Block encryption method and schemes for data confidentiality and integrity protection
a technology of integrity protection and block encryption, applied in the field of secure data communication, can solve the problems of reducing performance or requiring additional power, prior-art block encryption schemes are less suitable for use in high-performance, low-power applications, and cannot be used in most real-time applications for embedded systems. the effect of low cos
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
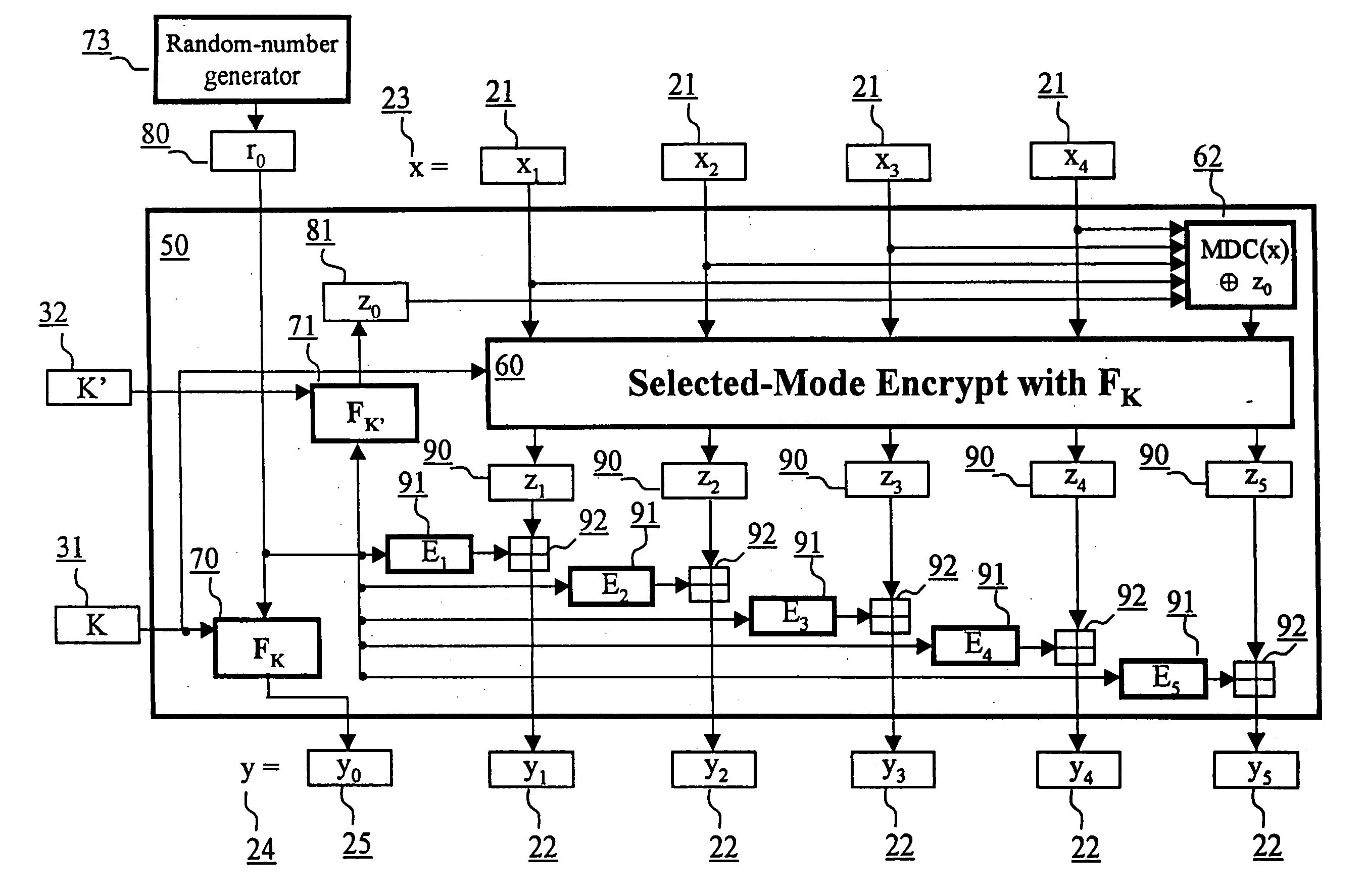
