Robust Header Compression Processing Method and Robust Header Compression Processor
a header compression and processing method technology, applied in the field of mobile communication, can solve the problems of wasting wireless resources, wasting wireless resources, and reducing so as to improve the efficiency of compression and decompression, robust header compression, and the utilization rate of wireless link bandwidth
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
embodiment 1
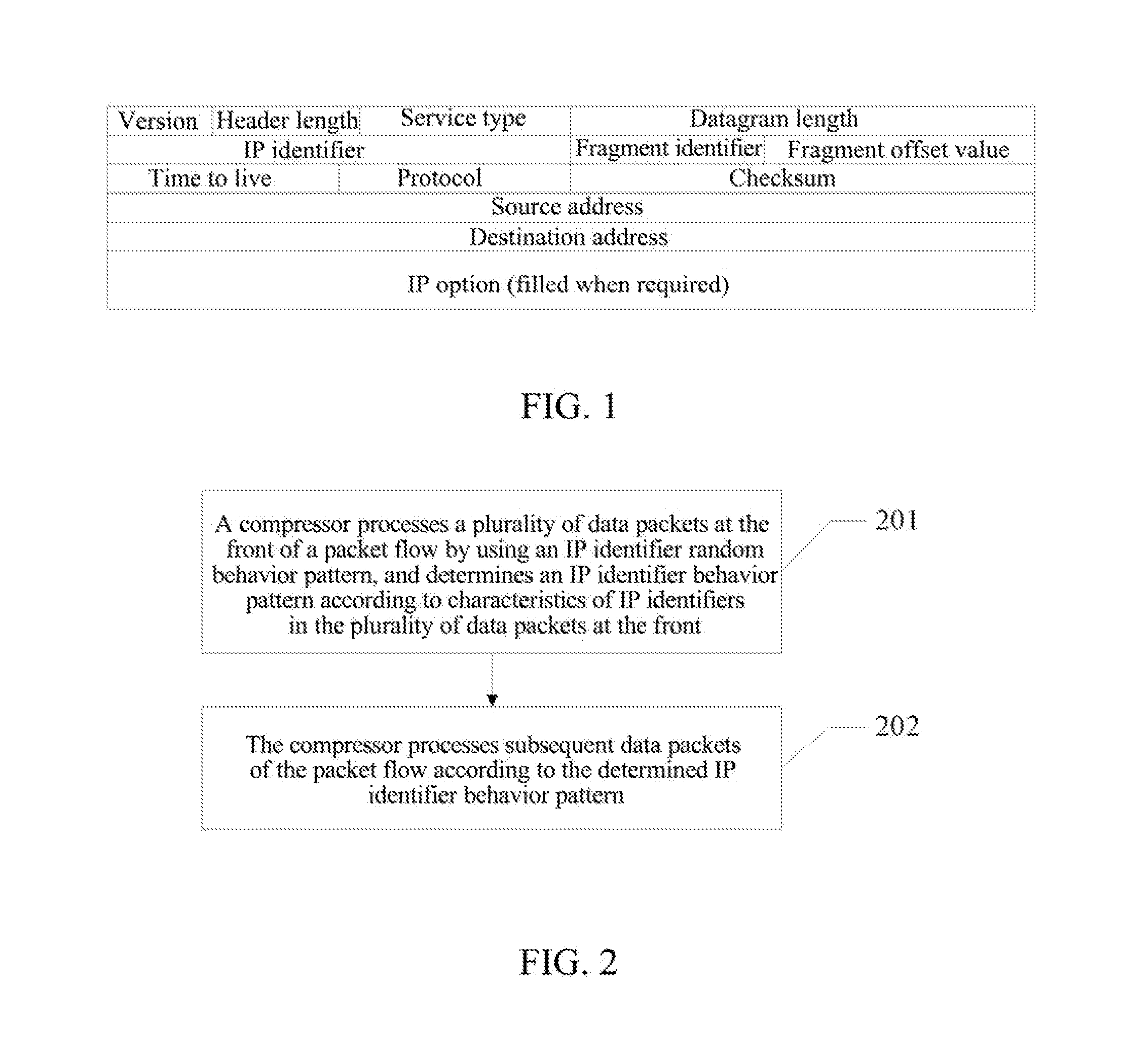
[0068]As shown in FIG. 2, the robust header compression processing method in the embodiment 1 of the present document includes the following steps.
[0069]In step 201, a compressor processes a plurality of data packets at the front of a packet flow by using an IP identifier random behavior pattern, and determines an IP identifier behavior pattern according to characteristics of IP identifiers in the plurality of data packets at the front.
[0070]The step of determining an IP identifier behavior pattern according to characteristics of IP identifiers in the plurality of data packets at the front includes:
[0071]if a first condition that the IP identifiers in the data packets increase continuously and a number of data packets with continuously increasing times reaches a first threshold value is satisfied, determining as an IP identifier incremental behavior pattern;
[0072]if a second condition that the IP identifiers in the data packets keep static continuously and a number of data packets k...
embodiment 2
[0080]In the scheme, identification of a specific behavior of the IPID is implemented by setting an identifier and accumulating three counters.
