Method for safeguarding the continuous safety operation of computers
A safe operation, computer technology, applied in the direction of data error detection, response error generation, etc., in the redundancy of calculation and operation, can solve problems such as loss of notebook computer, system crash, lack of arbitration module, etc., to restore operational intelligence and quick, effective results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
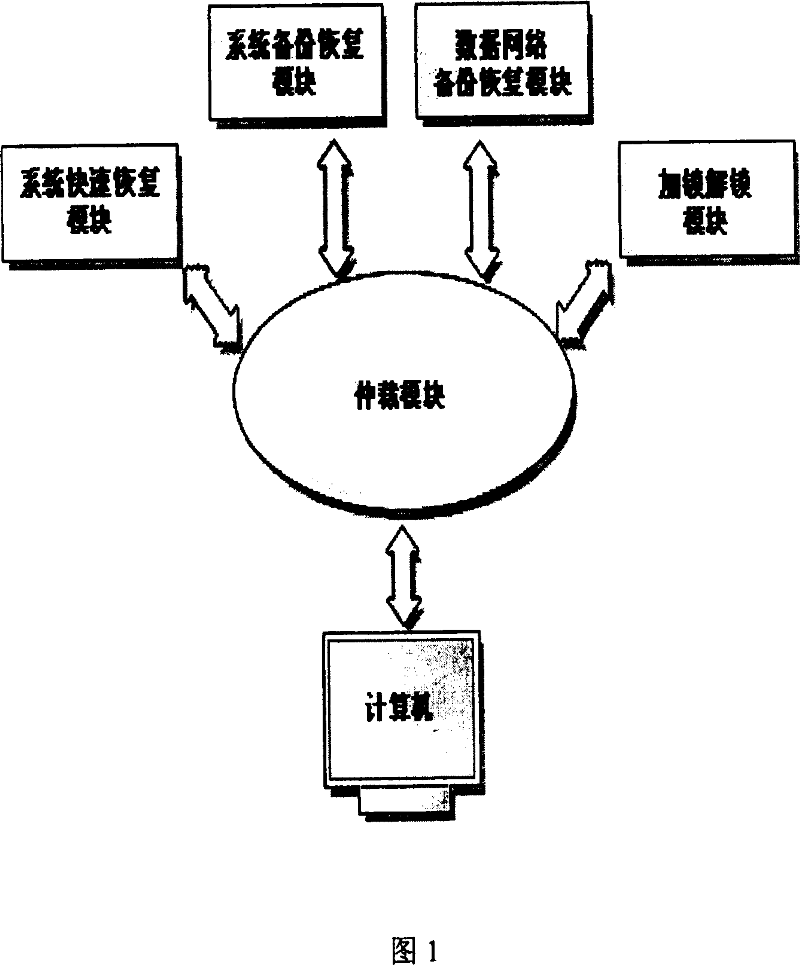
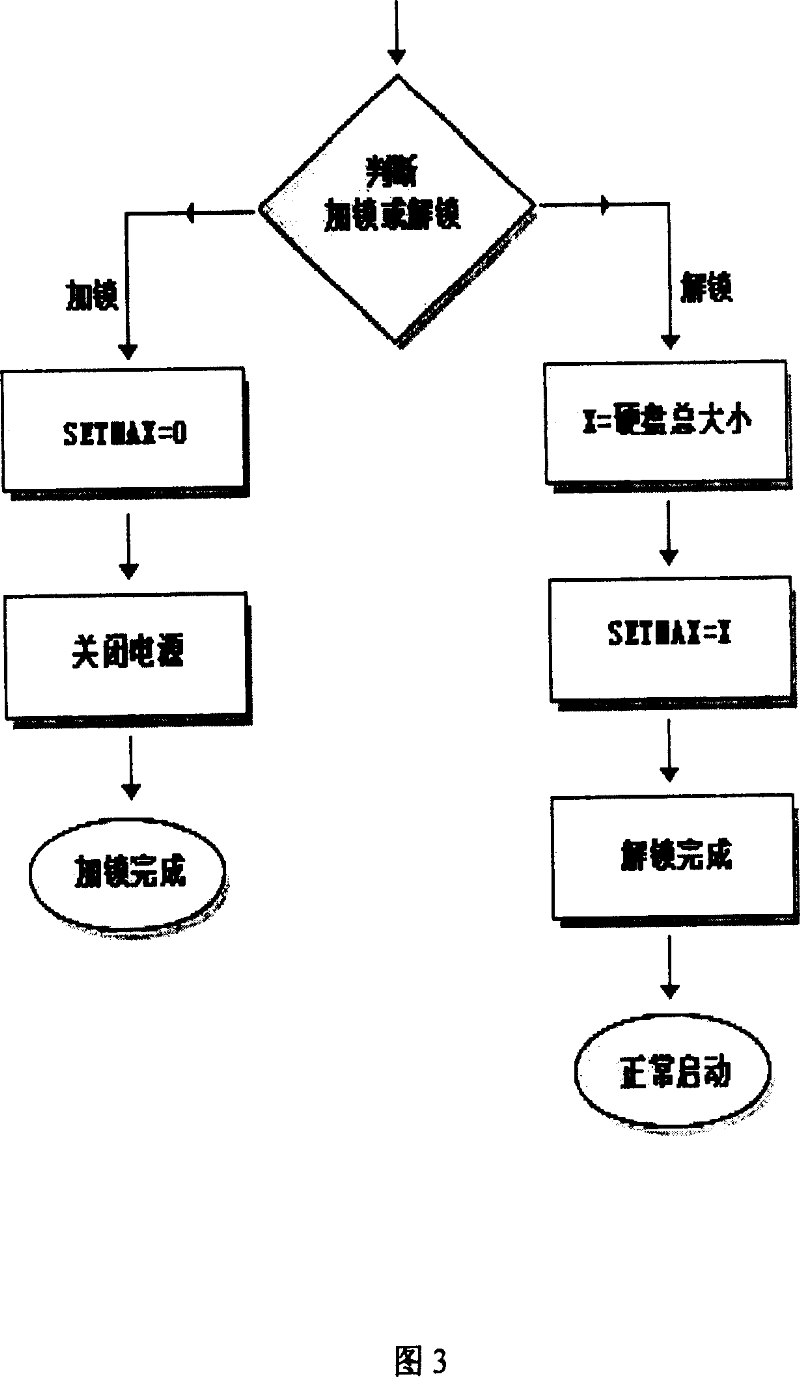
[0026] Equip the computer with a USB key, which has a unique serial number, the serial number is stored in the arbitration module of the computer, and the password of the legal user is stored. This way, only legitimate users can initiate computations. If there is no legal