Security system
a security system and security technology, applied in the field of premises security systems and methods, can solve problems such as difficult installation, inability to adapt to changing security needs, and inability to easily scale up or down
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
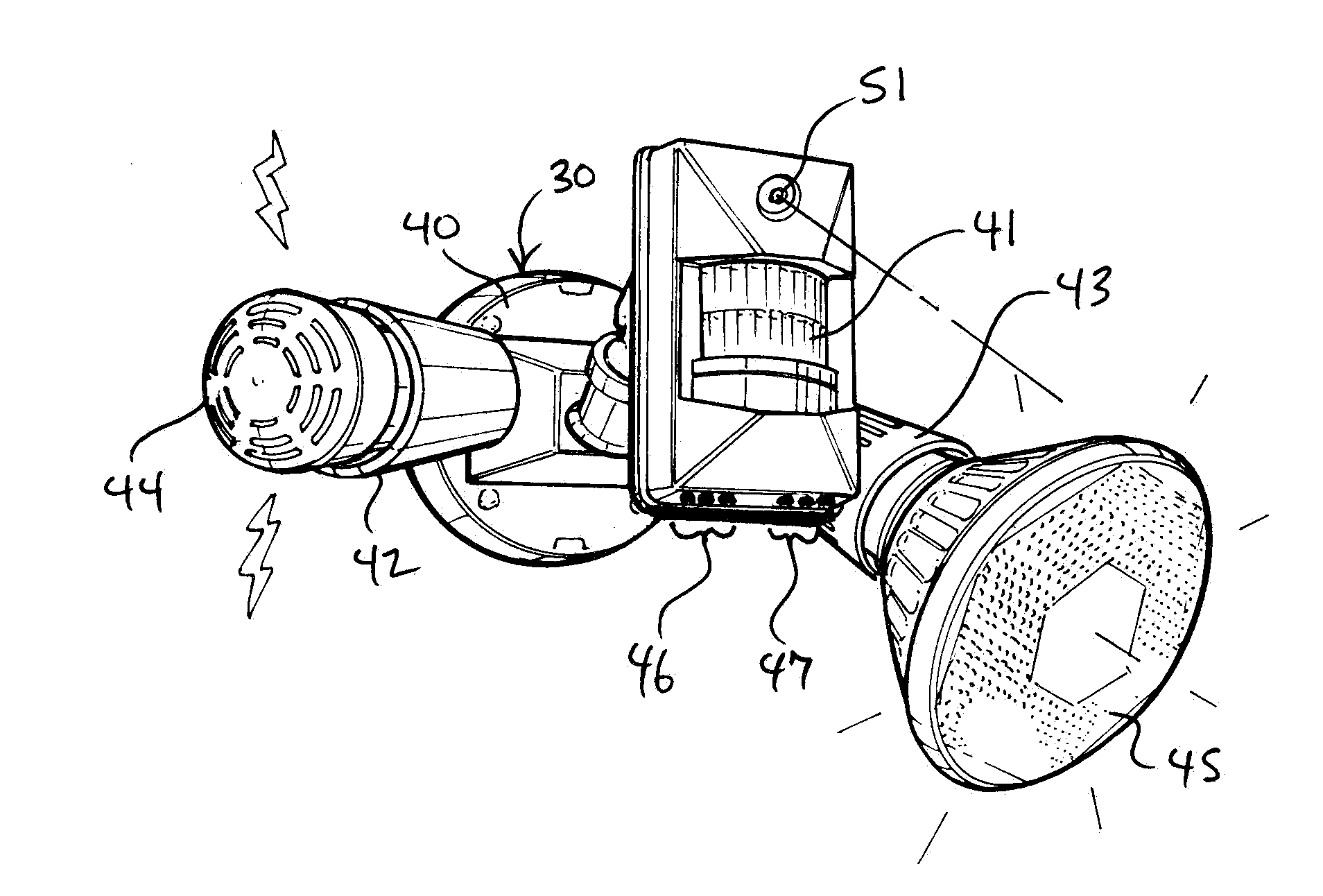
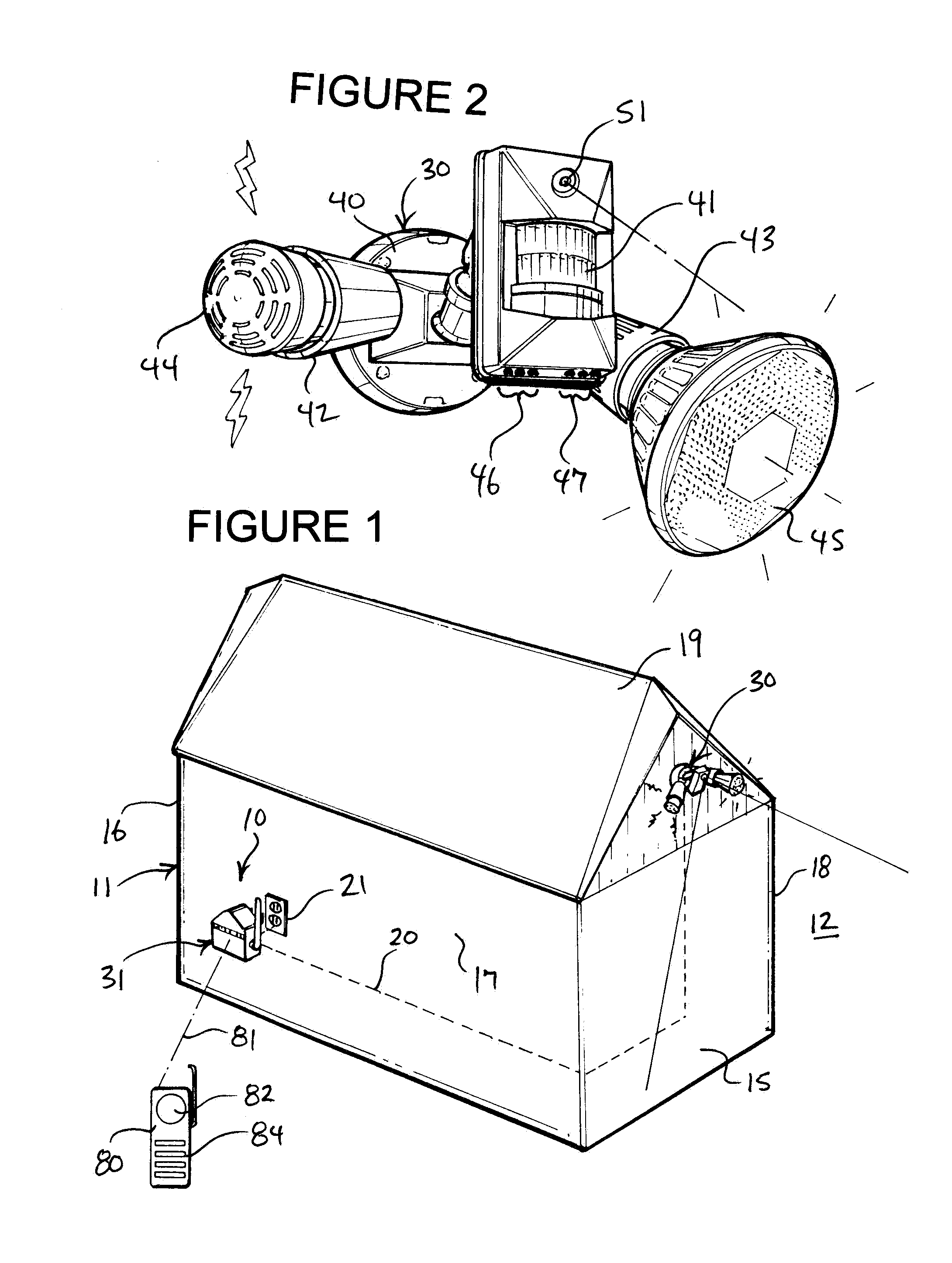
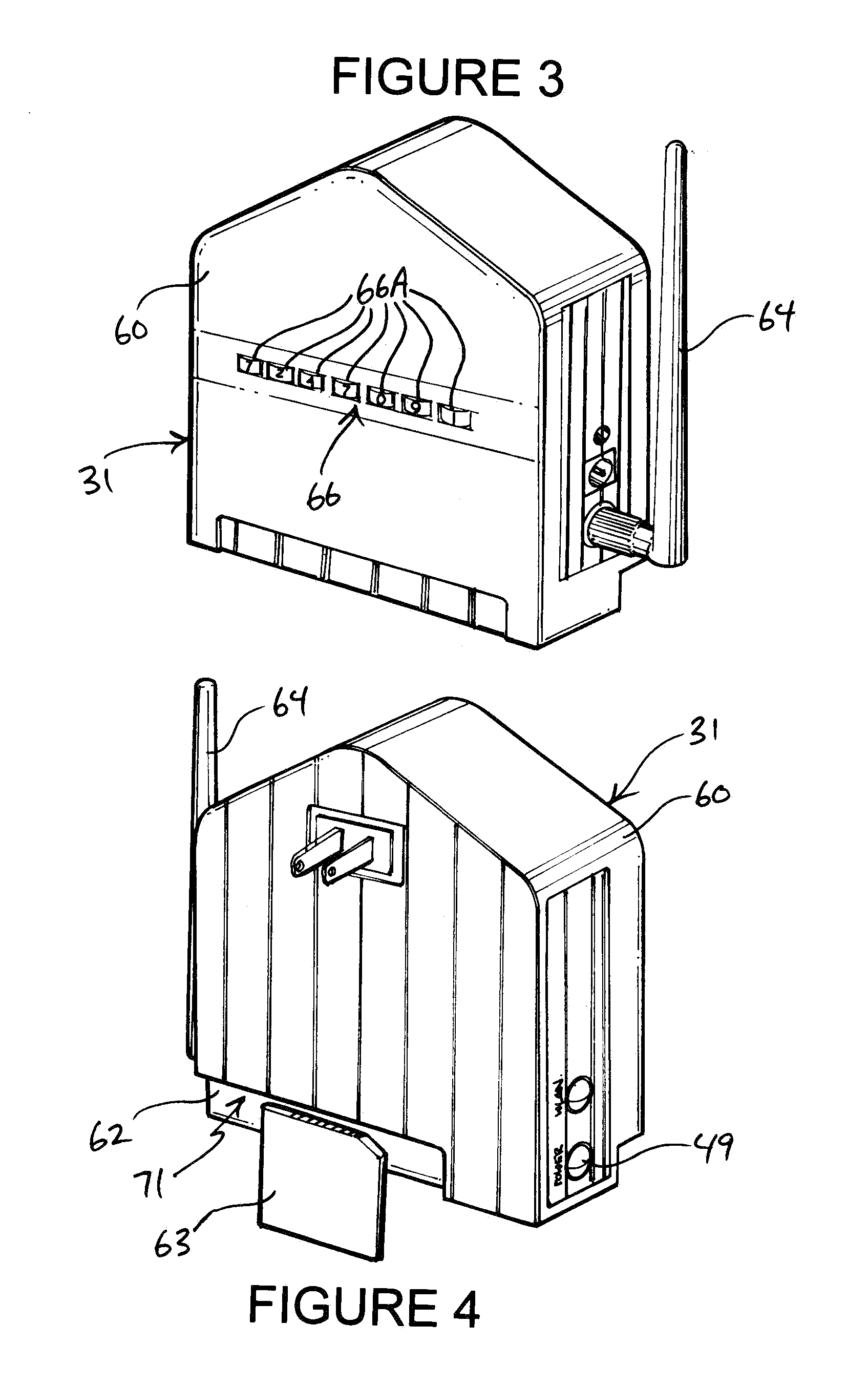
[0015]Turning now to the drawings, in which like reference characters indicate corresponding elements throughout the several views, attention is first directed to FIG. 1 in which there is seen a partially schematic perspective view of a security system 10 incorporated with a building 11 for providing security in a vicinity 12 of building 11. In FIG. 1, building 11 is a man-made structure used or intended for supporting or sheltering any use or continuous occupancy, and is constructed of conventional and readily available building materials and techniques. For orientation and reference purposes, building has opposed front and rear ends 15 and 16 and opposed sides 17 and 18 formed by upstanding walls, and a roof 19 forming the top covering of building 11, the purpose of which is primarily to shed water from building 11 and to shelter the interior of building 11. According to conventional practice, building 11 is fashioned with electrical wiring for conducting alternating current elect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com