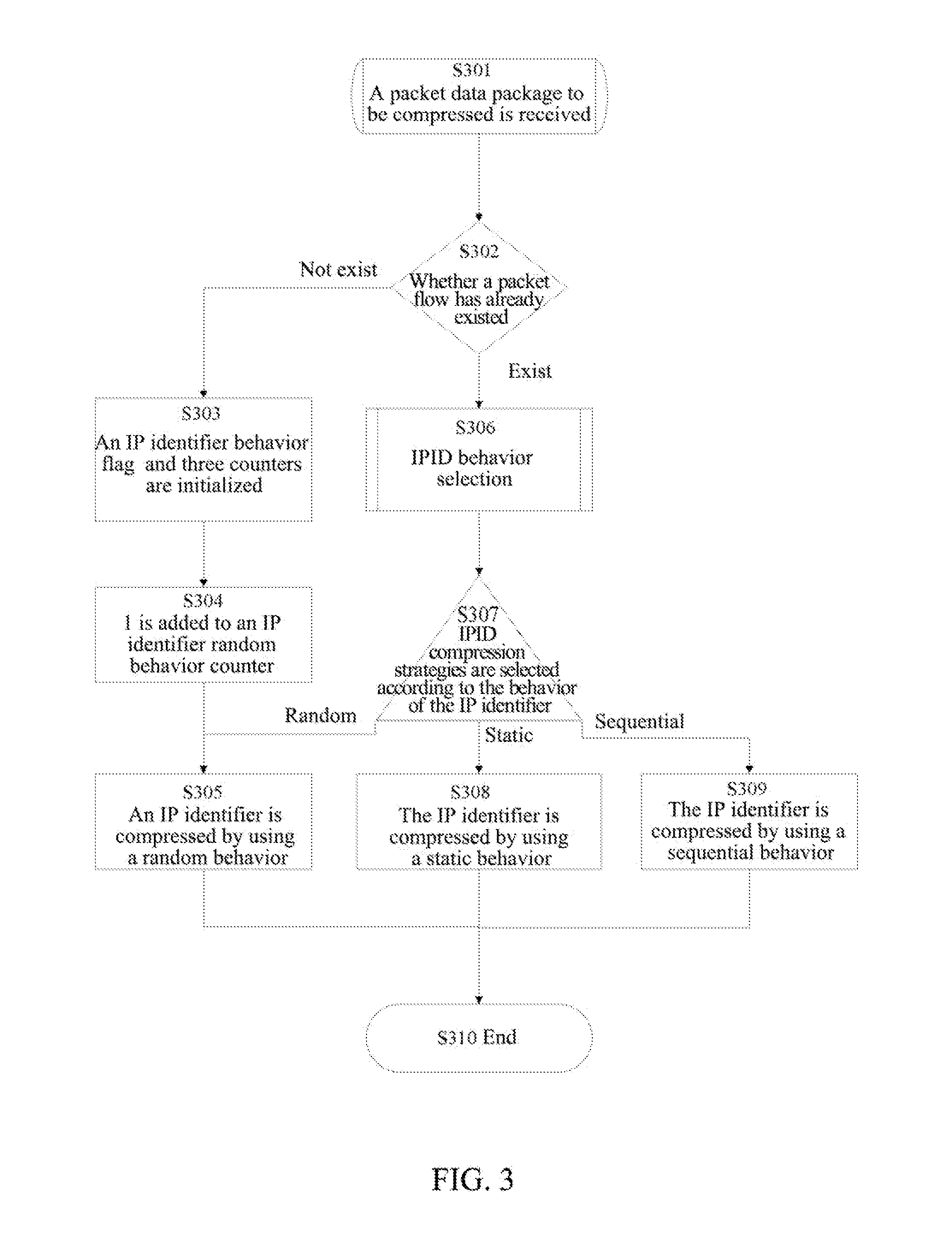
[0081]An implementation scheme of IP identifier behavior identification and IP identifier compression involved in the present document will be further described in detail in combination with FIG. 3 and FIG. 4 below, and the followings steps are included.
[0082]In step S301, a compressor receives a packet data package to be compressed, and it is to proceed to step S302.
[0083]In step S302, it is judged whether the packet flow has already existed, if the packet flow does not exist, it is to proceed to step S303, and if the packet flow exists, it is to proceed to step S306.
[0084]In step S303, an IP identifier behavior flag (BehaviorFlag) and three counters, an IP identifier random behavior counter IP rnd, an IP identifier static behavior counter Count_const and an IP identifier sequential behavior counter Count_seq, are initialized, and it is to p...
embodiment 3
[0123]In this scheme, identification of a specific behavior of the IPID is implemented by setting an identifier and accumulating two counters. Compared with the foregoing embodiment 2, in the embodiment 3, the flows corresponding to FIG. 3 are basically the same, the difference only lies in the step S303, only the Behavior Flag and the 2 counters, Count_const and Count_Seq, are initialized, and the step S304 is not executed, the process of selecting IP identifier behaviors is executed, and as shown in FIG. 5, the following steps are specifically included:
[0124]In step S501, when a compressor receives a packet package to be compressed and the packet flow has existed, it is to proceed to step S502.
[0125]In step S502, it is judged whether a Behavior Flag is 0, if the Behavior Flag is not 0, it is to proceed to step S503, and if the Behavior Flag is 0, it is to proceed to step S504.
[0126]In step S503, a behavior of the IPID identified by the Behavior Flag is recorded into an IpidBehacio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com