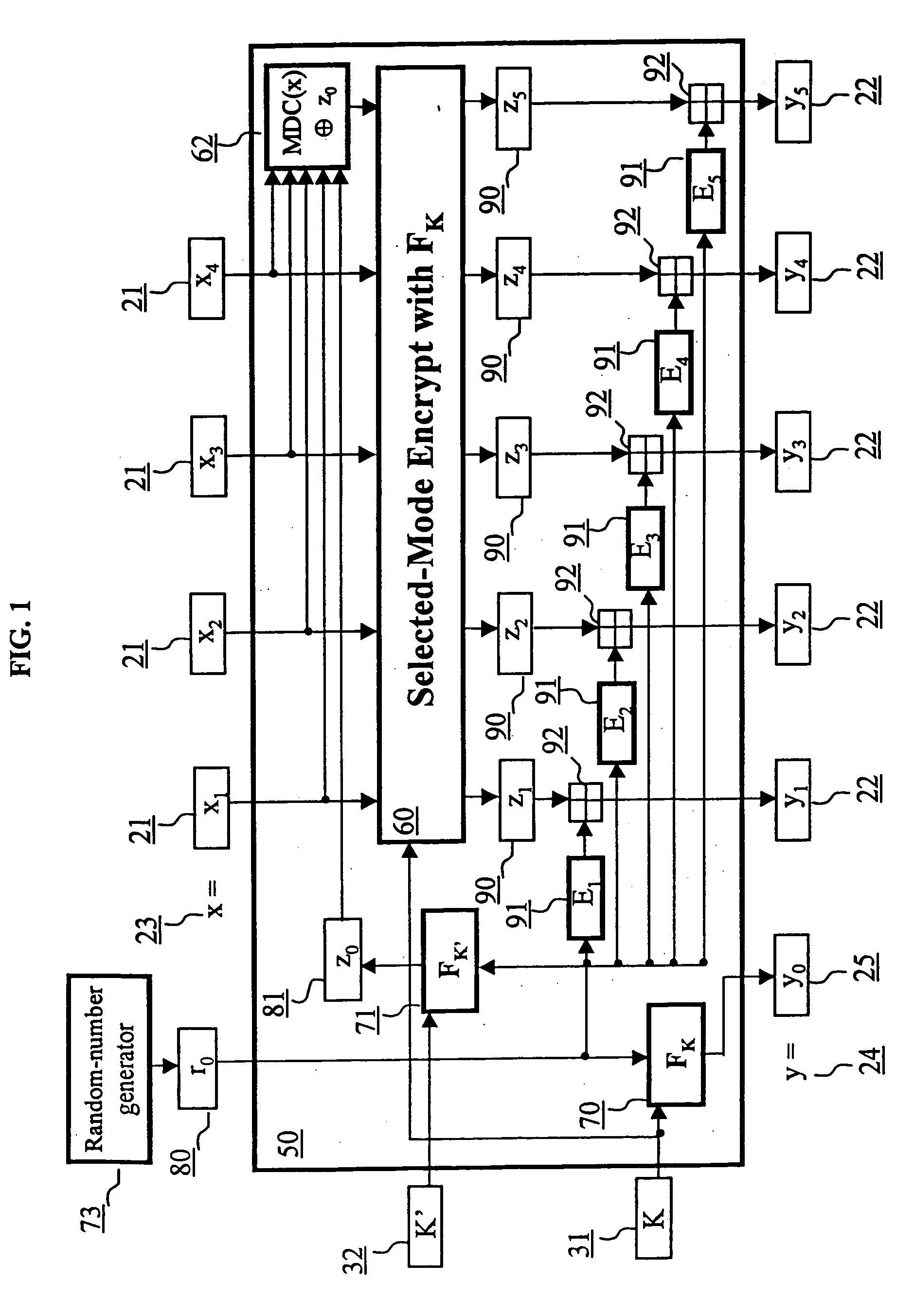
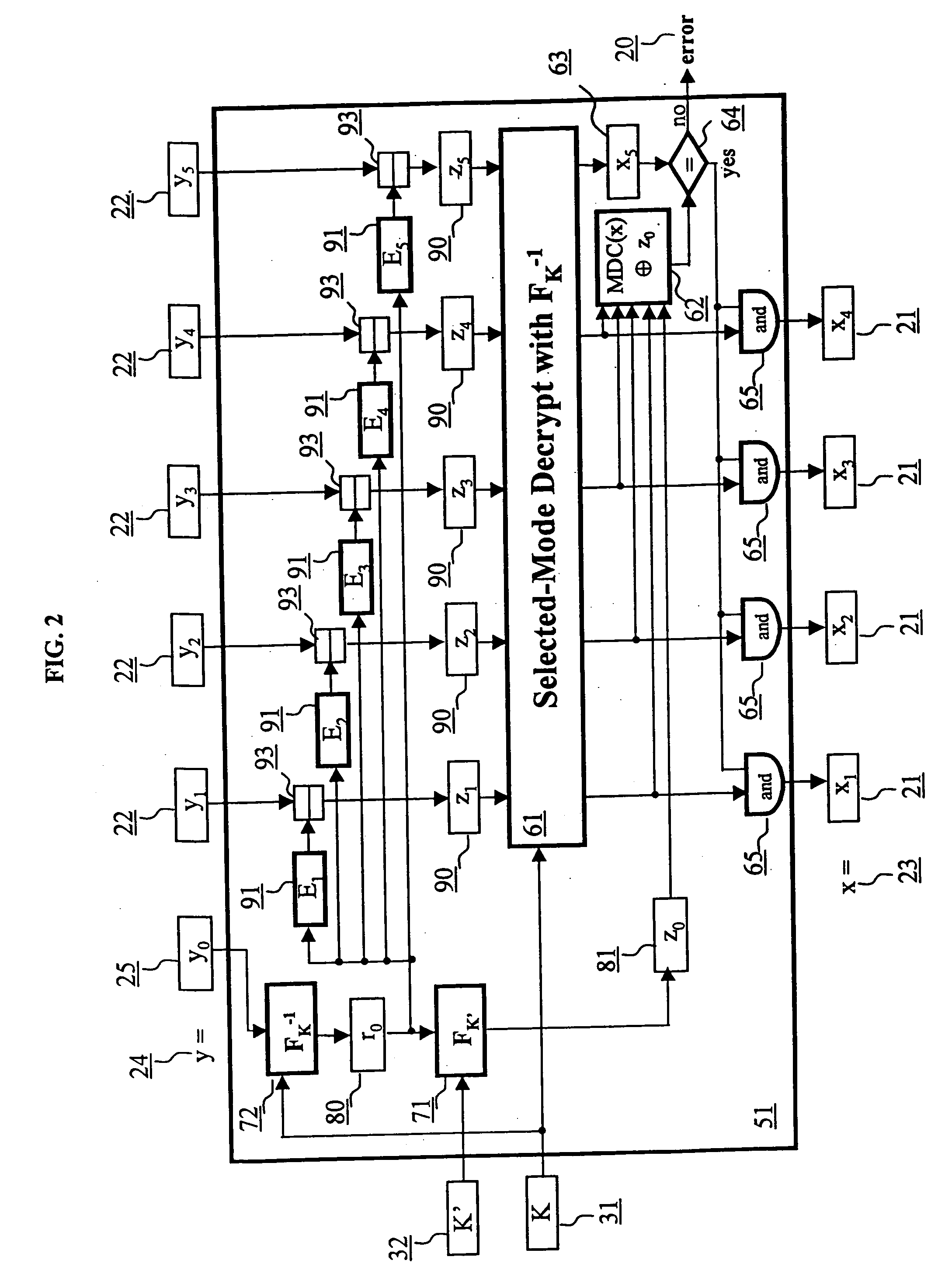
[0099] Referring to FIG. 1, a plaintext string x 23 representing the input data is presented to the encryption scheme providing data confidentiality and integrity 50 resulting in an output ciphertext string y 24. It is assumed that the sender and the receiver share a pair of secret keys K and K′ (i.e., a first key K 31, and a second key K′32) and that a random-number generator 73 is available. Keys K and K′ have the same length k and can be derived from a master key using key separation techniques well-known in the art. The input plaintext string x 23 is padded in some standard fashion so that it is a multiple of l bits. The padding is not shown in FIG. 1, as it is commonly known in the data processing art. It is assumed that the plaintext string x 23 is composed of n l-bit plaintext blocks 21. FIG. 1 shows an example plaintext string 23 composed of n=4 blocks, x=x1 x2 x3 x4.
[0100] In the description to follow, F is an l-bit block cipher with key length k, FK 70 is the l-bit block ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com