Method for applying general weight discrimination frame
An authentication and framework technology, applied in wireless communication, radio/inductive link selection arrangement, electrical components, etc., can solve the problems of spending storage resources and resource waste
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the technical solution of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
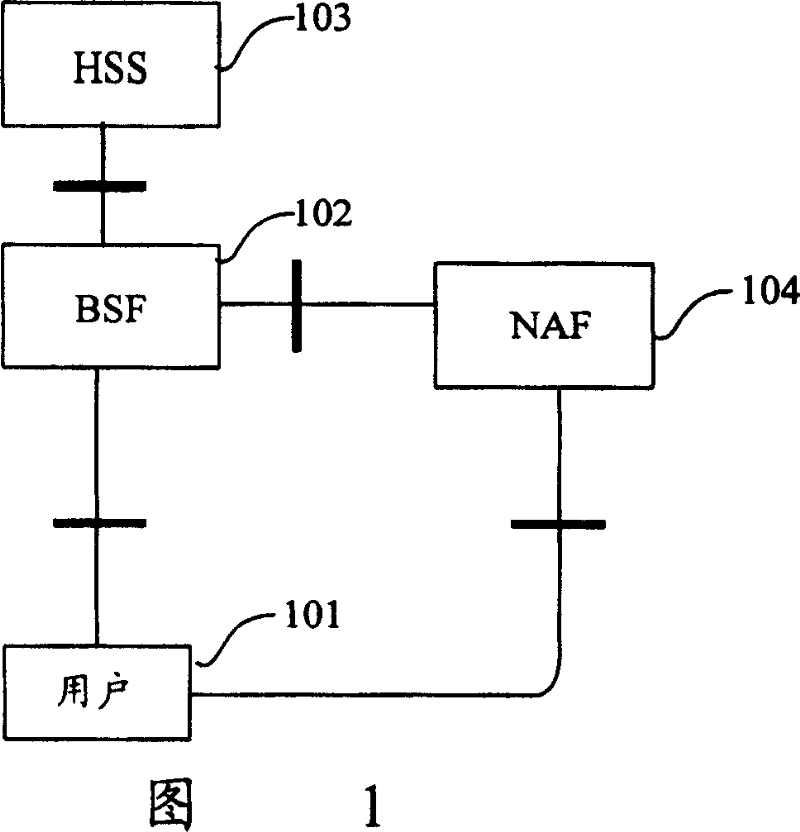
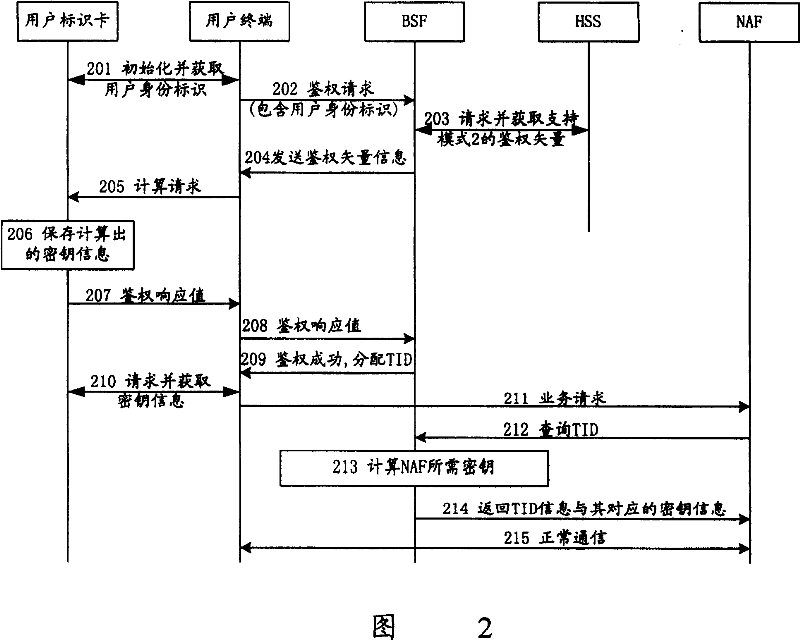
[0026] The idea of the present invention is: after the user identification card calculates the required response value and key information for authentication, it judges whether the user terminal supports mode 2 according to the mode information supported by the user terminal that it has saved, and if not, it Actively send the key Ks_ext and the authentication response value to the user terminal, and continue the follow-up processing according to the mode 1, otherwise, only send the authentication response value to the user terminal, and when the user terminal needs to communicate with the NAF, the user identification The card clearly requests Ks_ext_NAF or Ks_int_NAF, and the corresponding calculation is completed by the user identification card, and the user terminal no longer partici...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com