Identity authentication and secured access systems, components, and methods
a technology of identity authentication and access system, applied in the field of identity authentication system, can solve the problems of identity theft, misuse in unauthorized hands, and the technology currently available for identity security suffers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example 1
Digital Wallet Application
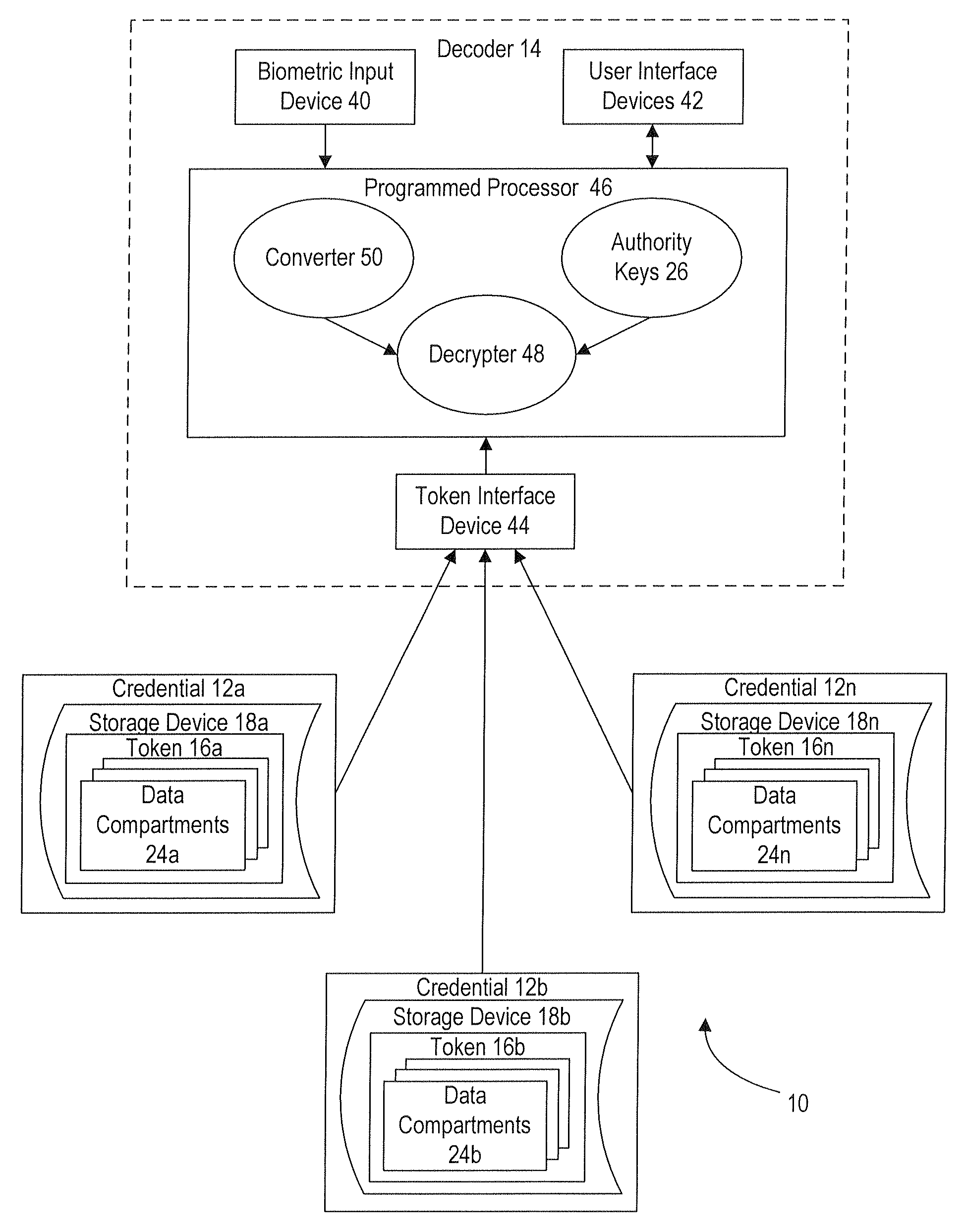
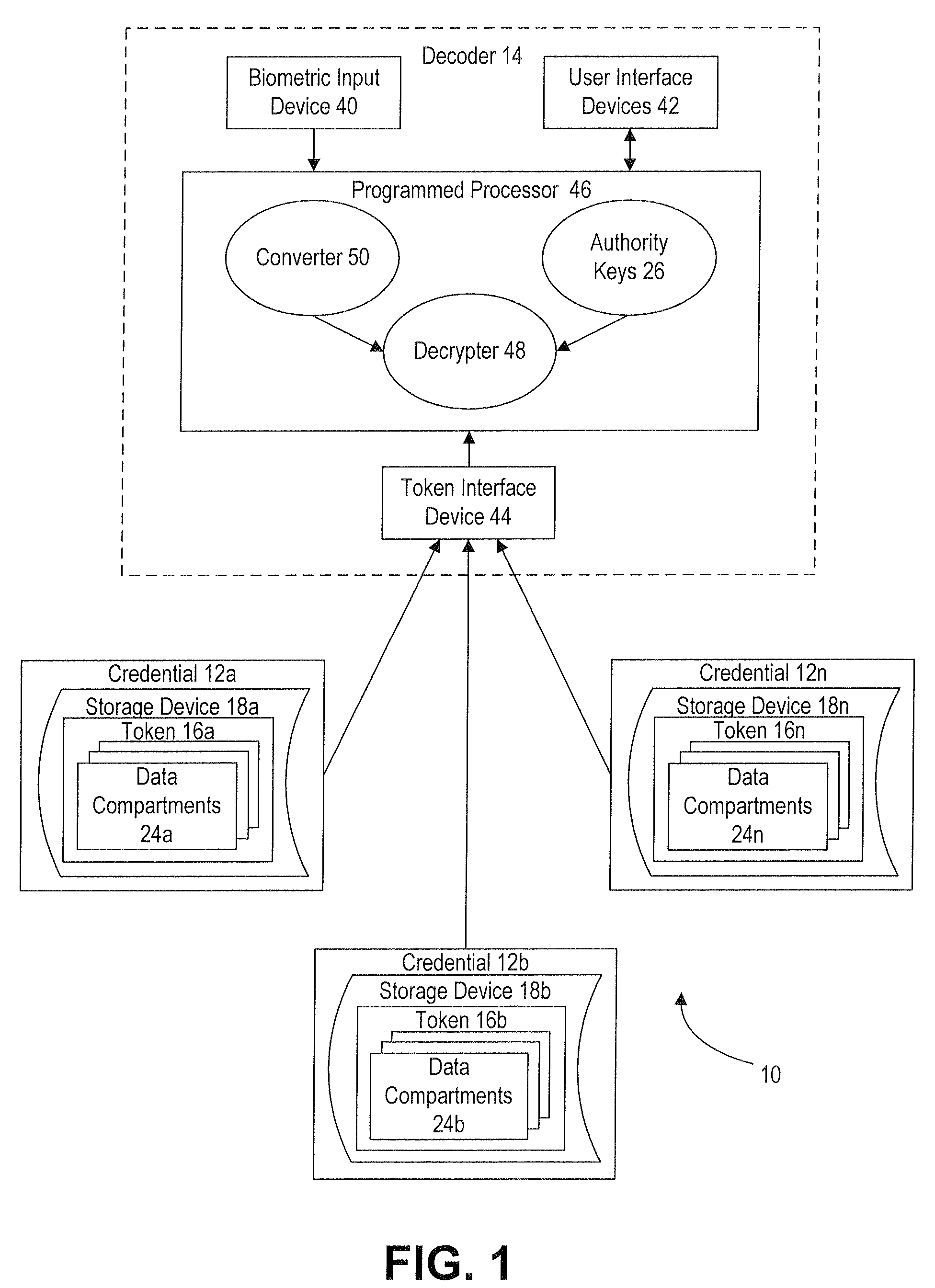
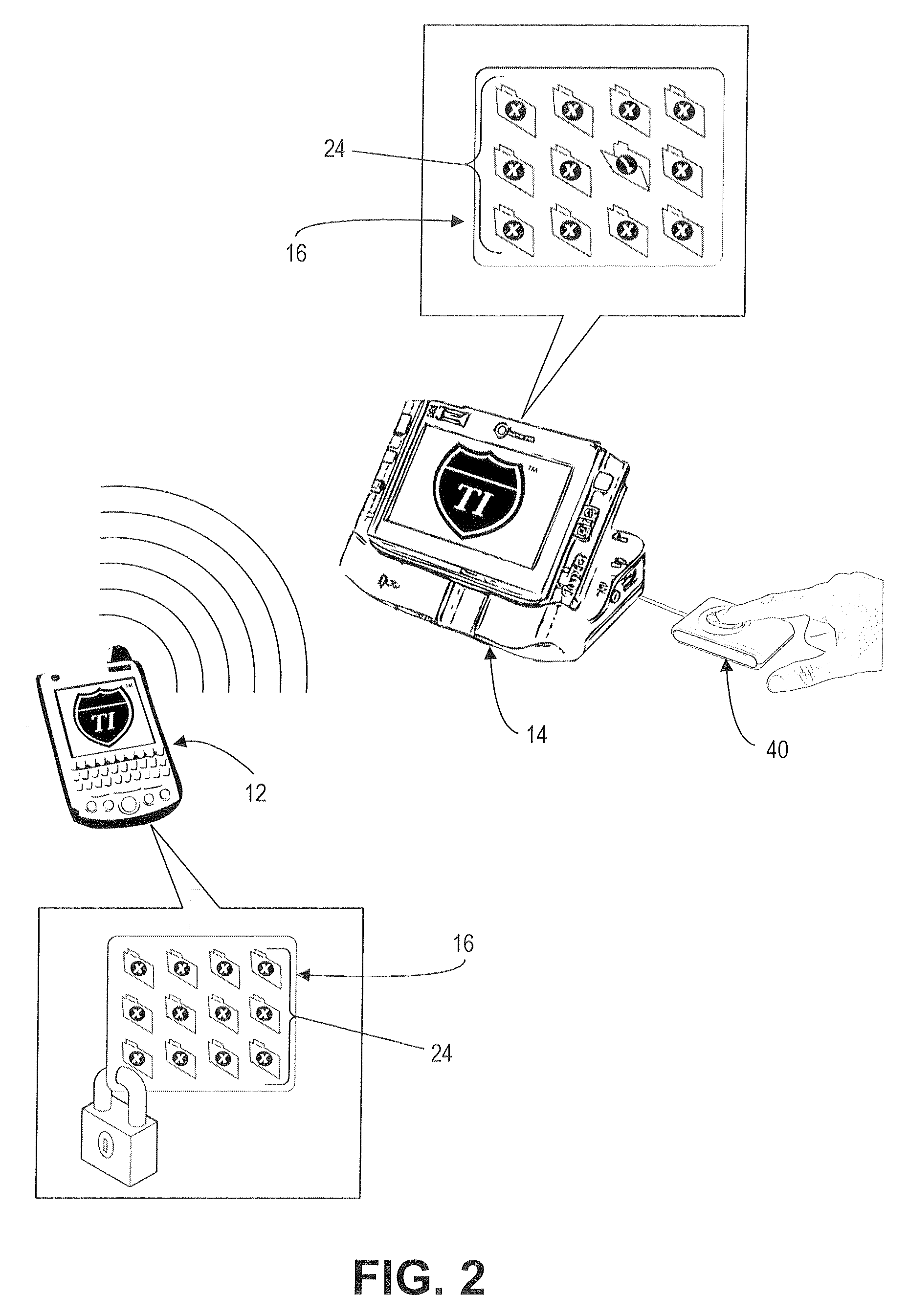
[0110]In typical commercial embodiments, digital wallet credentials are in the form of mobile phones, though they can be in the form of smart cards or other objects. The mobile phone credential stores the token, which includes account information for credit cards and other bank cards (check cards, debit cards, ATM cards, etc.). If desired, the token can include additional information typically carried by the user in a conventional wallet such as data on a driver's license, an employee pass or badge, an insurance card, gas or retailer card, frequent flyer card, retailer affinity card, and / or a movie rental card, as well as photographs of family