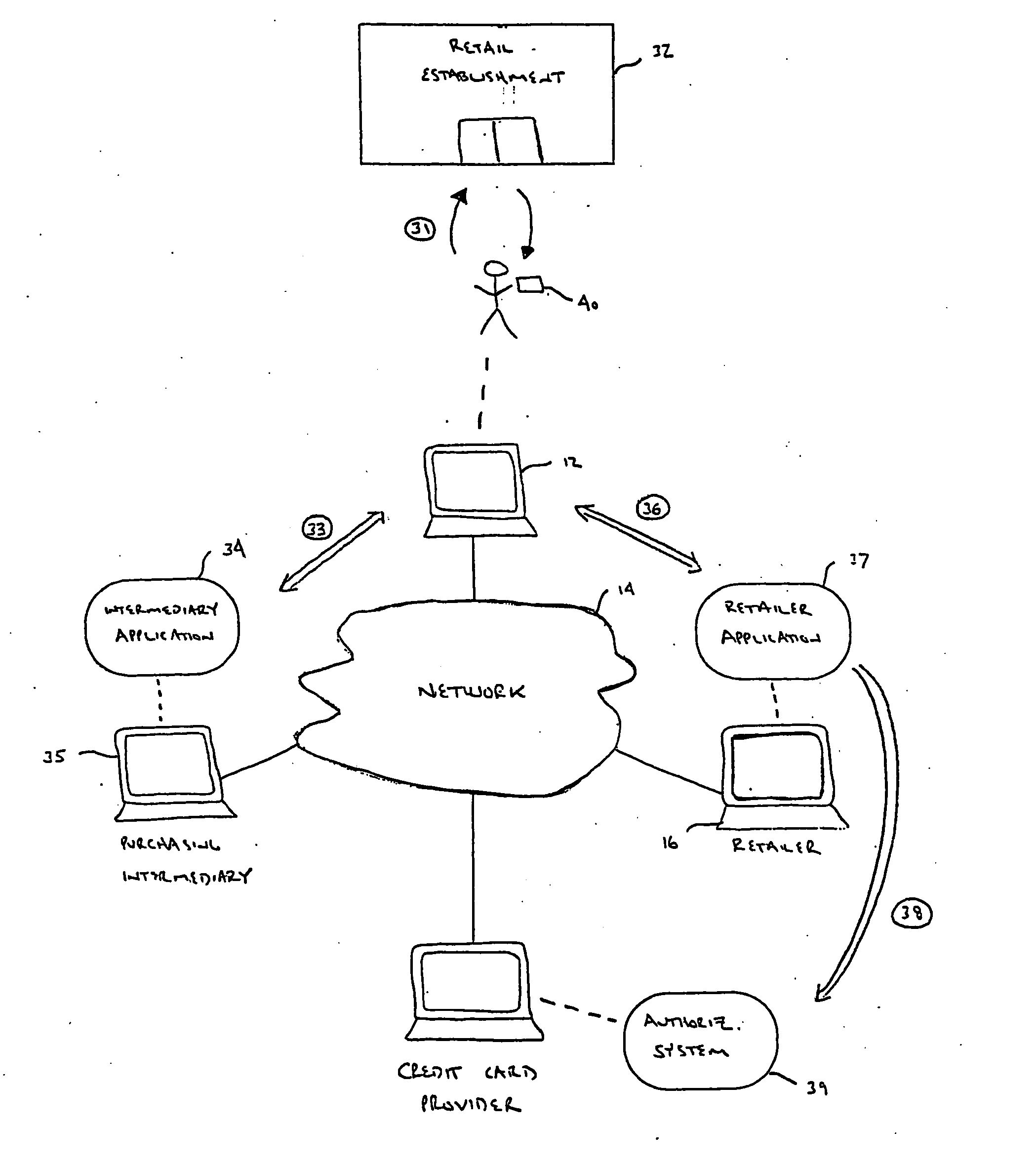
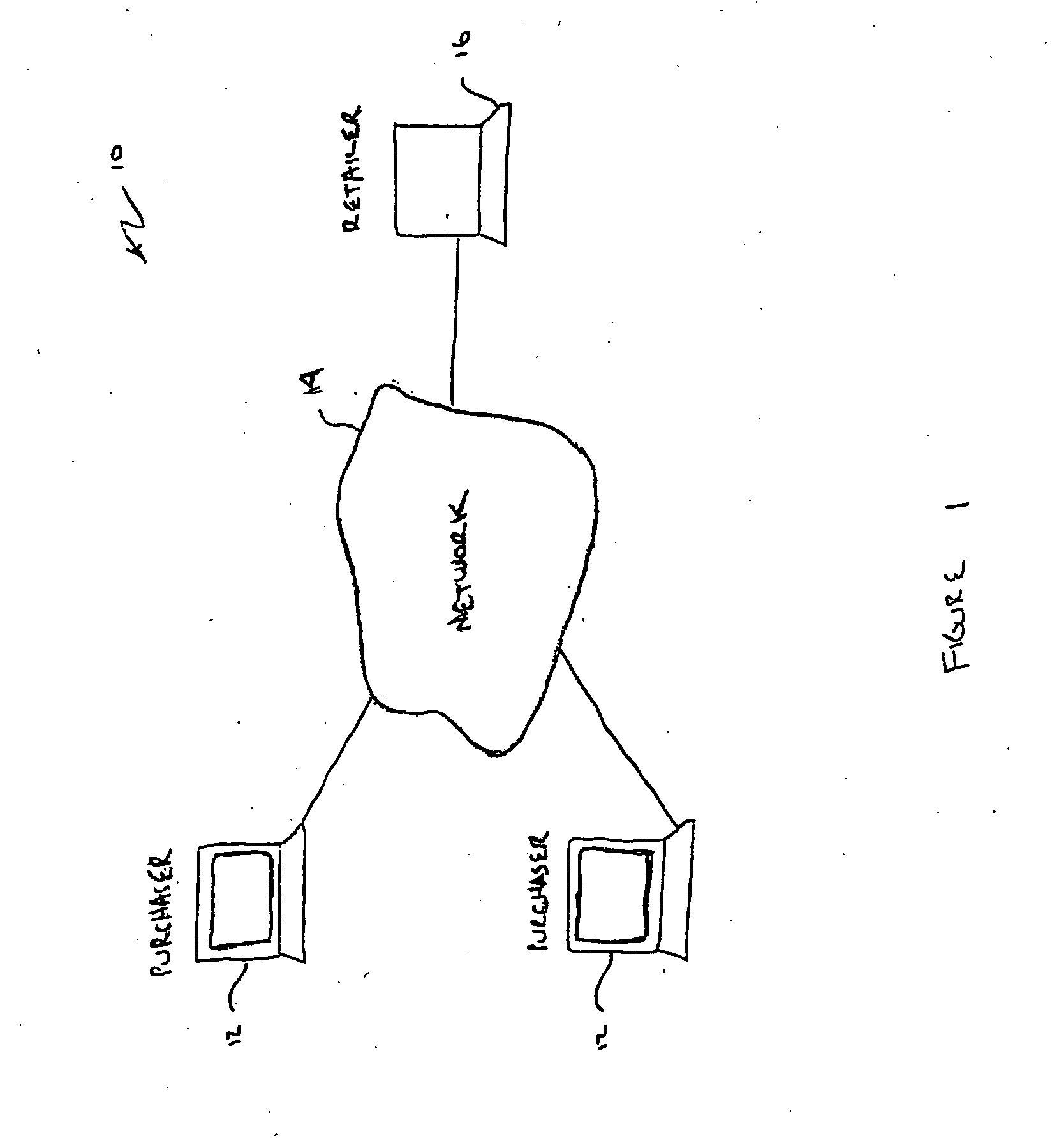
[0012]FIG. 1 illustrates the basic components of a conventional computer-implemented purchasing system 10. The purchasing system 10 is comprised of a plurality of purchasing computing devices 12 interconnected via a network 14 (e.g., the Internet) to at least one retail computing device 16. As will be apparent to one skilled in the art, the computing devices are able to communicate using common communication protocols (e.g., TCP / IP) over different types of network channels. For illustration purposes, a preferred embodiment of the computing device is a personal computer (PC). Of course, it will be appreciated that the principles of the invention can be employed in a wide variety of computing devices, including but not limited to a telephone, a television or a personal digital assistant (PDA).
