Preventing data from being submitted to a remote system in response to a malicious e-mail
a technology for preventing data from being submitted to a remote system in response to a malicious e-mail, applied in the field of computer security, can solve the problems of increasing the frequency of phishing campaigns at a dramatic and alarming rate, and the success of countermeasures to protect users from phishing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
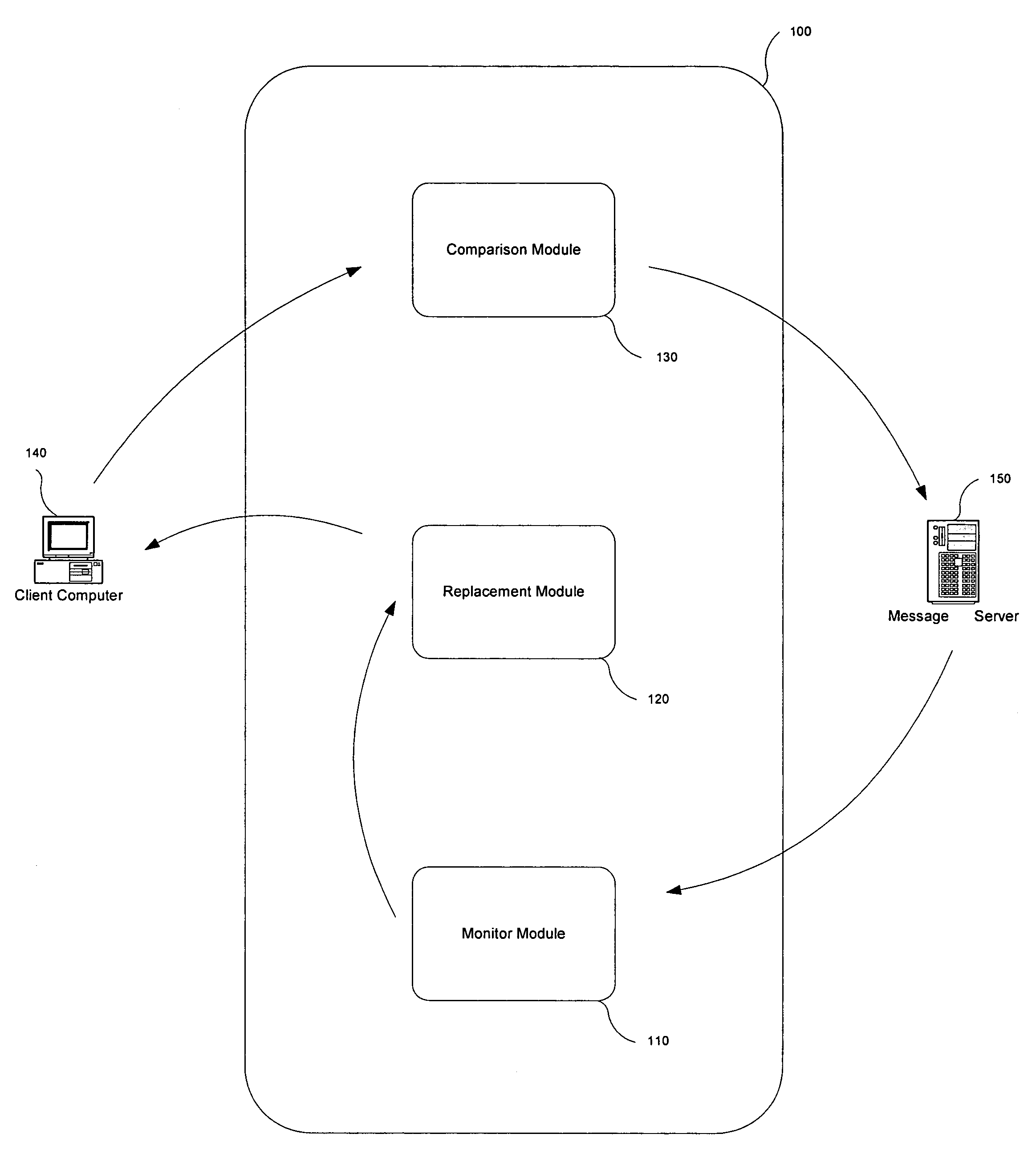
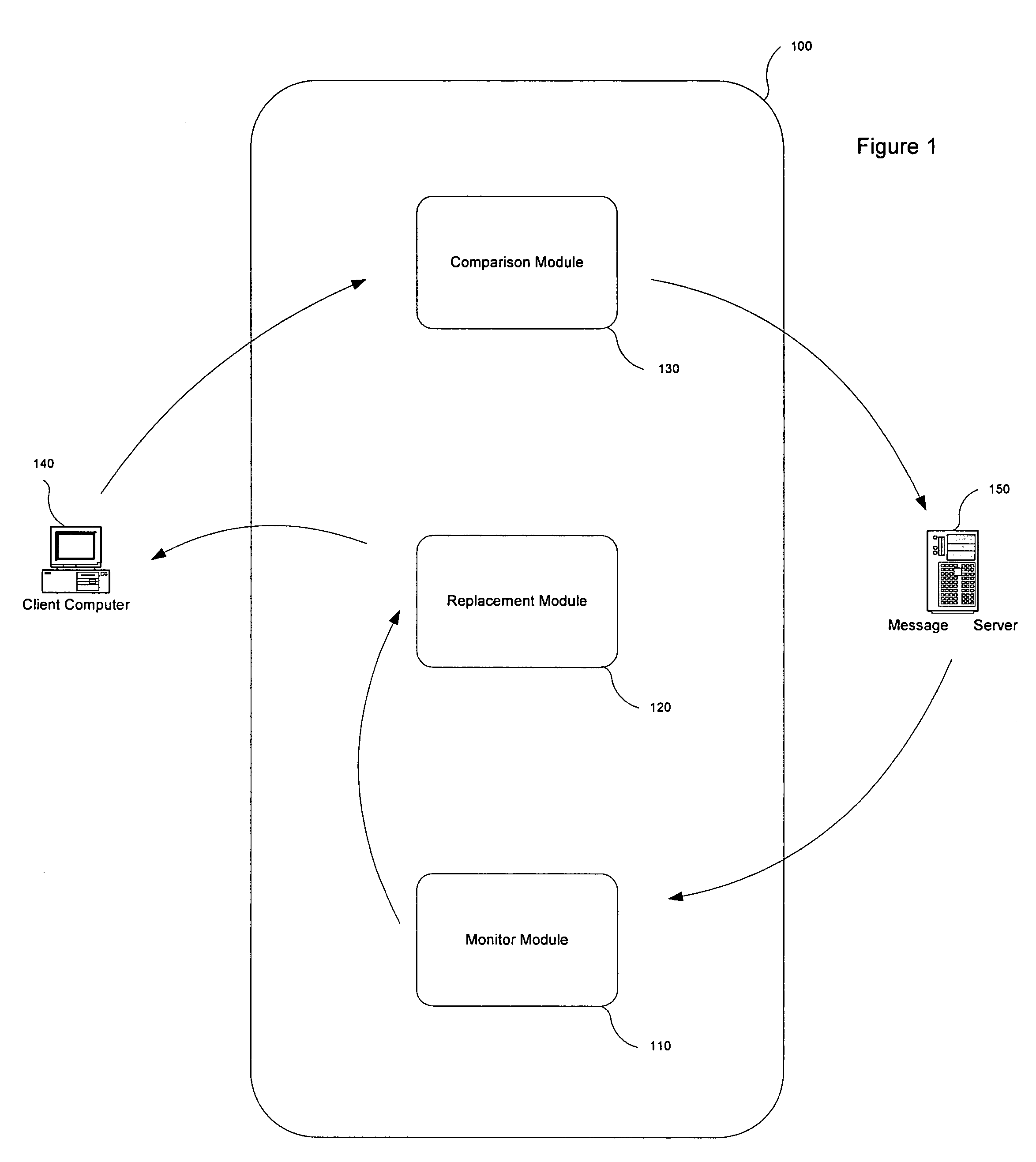
