Mark anti-fake method for compressing video frequency flow
A video stream and logo technology, applied in the field of proving the reliability of video streams, can solve the problems of heavy workload, increased hardware cost, invisible watermark, etc., and achieve the effect of small processing workload and prevention of intentional attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
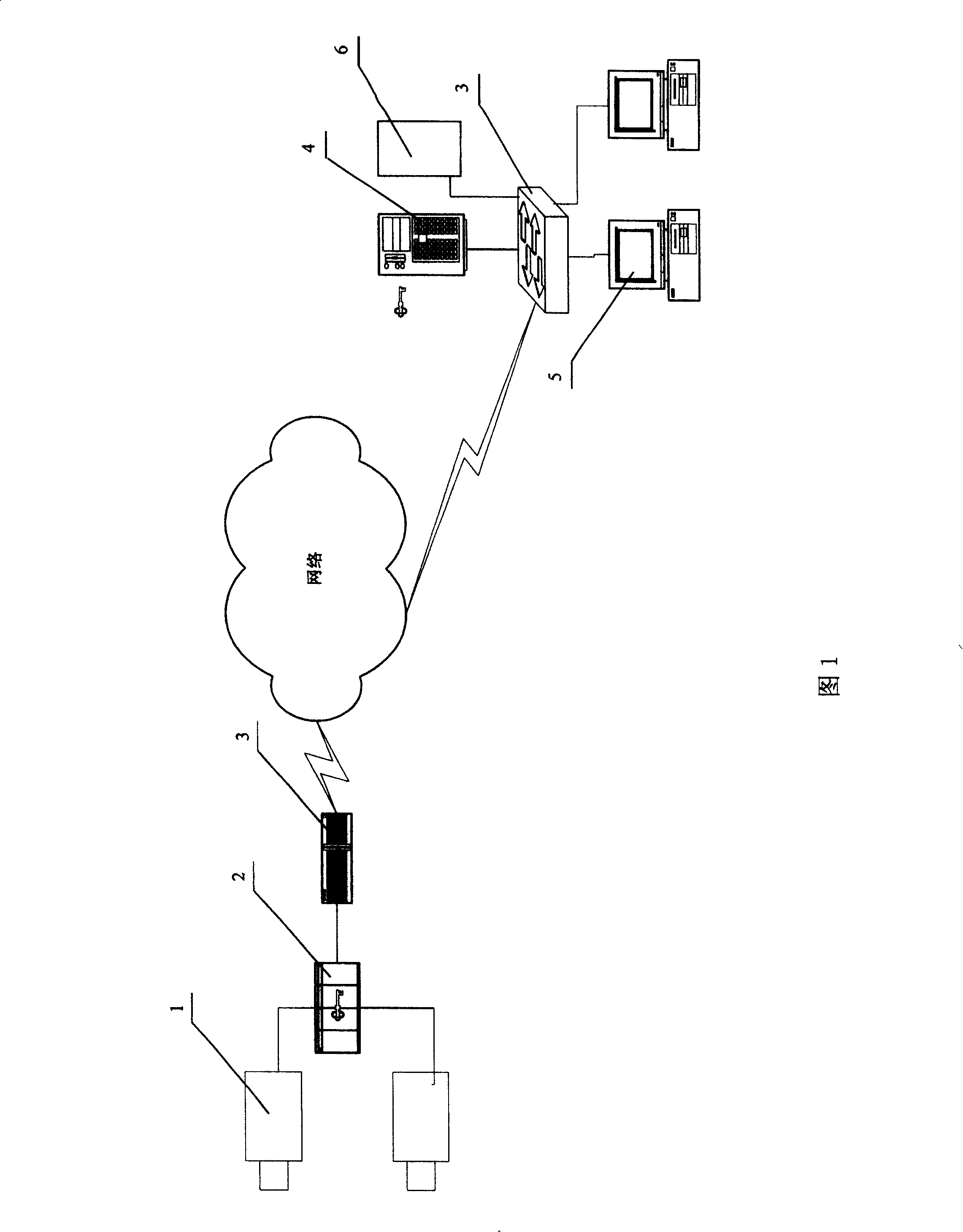
[0041] Embodiment one: referring to shown in accompanying drawing 1, a kind of logo anti-counterfeiting method for compressing video stream utilizes network to realize the real-time embedding and detection (real-time detection and video detection) of anti-counterfeiting logo, and the device it adopts is as shown in accompanying drawing 1 display, including:
[0042]1. Camera 1, used to acquire video images;
[0043] 2. Logo embedding / video compression device 2, wherein, logo embedding can be realized by a program on a dedicated chip, a dedicated computer or a general-purpose computer, which generates a structural key according to the device serial number and the current time, and generates a divergent key from the structural key. chaotic sequence of numbers. According to the serial number of the device and the current time, select a preset image (original logo) in the logo library stored in the machine, and then adjust the RGB color value of each point of the image according ...