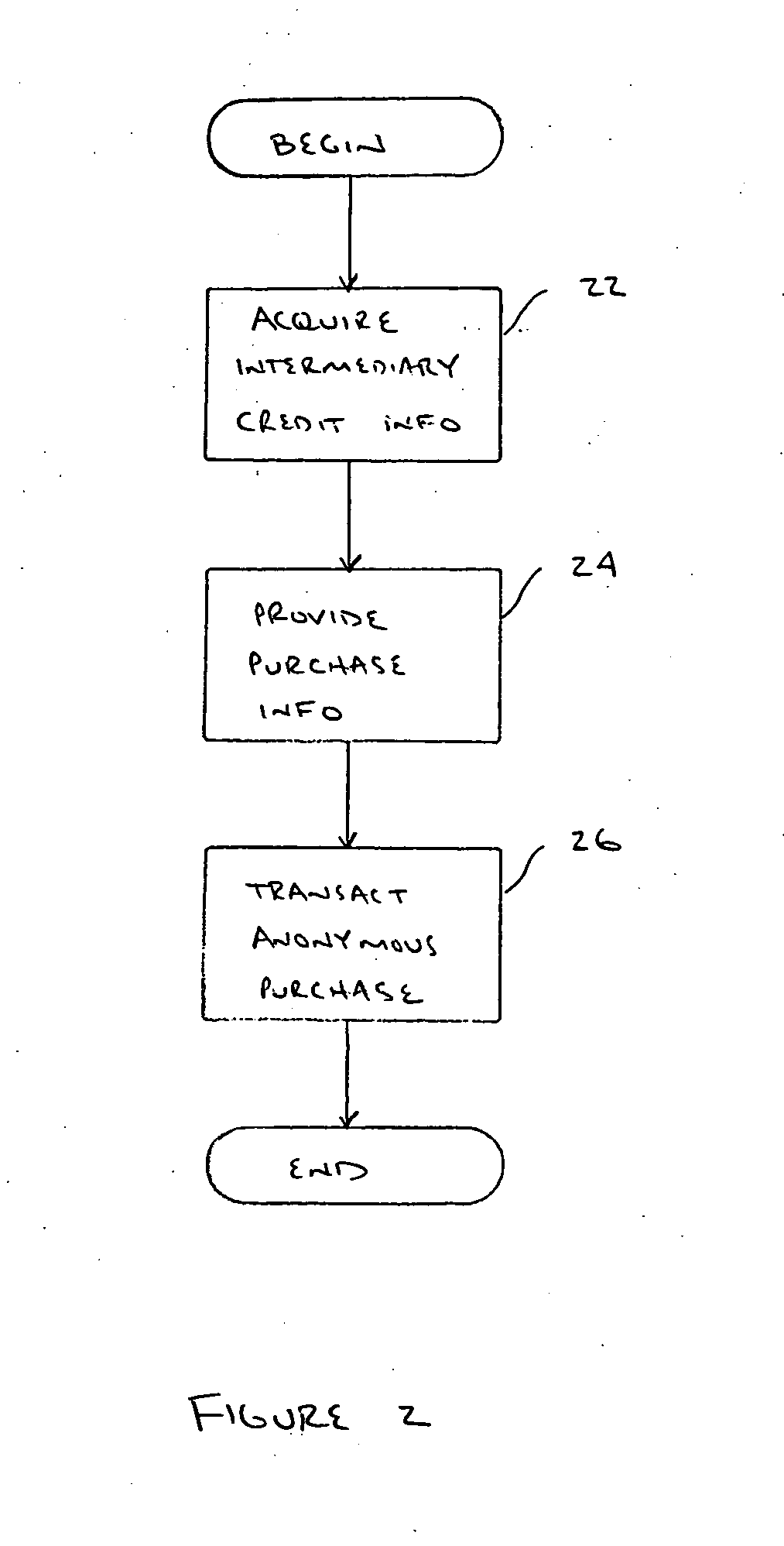
[0013] In accordance with the present invention, an overview of a method for transacting an anonymous purchase using the computer-implemented purchasing system 10 is shown in FIG. 2. First, a pu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com