and friends. As such, this is typically a “secured data” application in which the token includes one or more data compartments for storing the financial data with a higher degree of security.
[0111]In use, after the decoder accesses the secured data, the decoder displays (e.g., via a display screen or touch-screen user...
example 2
Medical Insurance Card Application
[0112]In this application the credentials provide insurers with the assurance that a patient claiming insurance coverage is actually the person insured. In typical commercial embodiments, the credentials are in the form of smart cards with a chip or plastic cards with a magnetic stripe or barcode, and the tokens secure the user's insurance information. As such, this is typically a “secured data” application in which the token includes one or more data compartments for storing the insurance data with a higher degree of security.
[0113]In use, a user presents an insurance card credential and a biometric identifier to a decoder in his doctor's office. After the decoder authenticates the token and the user and accesses the secured data, the patient's insurance information is transferred to the doctor's office records. The decoders can be connected (wirelessly or wired) to the local network in the doctor's office so that the insurance data is electronical...
example 3
Medical Passport Application
[0114]In this application the credentials help reduce errors when providing medical services. In typical commercial embodiments, the credentials are in the form of smart cards with a chip, plastic cards with a magnetic stripe, or flash (thumb) drives, and the tokens secure instructions relating to medial services prescribed for the user. As such, this is typically a “secured data” application in which the token includes one or more data compartments for storing the medical instructions data with a higher degree of security.
[0115]When medical services are prescribed, the doctor uses a set-up workstation or decoder to issue the credential and enter all of the prescribed orders into the credential's token. Each order is typically secured in an individual data compartment of the token so that for example a lab will only have the authority level on its decoder to access the doctor's orders for the lab, and the lab will not have access to any other information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com