Generalized network security policy templates for implementing similar network security policies across multiple networks
a network security policy and network security technology, applied in the field of automatic network security, can solve the problems of difficult and/or expensive installation and use high cost, and inconvenient maintenance of network security devices, and achieve the effect of efficiently updating the configuration of a large number of operating network security devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
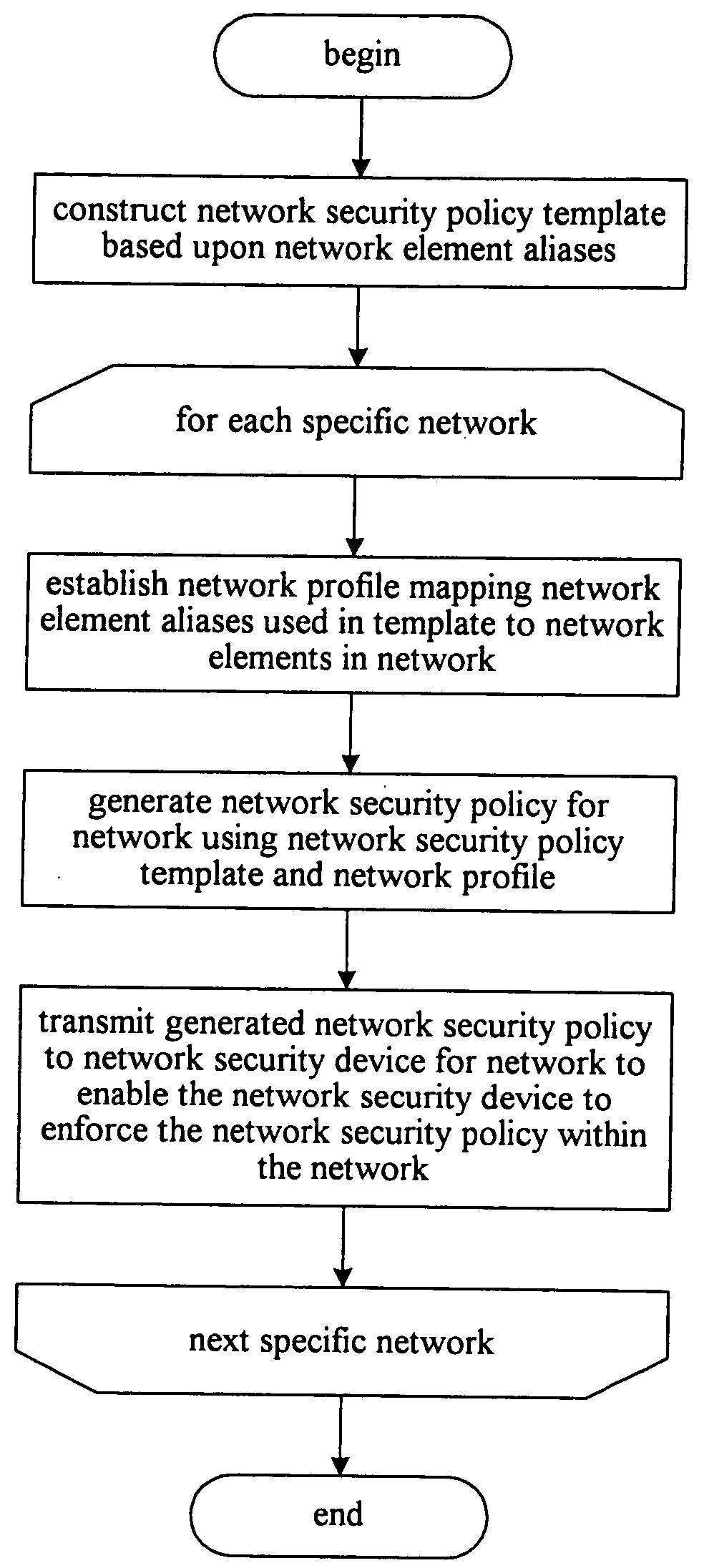
