Keyless entry system security enhancement
a keyless entry and security enhancement technology, applied in the field of keyless entry system security enhancement, can solve problems such as security vulnerabilities, and achieve the effect of enhancing the security of the keyless entry system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
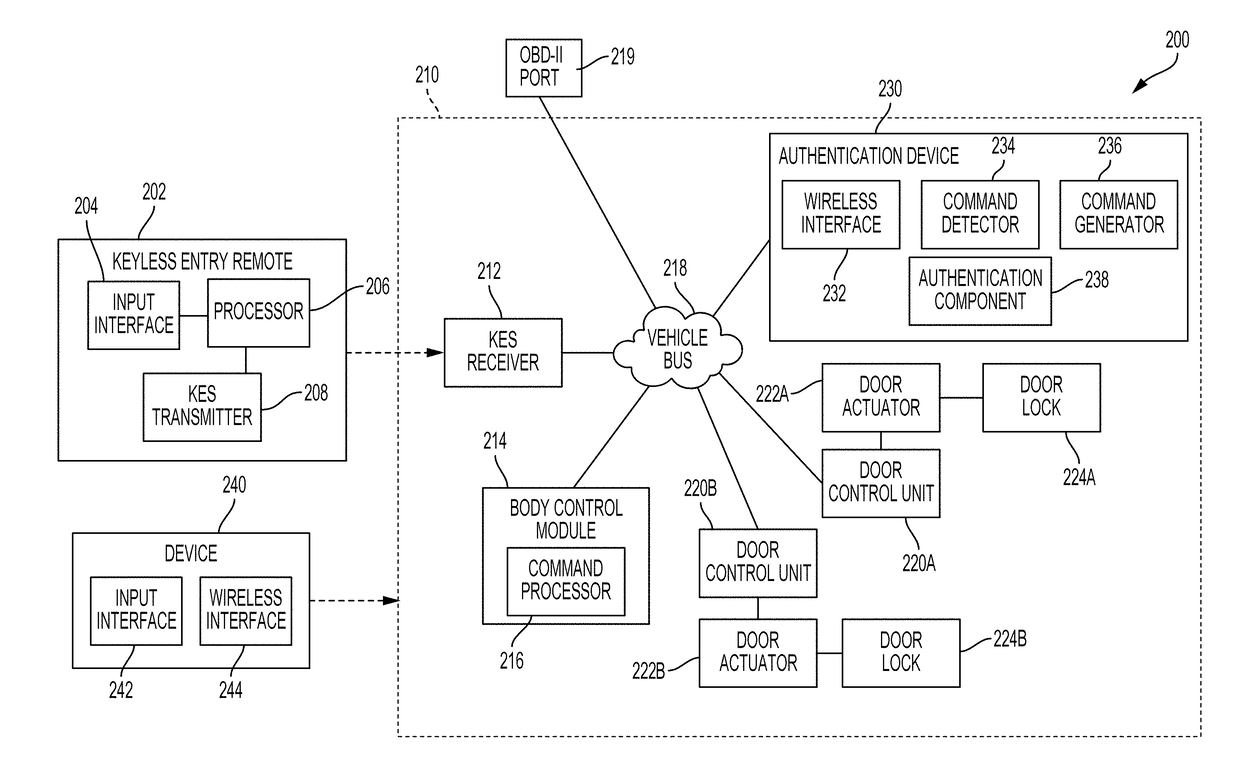
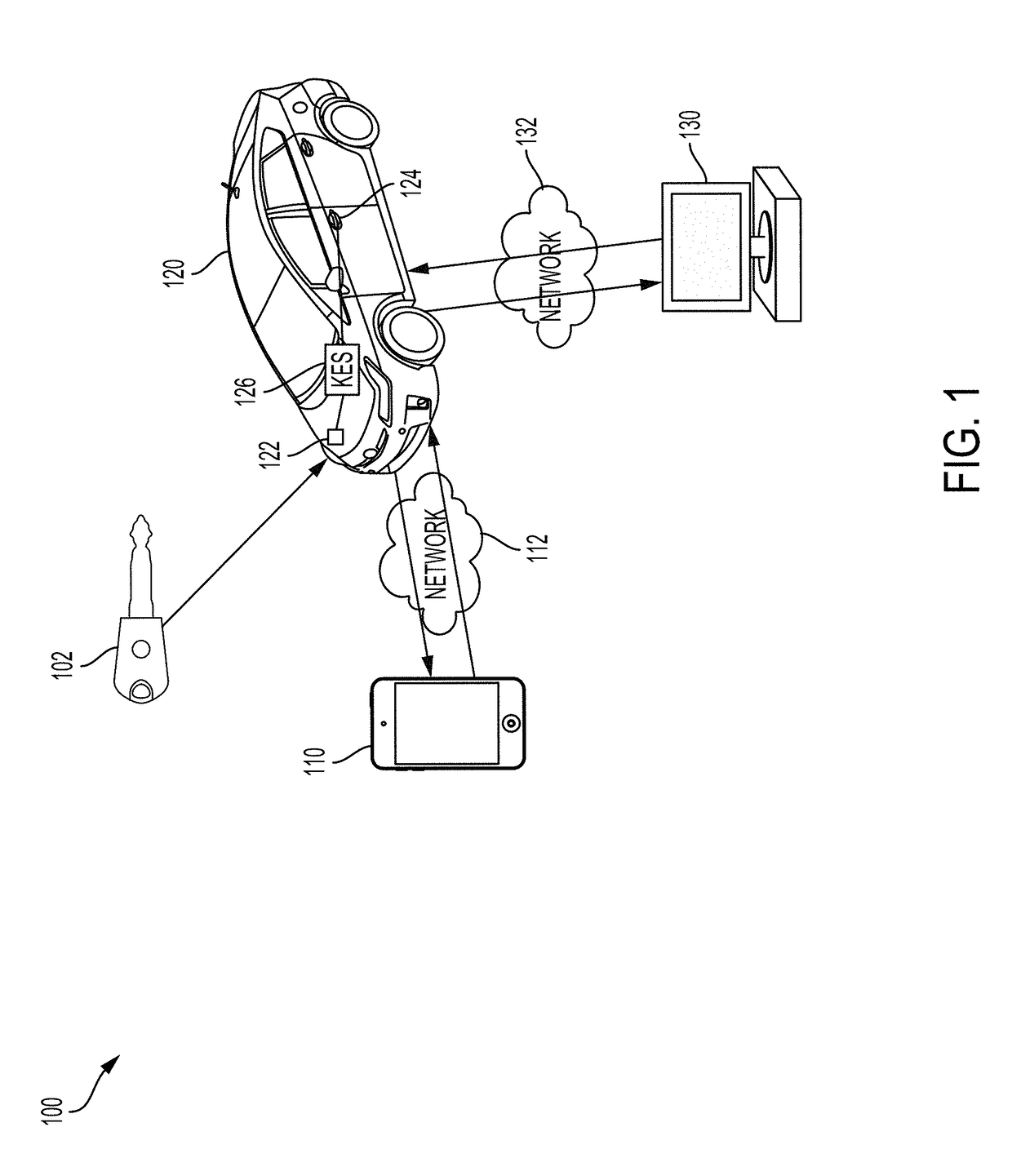
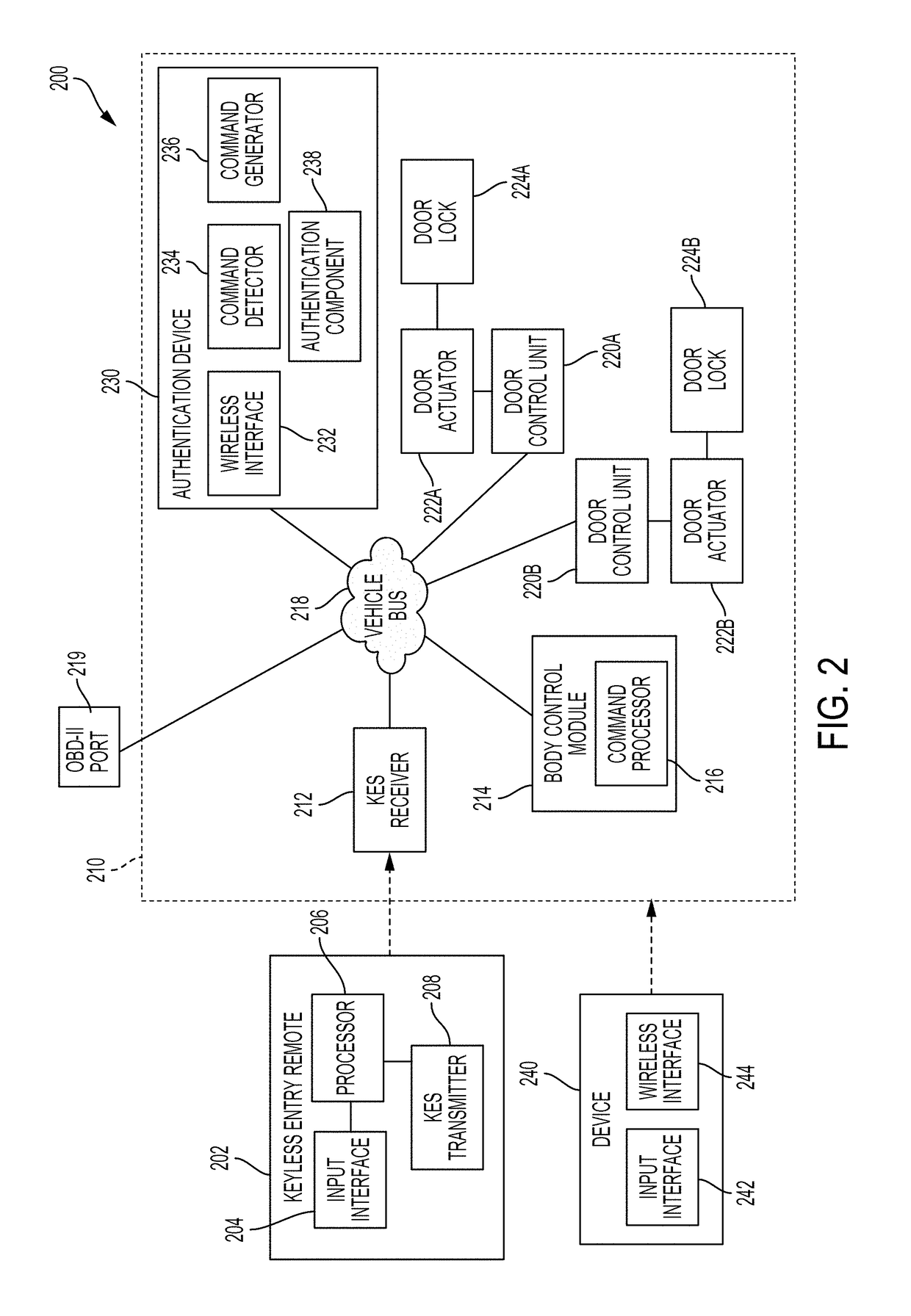
[0040]Modern vehicles, particularly automobiles, can utilize wireless signals from a keyless entry remote to unlock a vehicle through a keyless entry system (KES). In particular, the KES may unlock the vehicle once the KES verifies that a wireless signal from the keyless entry remote corresponds to an authorized unlock code. However, such a KES can be vulnerable to attack and exploitation from malicious, unauthorized third parties who seek to gain unauthorized entry into the vehicle. For example, an unauthorized user may gain unauthorized access to modern vehicles by exploiting a vulnerability of the KES through an attack called “RollJam” or through an “amplification attack.”
[0041]A RollJam attack refers to a type of attack in which the unauthorized user operates a device to intercept communications between the keyless entry remote and a target vehicle. As the user (i.e., authorized user of the vehicle) attempts to unlock the vehicle, the unauthorized user can capture a first wirele...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com