Personal security system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
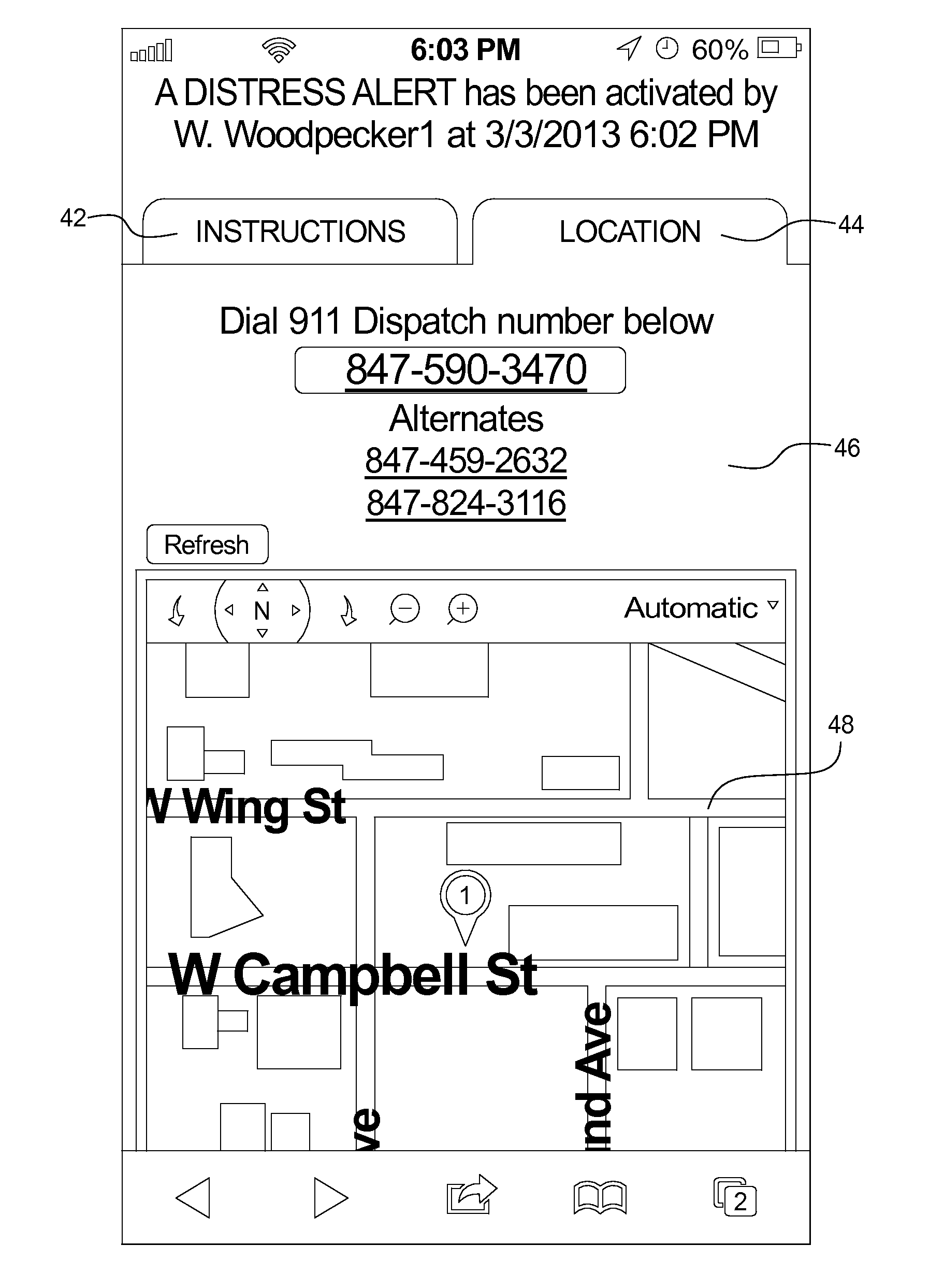
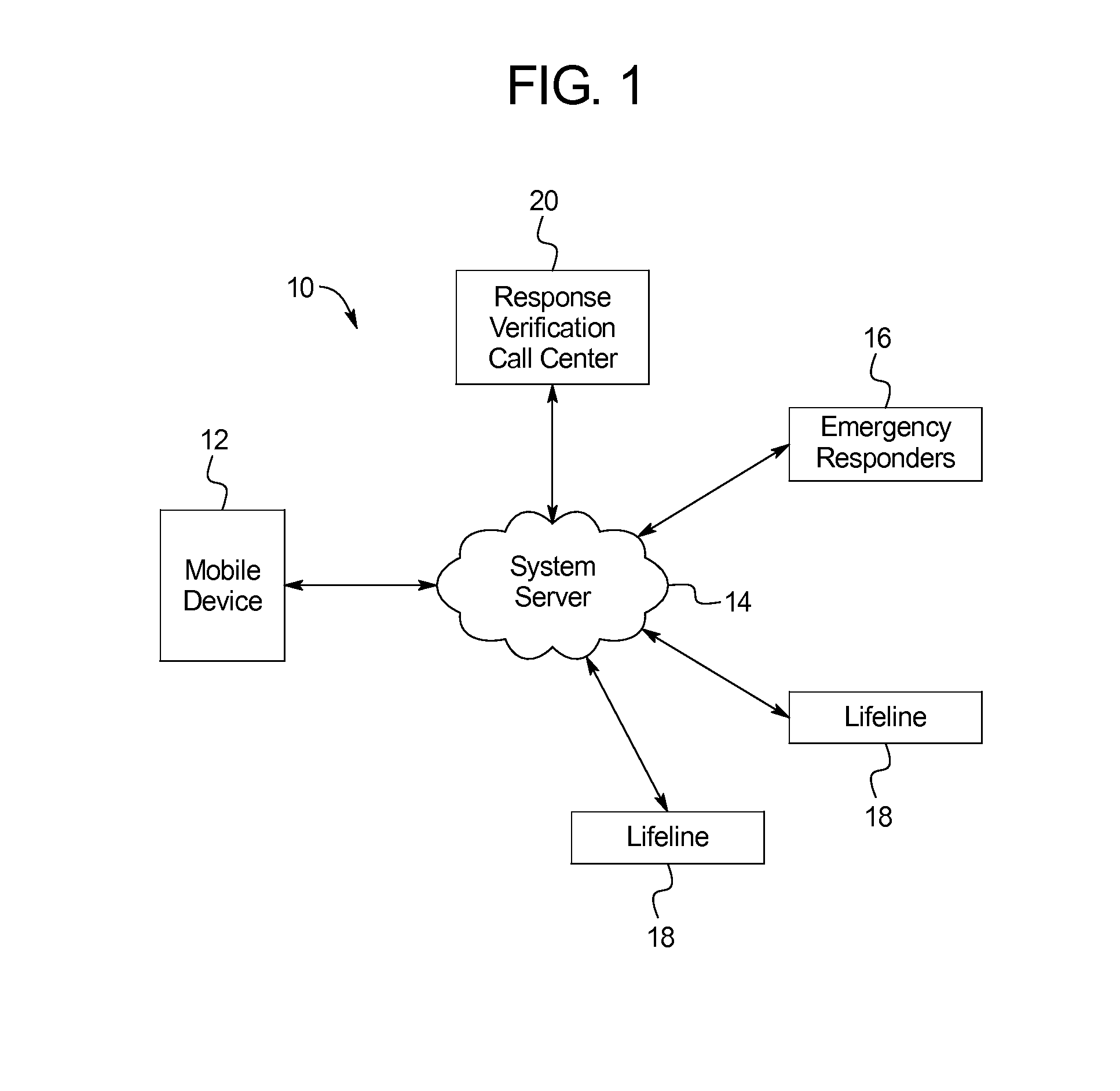
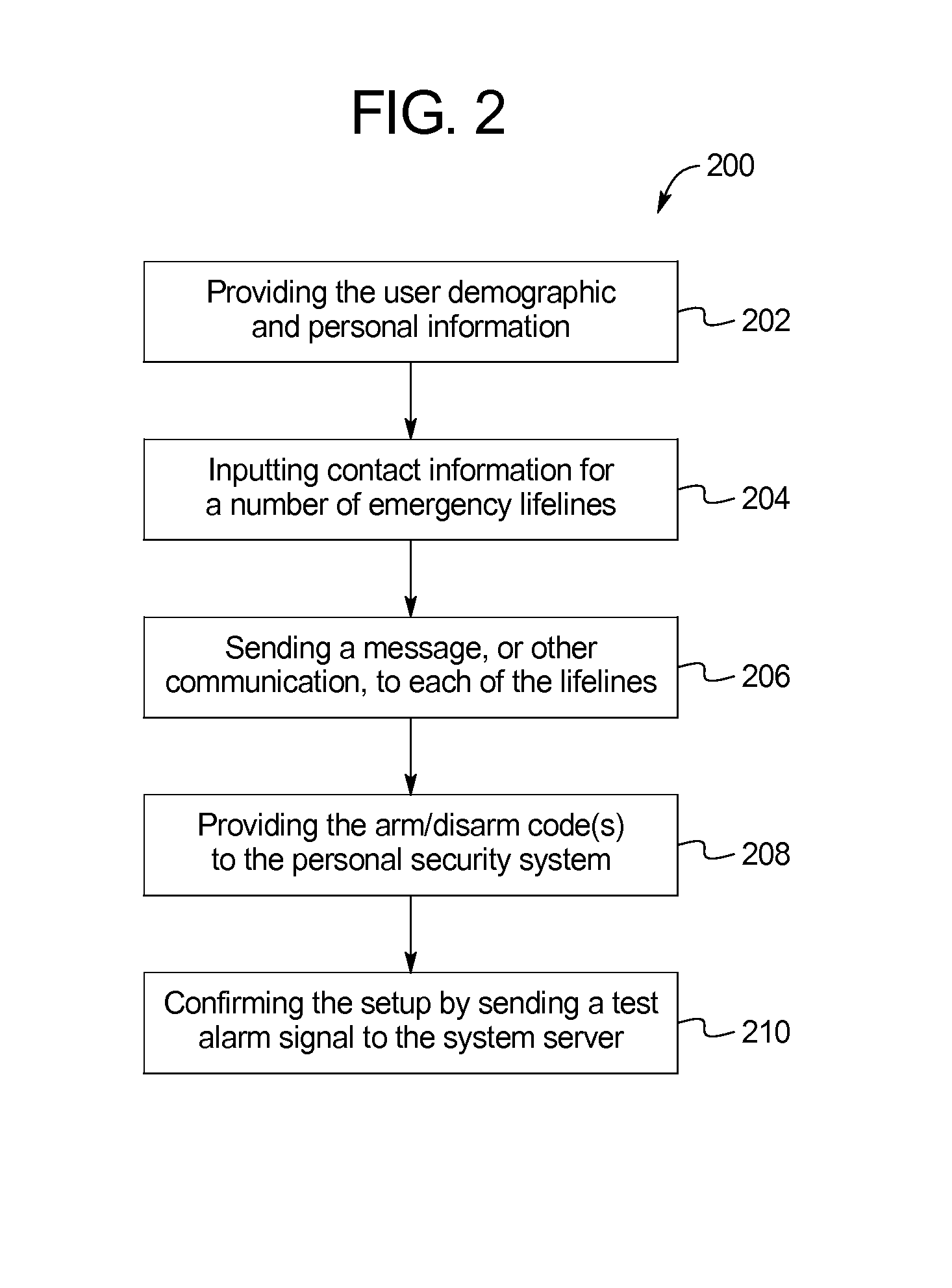
[0058]FIG. 1 illustrates an example of a personal security system 10. As shown in FIG. 1, the personal security system 10 may include a mobile device 12 in communication with a system server 14. Further, the system server 14 may be in communication with one or more emergency responders 16 and one or more lifelines 18 (as used herein, lifelines are user defined contacts that are contacted in case of an emergency event). As shown, the system server 14 may be associated with a response verification call center 20 through which one or more operators / representatives may interact with the system 10.
[0059]In some examples, the mobile device 12 may be in one-way communication with the system server 14 (e.g., syncing setup information and communicating alarm conditions). Of course, in other embodiments, the mobile device 12 may be in two-way communication with the system server 14 (e.g., syncing setup information and communicating alarm conditions, as well as, confirming receipt of informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com