Device and method for authenticating user's access rights to resources
a technology for authenticating users and access rights, applied in the direction of program/content distribution protection, unauthorized memory use protection, instruments, etc., can solve the problems of replay attacks, unable to continue the execution of subsequent steps, and improper execution of application programs by replaying communication content, etc., to achieve easy and simple authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
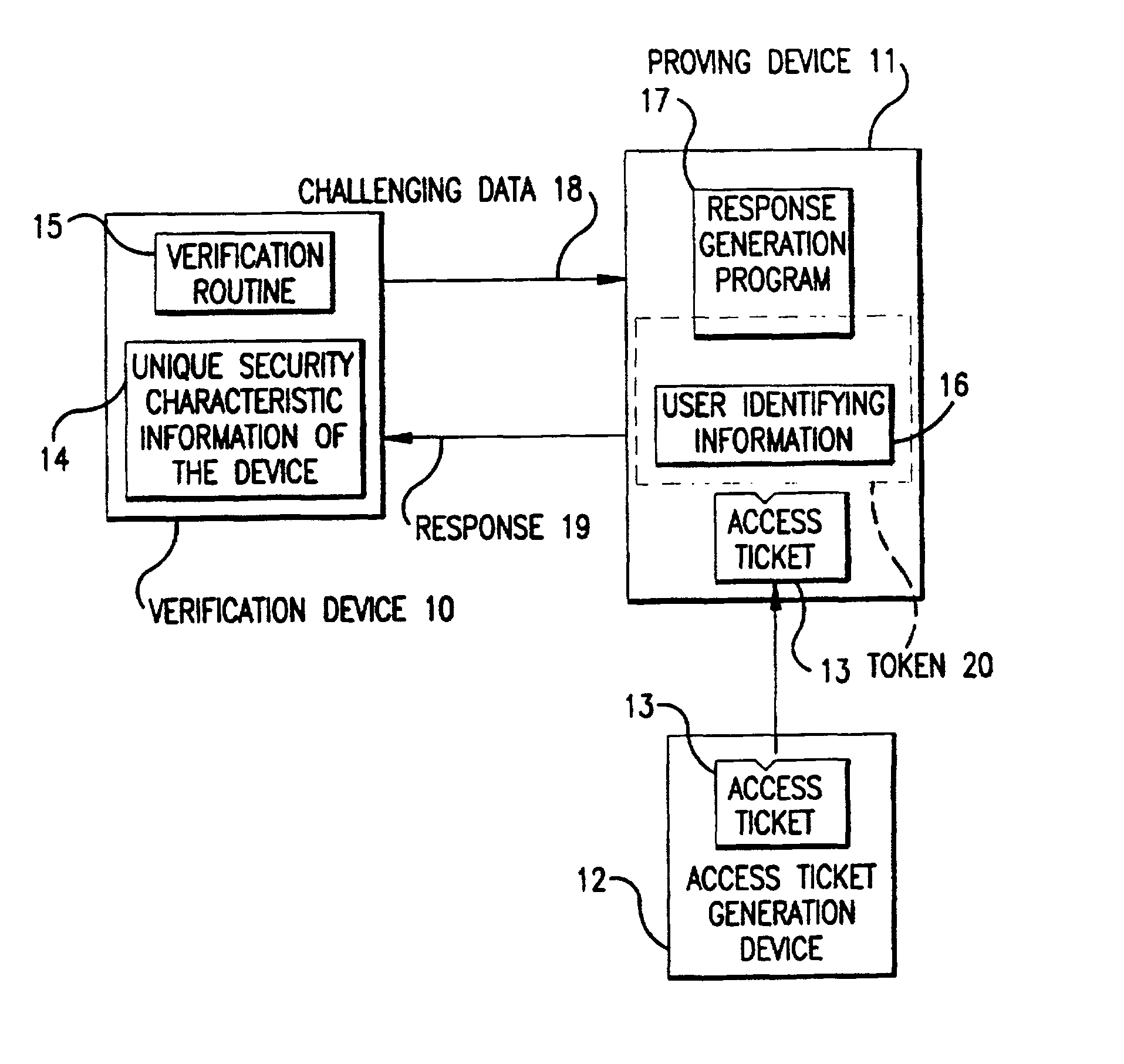
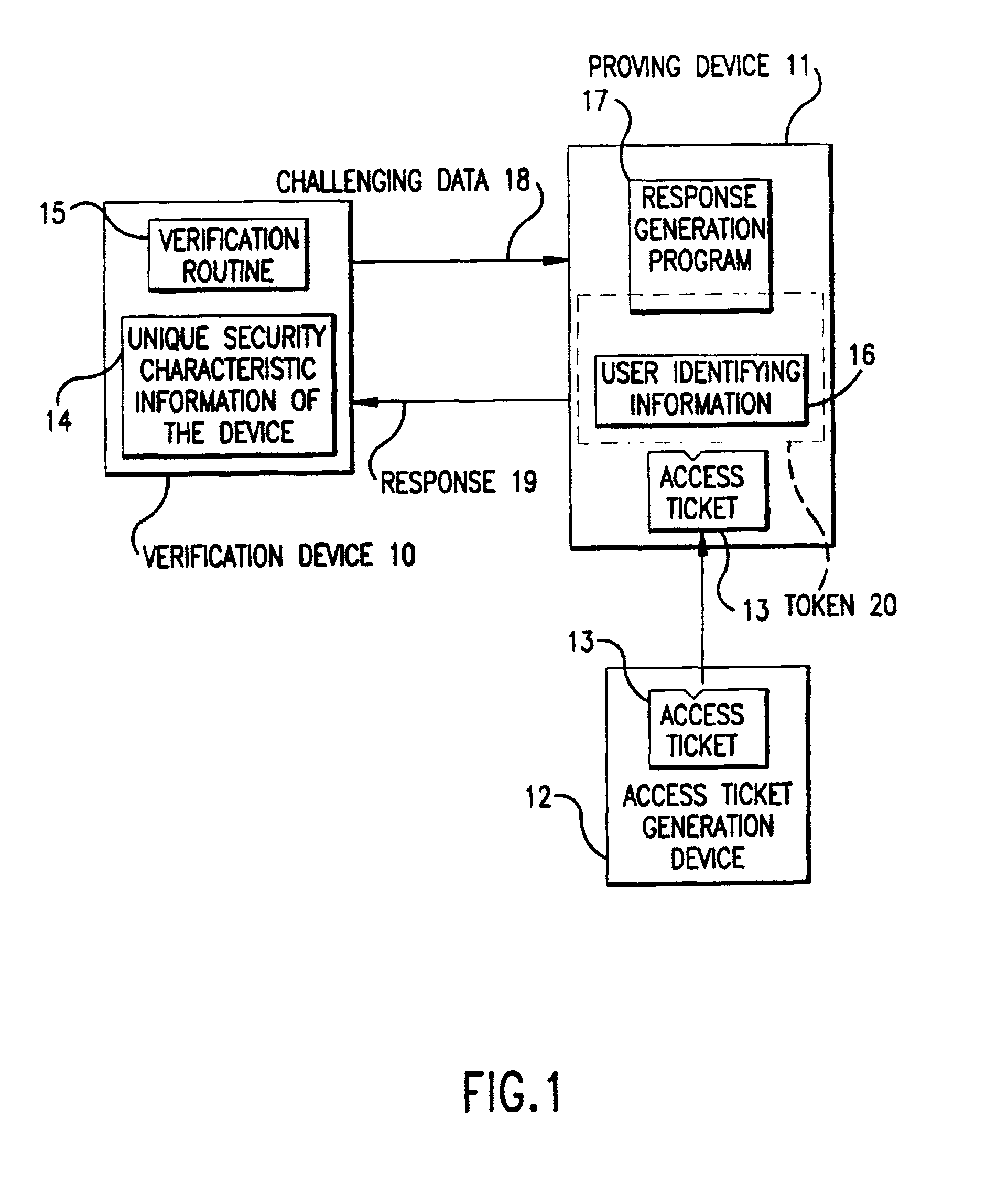
[0077]In a first embodiment, an access ticket t is defined as the relation (1).
t=D−e+ωφ(n) (1)
[0078]In the following bulleted paragraphs, symbols used in the above relation are described.[0079]An integer n is an RSA modulus, hence, a product of two very large prime numbers p and q (n=pq).[0080]φ(n) denotes the Euler number of n, hence, a product of two integers p−1 and q−1 (φ(n)=(p−1)(q−1)).[0081]A piece of user identifying information e is an integer allocated to each user. A piece of user identifying information is unique to a user: a different user identifying information is allocated to a different user.[0082]An access-ticket secret key D is a private key of an RSA public key pair. Since the modulus is assumed to be n, the relation 2 is derived from the definition.
gcd (D, φ(n))=1 (2)[0083]In the above, gcd (x, y) denotes the greatest common divisor of two integers x and y. The existence of an integer E satisfying the relation (3), which is called an access-ticket public key, ...
second embodiment
[0097]A second embodiment to be described is the same as the first embodiment regarding the definition of an access ticket t and the function of the proving device. However, the verification device works differently. The difference in the roles between challenging data C and a response R causes the difference in the function between the two embodiments: in the first embodiment, a response R is encryption of a random challenging data C; in the second embodiment, a response R will be decryption of challenging data C which is encryption of some other meaningful data.