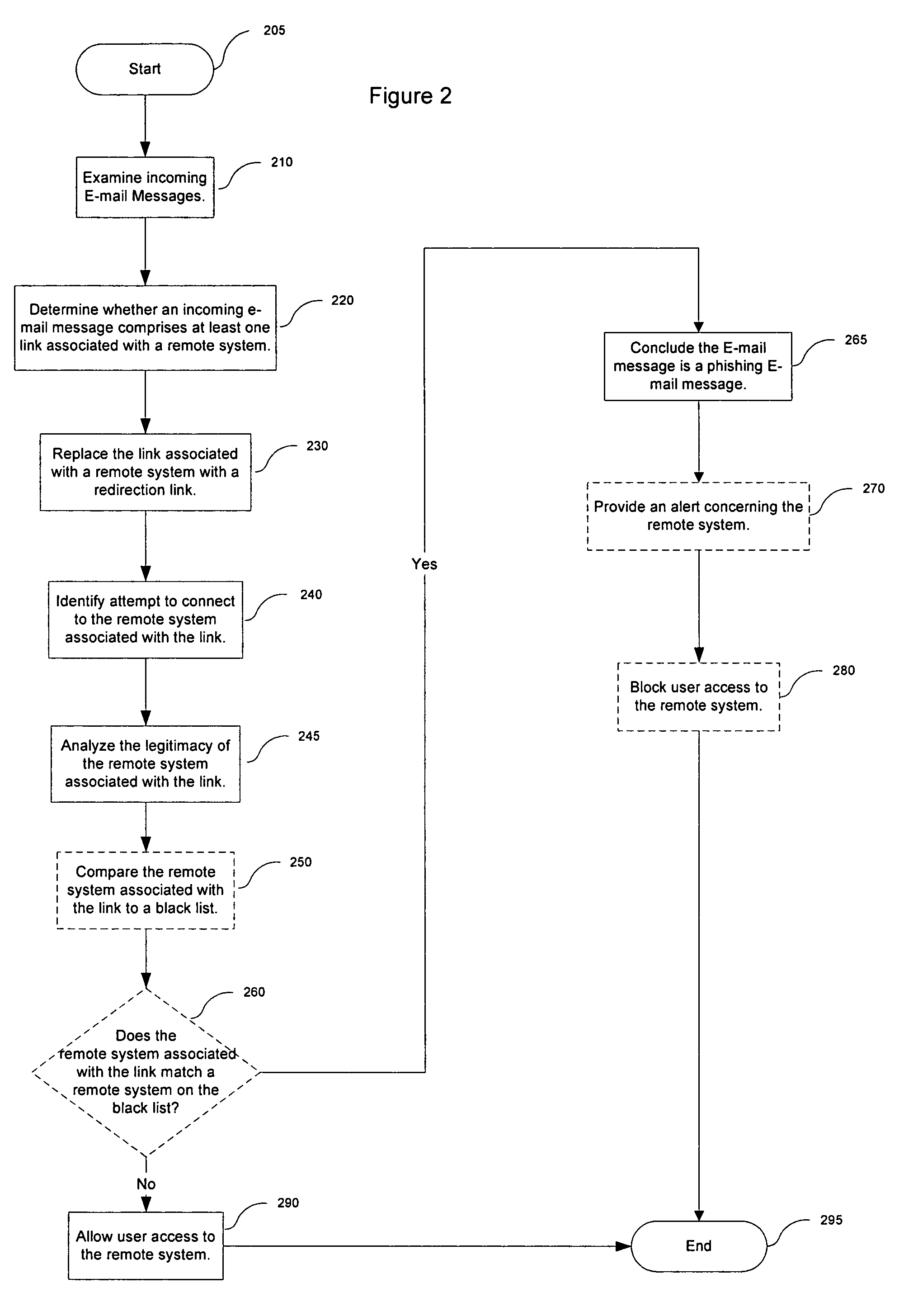
[0014]An electronic message manager 100 examines incoming electronic messages such as e-mails, instant messages, text messages following the SMS protocol, etc. to determine if they comprise at least one embedded link associated with a remote system. Each link identified by the electronic message manager 100 is replaced with a redirection link prior to the electronic message arriving to the user. When the user selects the link in an attempt to connect with the remote system, the redirection link directs the user, at least temporarily, to an analysis site where the legitimacy of the remote system associated with the original link is determined. When the legitimacy of the remote system associated with the link is found wanting, the electronic message manager 100 concludes the e-mail message is a malicious e-mail message and takes appropriate steps to prevent data from being submitted.
[0015]The electronic message manager 100 offers the following advantages over the prior art:
[0016]isola...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com