Information processing apparatus, control method for the same, program and storage medium
a technology of information processing and control method, applied in the field of setting private information, can solve the problems of inability to maintain security in preventing falsification, inability to modify, and inability to really be modified
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
Apparatus Configuration
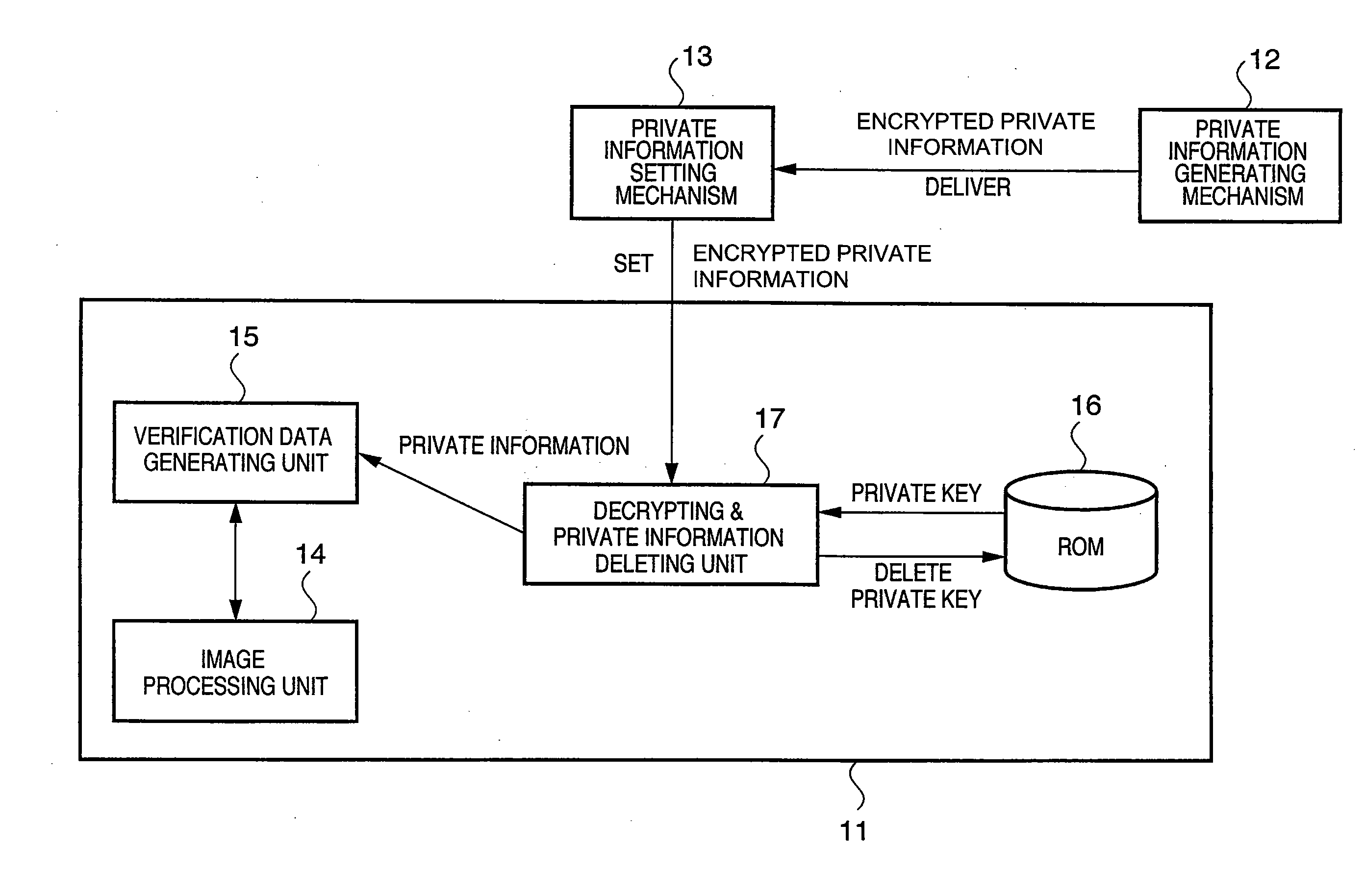
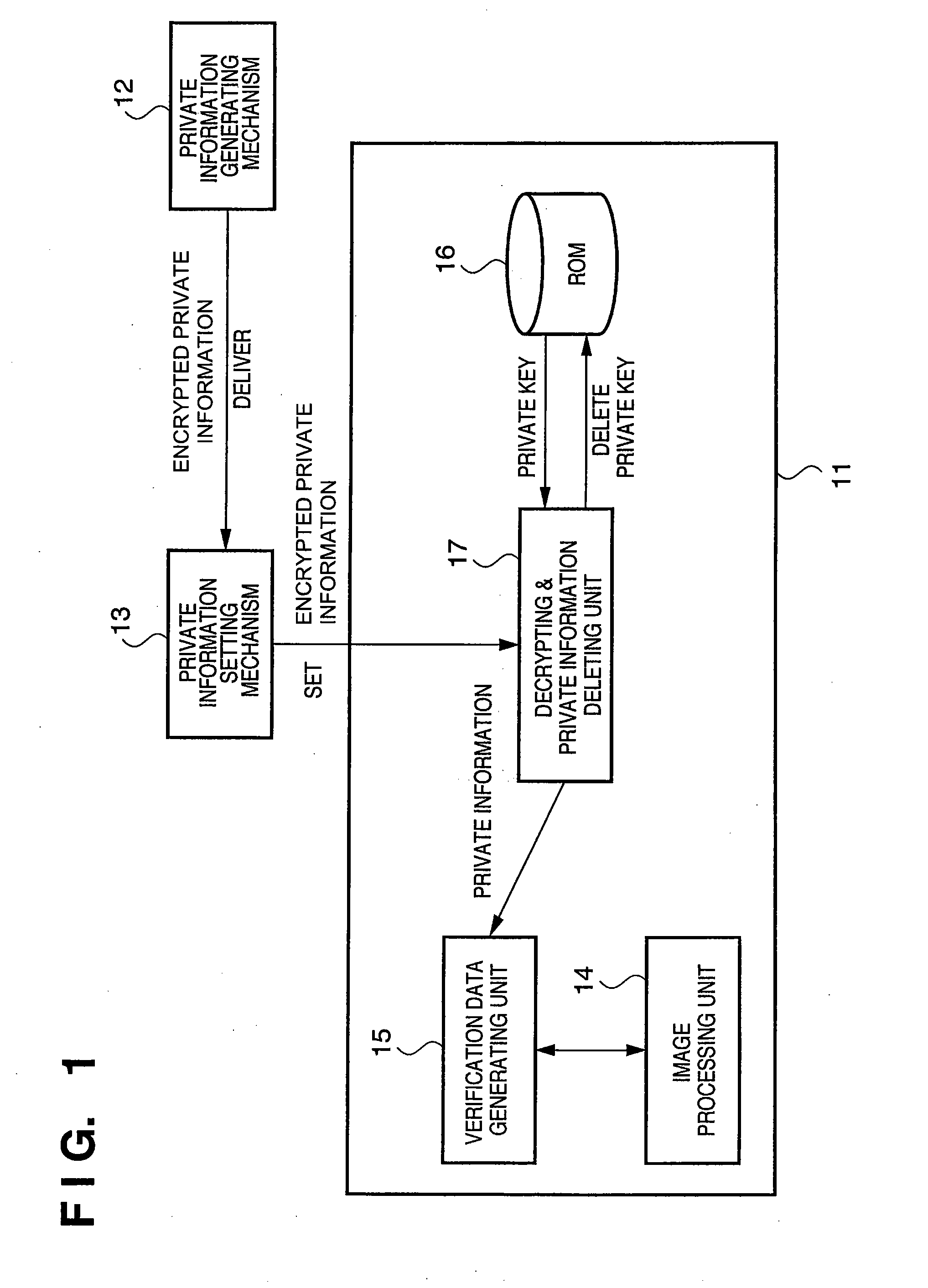
[0045]FIG. 1 is a block diagram showing an exemplary system configuration that includes an information processing apparatus according to the present embodiment. As shown in FIG. 1, in the present embodiment there exists an image generating apparatus 11 as an information processing apparatus according to the present embodiment, a private information generating mechanism 12, and a private information setting mechanism 13.
[0046](Image Generating Apparatus 11)
[0047]The image generating apparatus 11 basically has the functional configuration of an image processing unit 14, a verification data generating unit 15, a ROM 16, and a decrypting & private information deleting unit 17.
[0048]The image processing unit 14 has a function of generating / shooting image data, a function of generating auxiliary parameters, and a function of generating image files with verification data. Incidentally, in the case where the image generating apparatus 11 is a camera, auxiliary paramet...
second embodiment
[0130]In the first embodiment, the confirmation of the validity of a password or biological information input externally was shown as an example of an action that triggers the execution of the decrypting & private information deleting unit 17 in the camera 11. However, it is conceivable that usability is impaired because of the operations for inputting passwords or the like differing from normal operations. Note that verification data cannot be created as long as decryption and private key deletion has not been executed, as mentioned above. Thus, in the configuration according to the present embodiment, an operation that is definitely performed on the camera 11 is made the trigger for executing decryption and private key deletion, given that it is sufficient if verification data can created before the user first takes a shot. This enables usability to be improved.