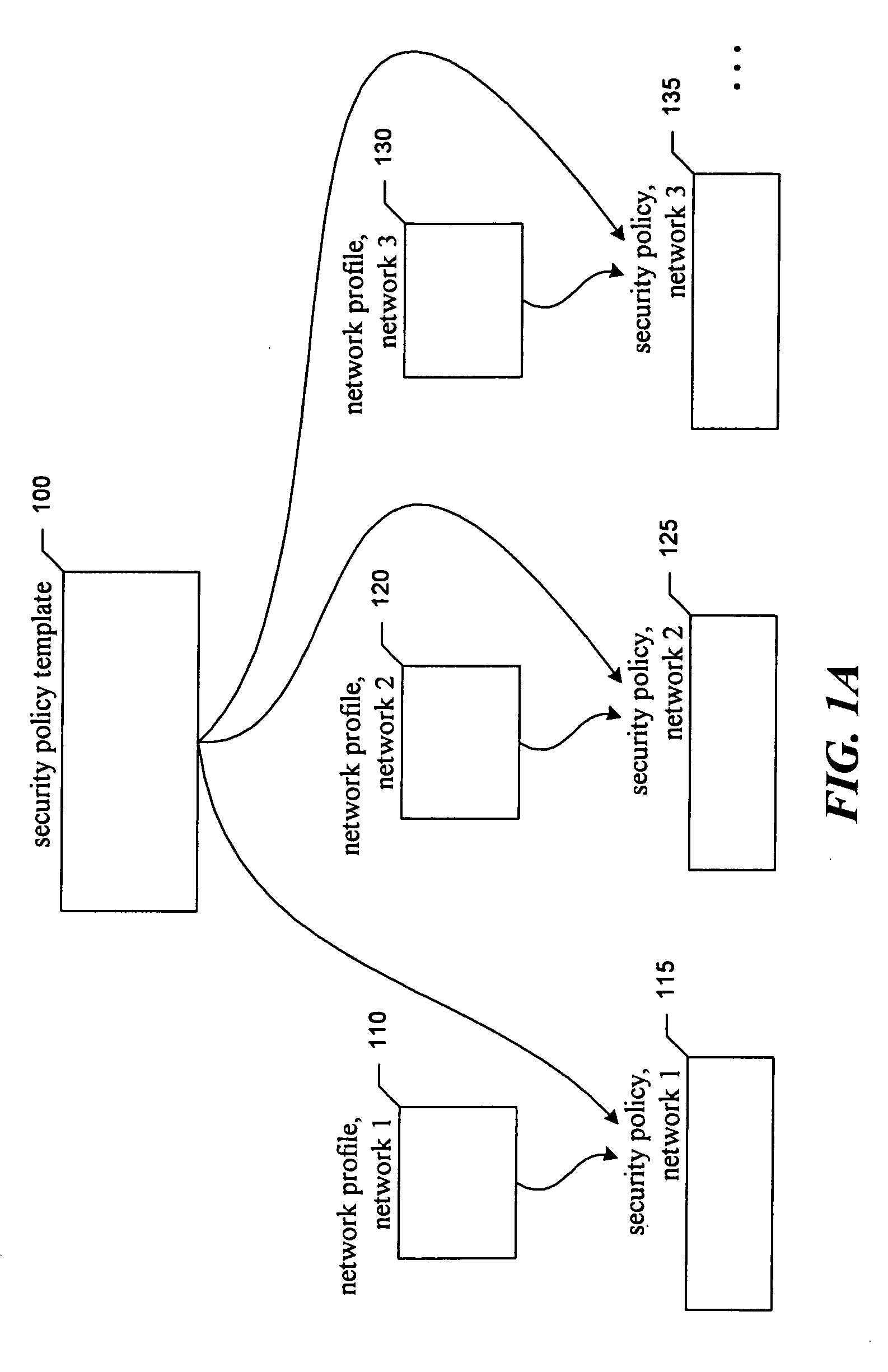
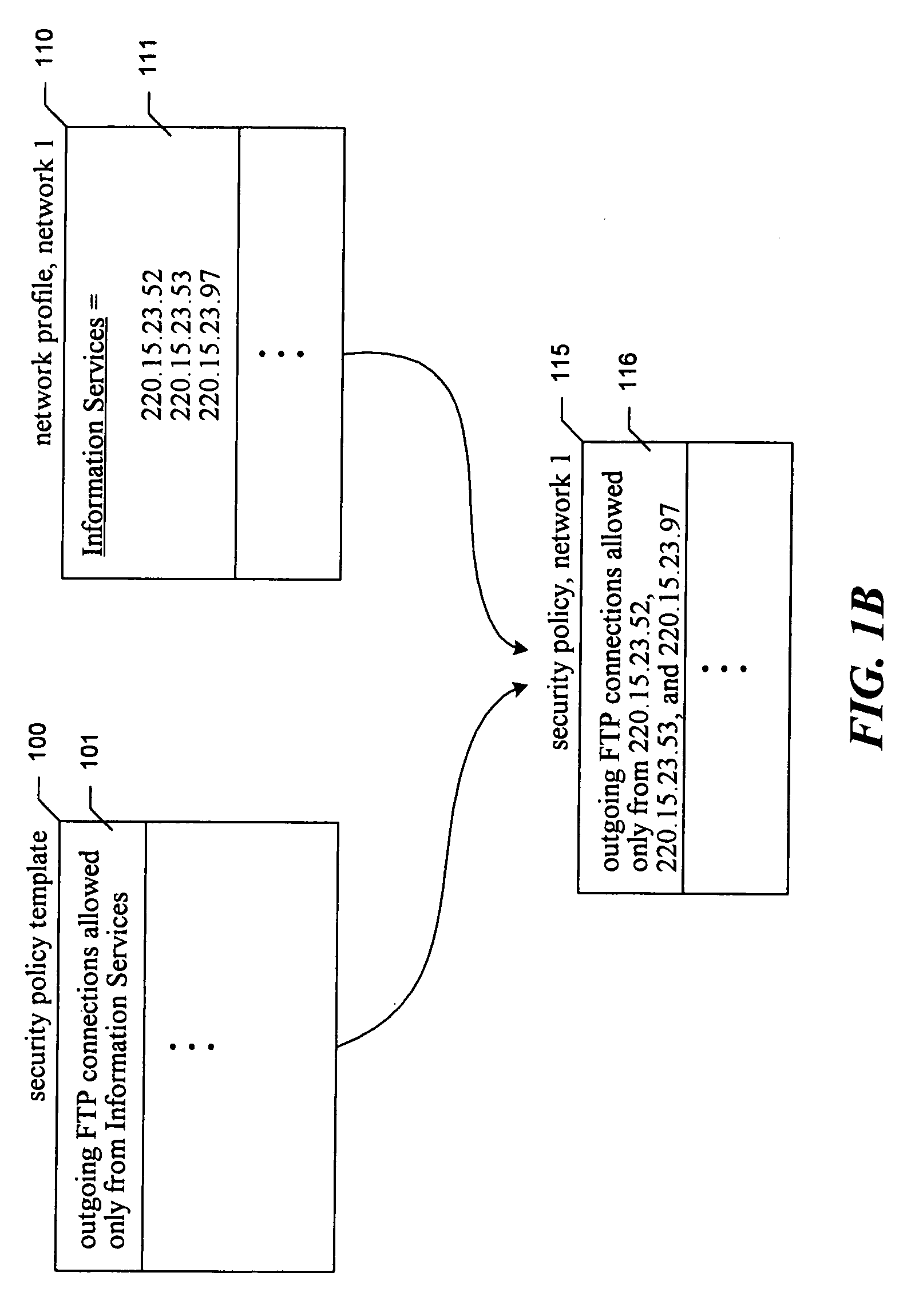
The present invention provides a software facility for implementing similar network security policies across multiple networks (“the facility”). Each network is a collection of network elements, including a network security device that protects the network by implementing a network security policy (hereinafter simply “policy”) within the network. While Firebox II network security devices provided by WatchGuard Technologies, Inc., of Seattle, Wash. are suggested for use with the facility, the facility preferably also operates with other network security devices available from other sources.
The policy implemented in a particular network comprises a set of rules for managing network traffic. These rules are specified in terms of specific network elements, such as user workstations, servers, routers, and printers, that perform certain functions, or “roles.” For example, a rule in a network security policy for a particular network may specify that all email traffic must flow through a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com