identity to start the computer, the locking and unlocking module will deadlock the hard disk, even if the hard disk of the computer is removed and connected to other computers, it cannot work. In this way, a certain degree of data security is guaranteed. Especially for laptops, the lock and unlock module can delay the time of critical data leakage.
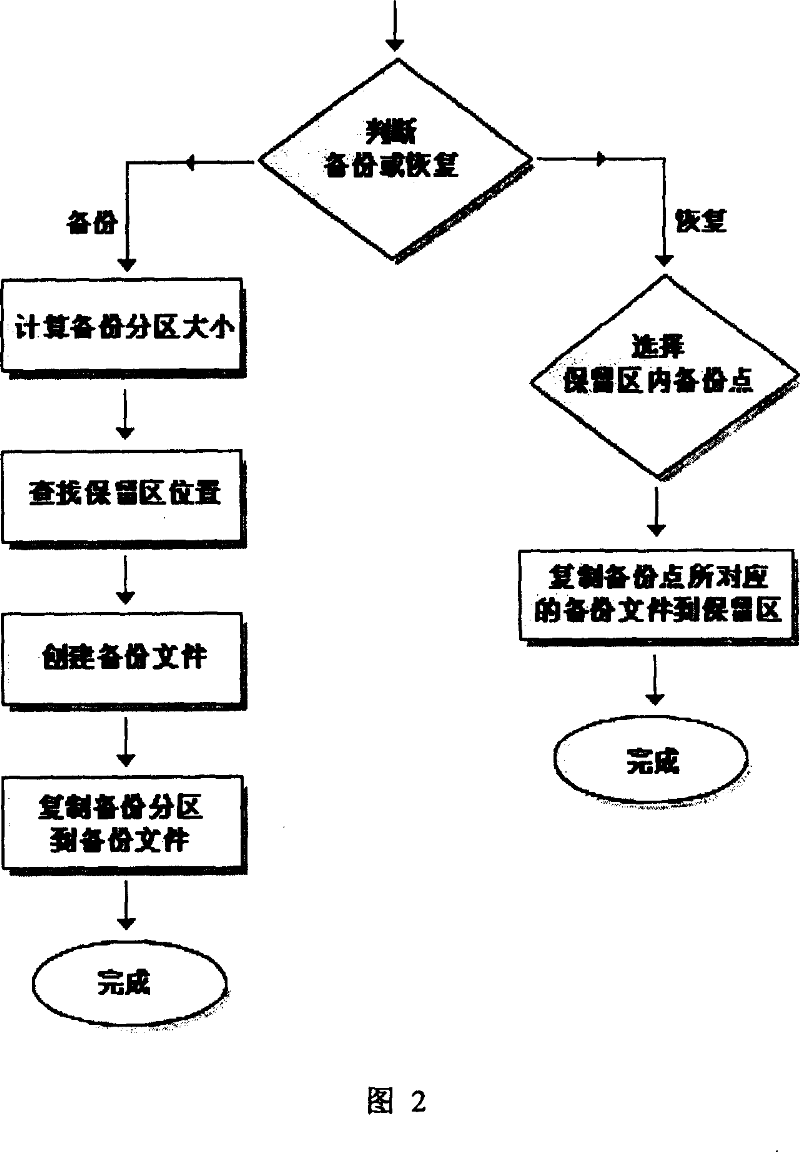
[0027] The system fast recovery module has a filter driver, when the operating system writes a file, it does not overwrite the old file but creates a new file, and marks it with a date and time. When reading a file, select the closest file from many files with the same name according to the date and time mark, and read the file. When the system needs to be res...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com