[0131]Since the configuration according to the present embodiment is largely similar to the configuration according to th...
third embodiment
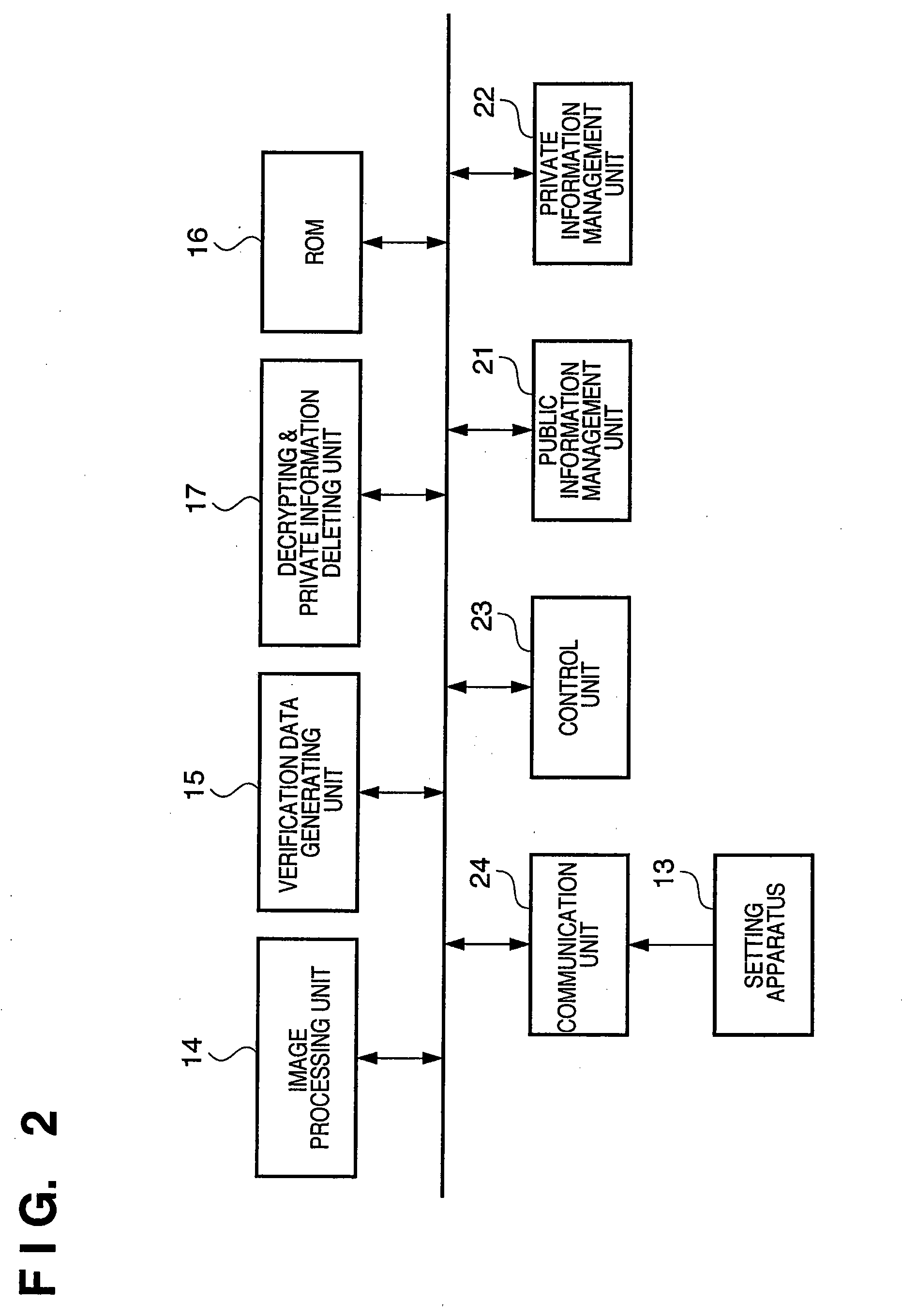
[0140]Firstly, an outline of the processing of the configuration according to the first and second embodiments is summarized with reference to FIG. 12. FIG. 12 is a block diagram schematically showing an outline of the processing of the configuration according to the first and second embodiments.
[0141]As described above, the generating apparatus 12 generates the private information K by inputting the public information I and the private key P′ into the function E( ) and encrypts the generated K using the private key P to create the private information EK. Next, the generating apparatus 12 delivers EK to the setting apparatus 13 via a channel whose security is not guaranteed.
[0142]The setting apparatus 13, on receipt of the encrypted private information EK, sets EK in the camera 11.
[0143]Finally, the camera 11, when triggered by a prescribed action, performs controls to decrypt EK using the private key P and acquire the private information K, and to delete the private key P from memo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com