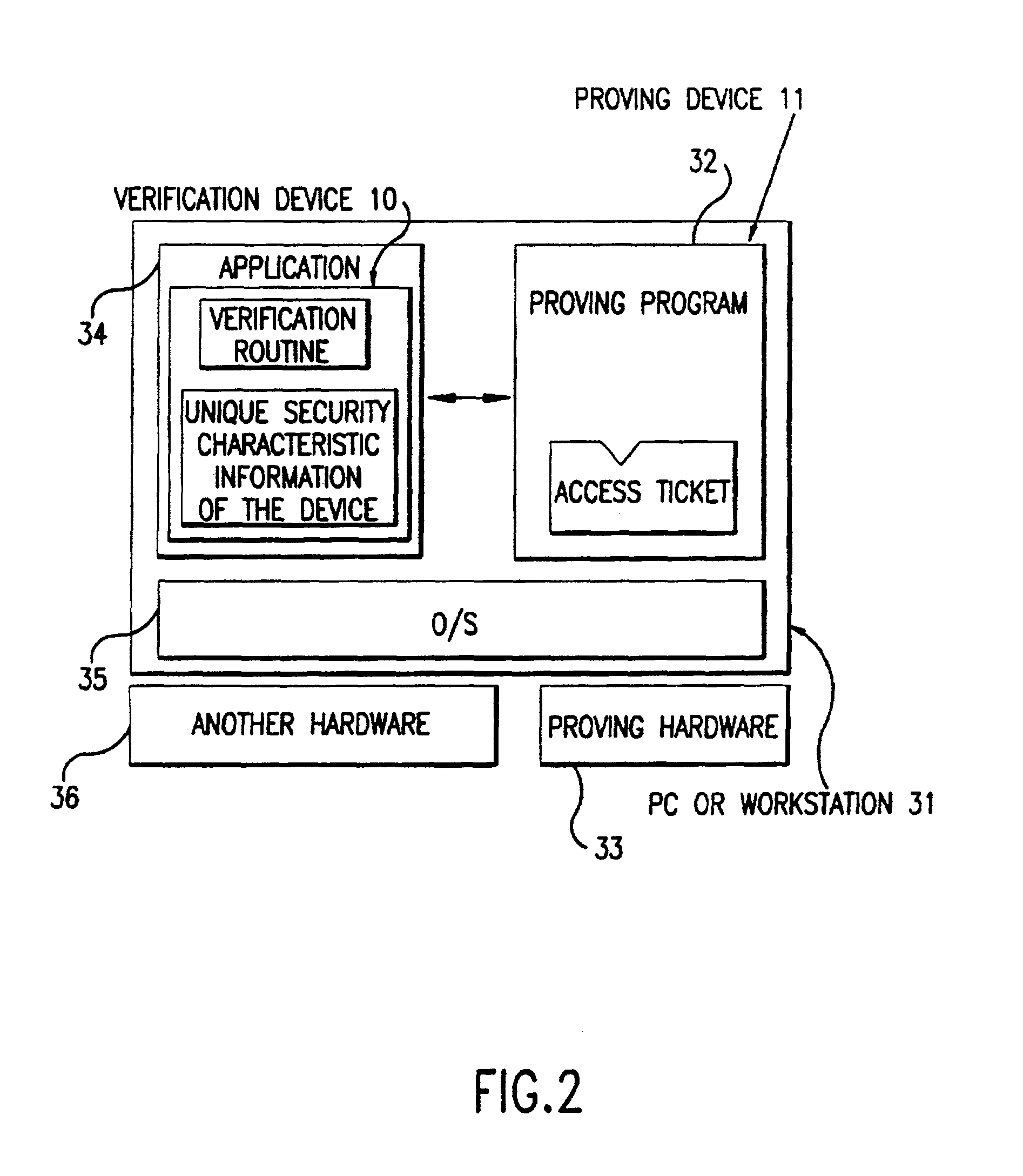
[0098]FIG. 5 depicts the constitution of devices of the second embodiment, and FIG. 6 depicts flow of data. A verification device 10 comprises the following means: an access ticket public key storing means 101; a random number generation means 102; a random number storing means 103; a response storing means 105; a randomizing means 121; a challenge seed storing means 122; a de-randomizing means 123; and an execution means 3...
third embodiment
[0117]In a third embodiment, the definition of an access ticket is given as the relation (16).
t=D+F(n, e) (16)
The following bulleted paragraphs illustrate the symbols appearing in the relation (16).[0118]An integer n is an RSA modulus, hence, a product of two very large prime numbers p and q (n=pq).[0119]φ(n) denotes the Euler number of n, hence, a product of two integers p−1 and q−1 (φ(n)=(p−1)(q−1)).[0120]A user identifying information e is an integer allocated to each user. The user identifying information e is unique to each user: a different user identifying information is allocated to a different user.[0121]An access-ticket secret key D is the private key of an RSA public key pair. Since the assumed modulus is n, D satisfies the relation (17).
gcd(D, φ(n))=1 (17)[0122]In the above, gcd(x, y) denotes the greatest common divisor of two integers x arid y. The existence of an integer E satisfying the relation (18), which is called an access-ticket public key, is derived form th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com