Mobile peer-to-peer authenticated transfers
a peer-to-peer authenticated and mobile technology, applied in the field of mobile peer-to-peer authenticated transfers, can solve the problems of lack of aesthetics, unattractive barcodes, and methods commonly employed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
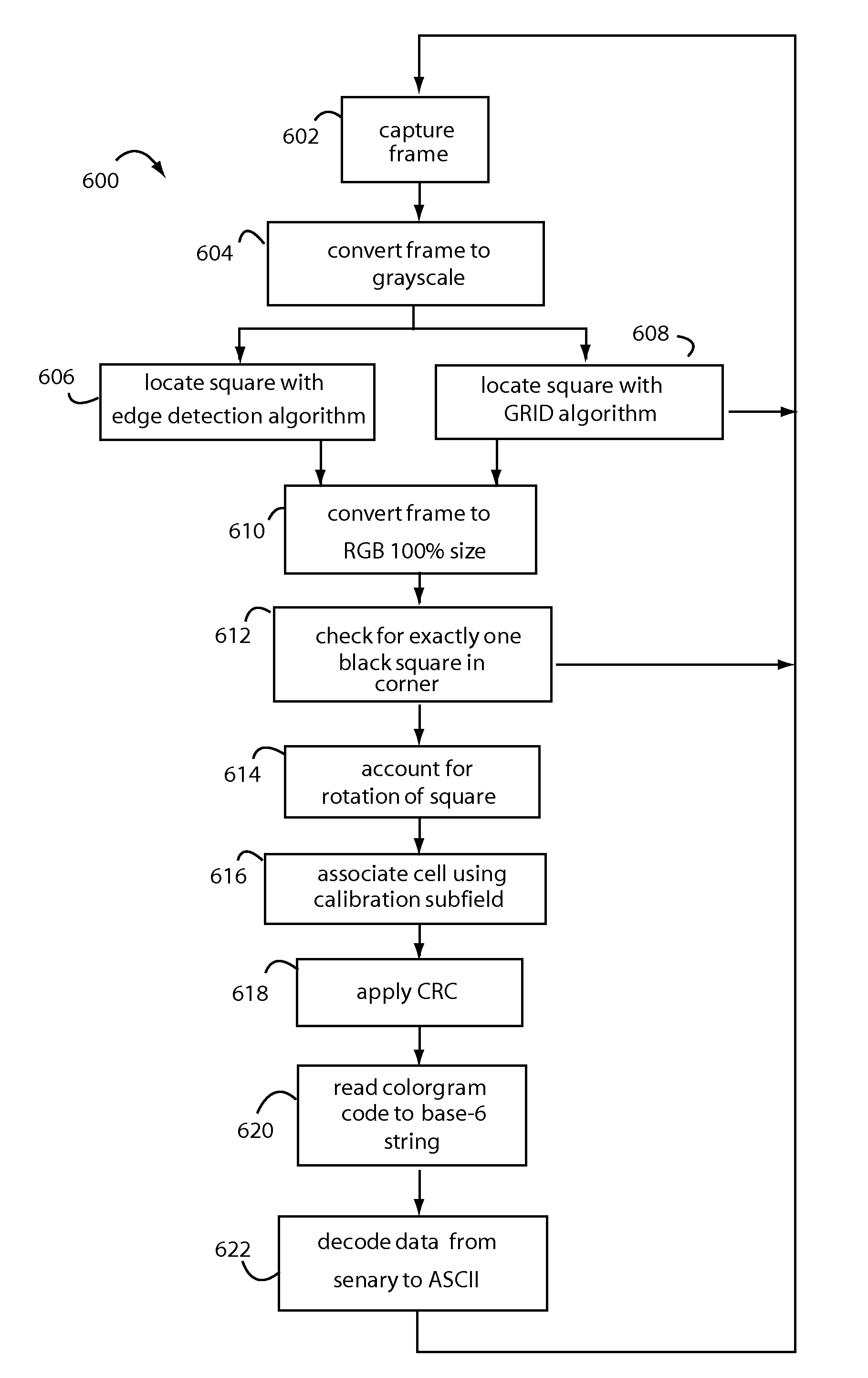
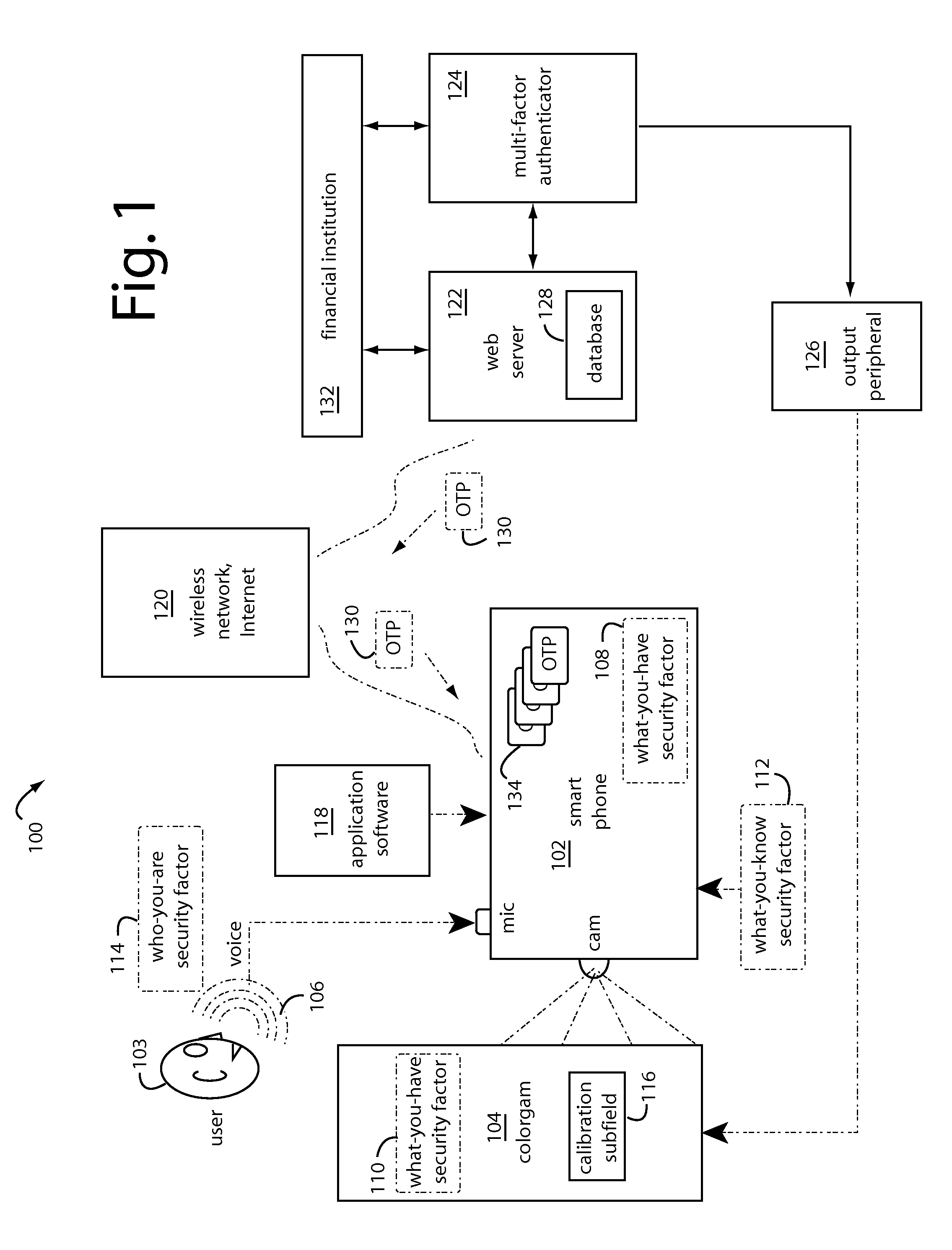
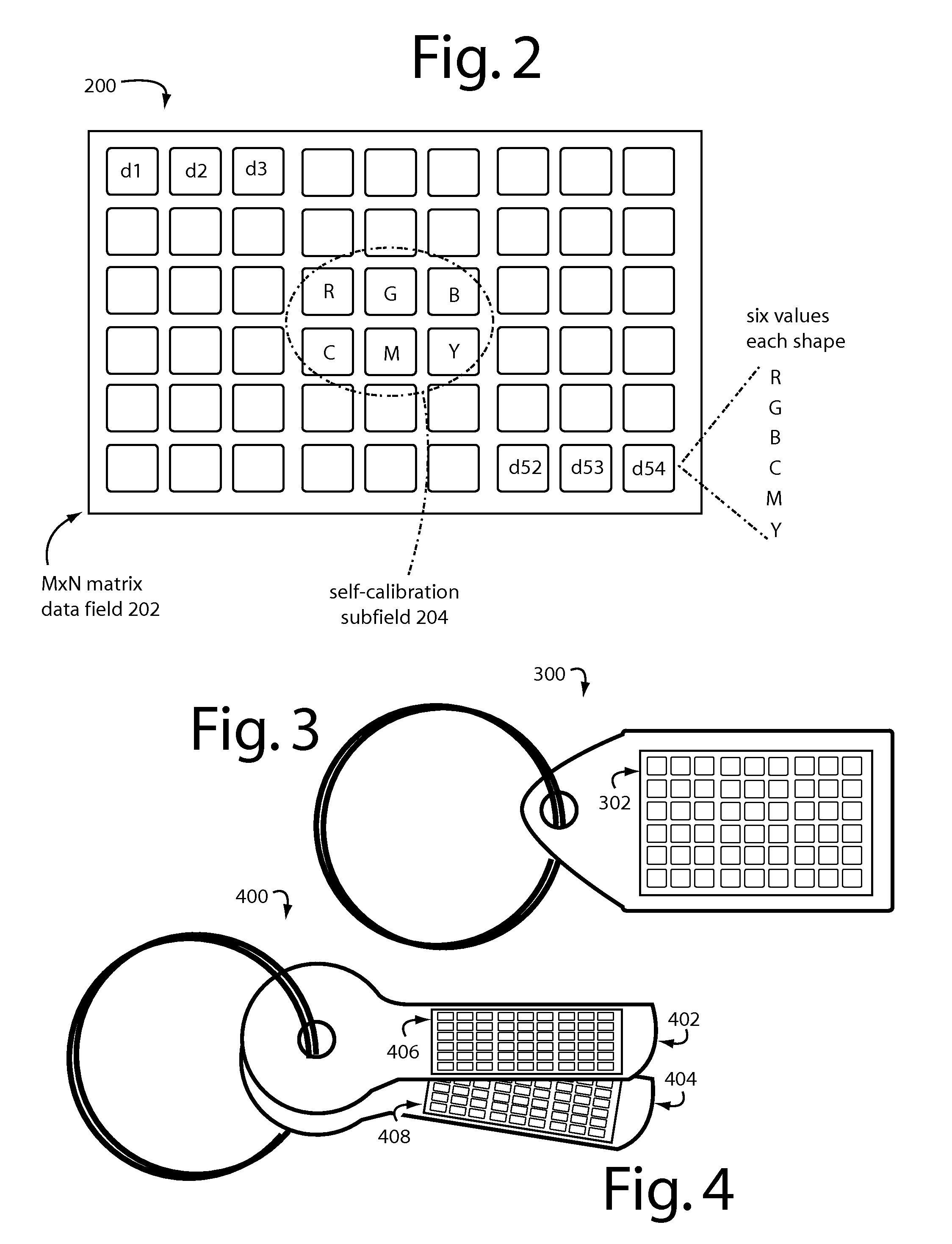
[0041]In general, a first group of embodiments of the present invention provide security gateways for applications and social networking accessed by consumer mobile devices. An email client database, private photos, private documents, and other personal and confidential files can be encrypted in files on a user's mobile device with cryptographic keys in the encoded visual form of colorgrams. Users' data and links to “apps” are displayed as icons in an encrypted vault, and selecting one of them will launch an auto-capture sequence, extract the corresponding key from a captured colorgram, use this to recover a passcode-session key from the encrypted data in the vault, and then launch the appropriate website or file viewer.
[0042]Alternatively, the “app” link may use a key read from the captured colorgram to generate a One-Time Passcode (OTP) that will enable the user to log on to a bank account for a higher level of security. The embodiments then auto-fill the respective login data for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com