Embodiment 2
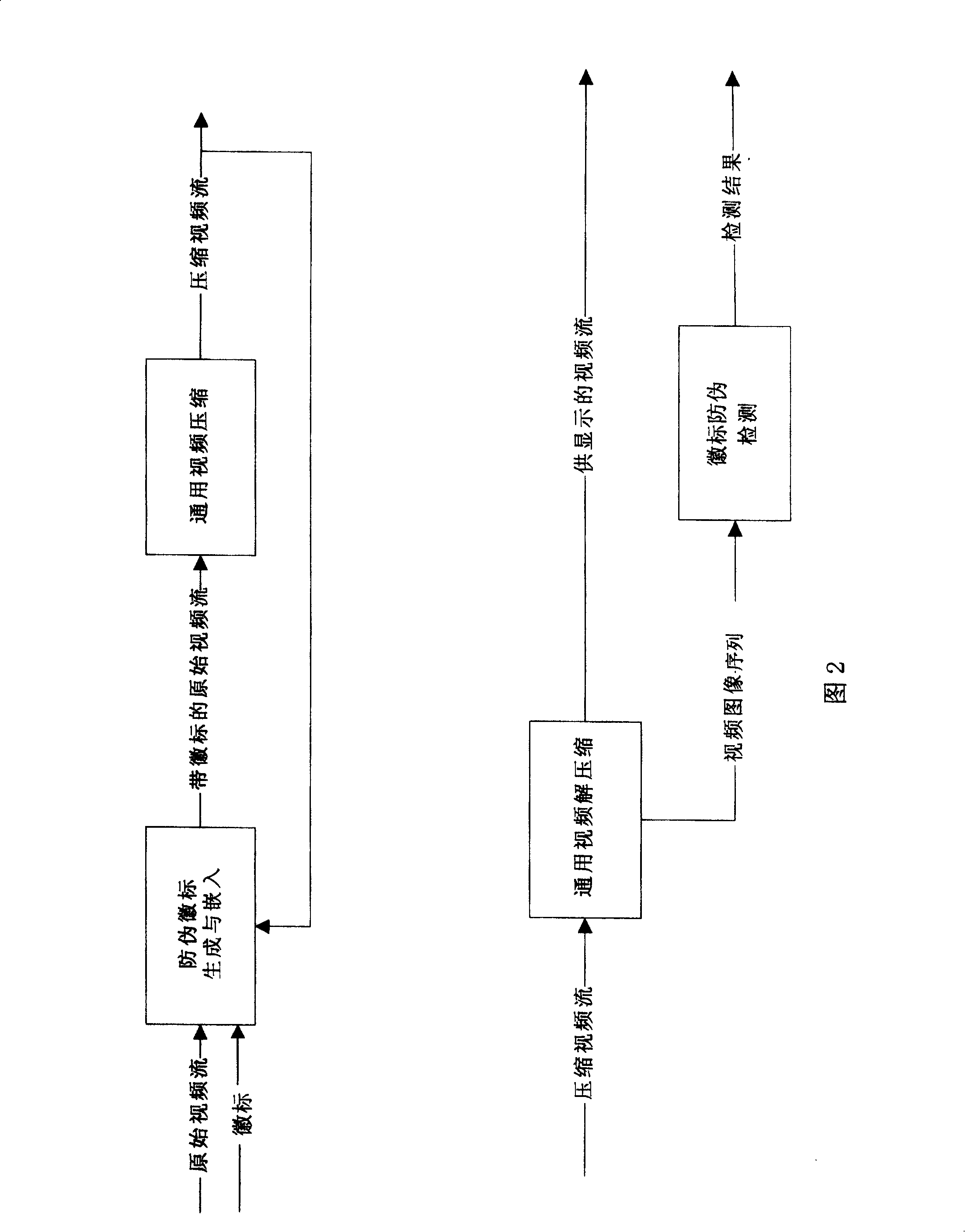
[0049] Embodiment two: referring to shown in accompanying drawing 2, a kind of method that is used to prevent DVD from being tampered with, anti-counterfeiting logo is dynamically embedded in DVD video, and detects, and its realization device comprises:
[0050] The logo embedding device can be implemented by a program on a dedicated chip, a dedicated computer or a general-purpose computer, which generates a structural key for the current relative time signature according to the private key of the video provider, and a pseudo-random digital sequence is generated by the structural key . The publisher's trademark is used as the original logo, and then the color value of each point of the image is adjusted according to the pseudo-random number sequence to generate the first logo with structure; each number of the pseudo-random number sequence is negated to obtain the second Logo with structure. At the same time, the structural key, the current relative time and the relevant dete...
Embodiment 3
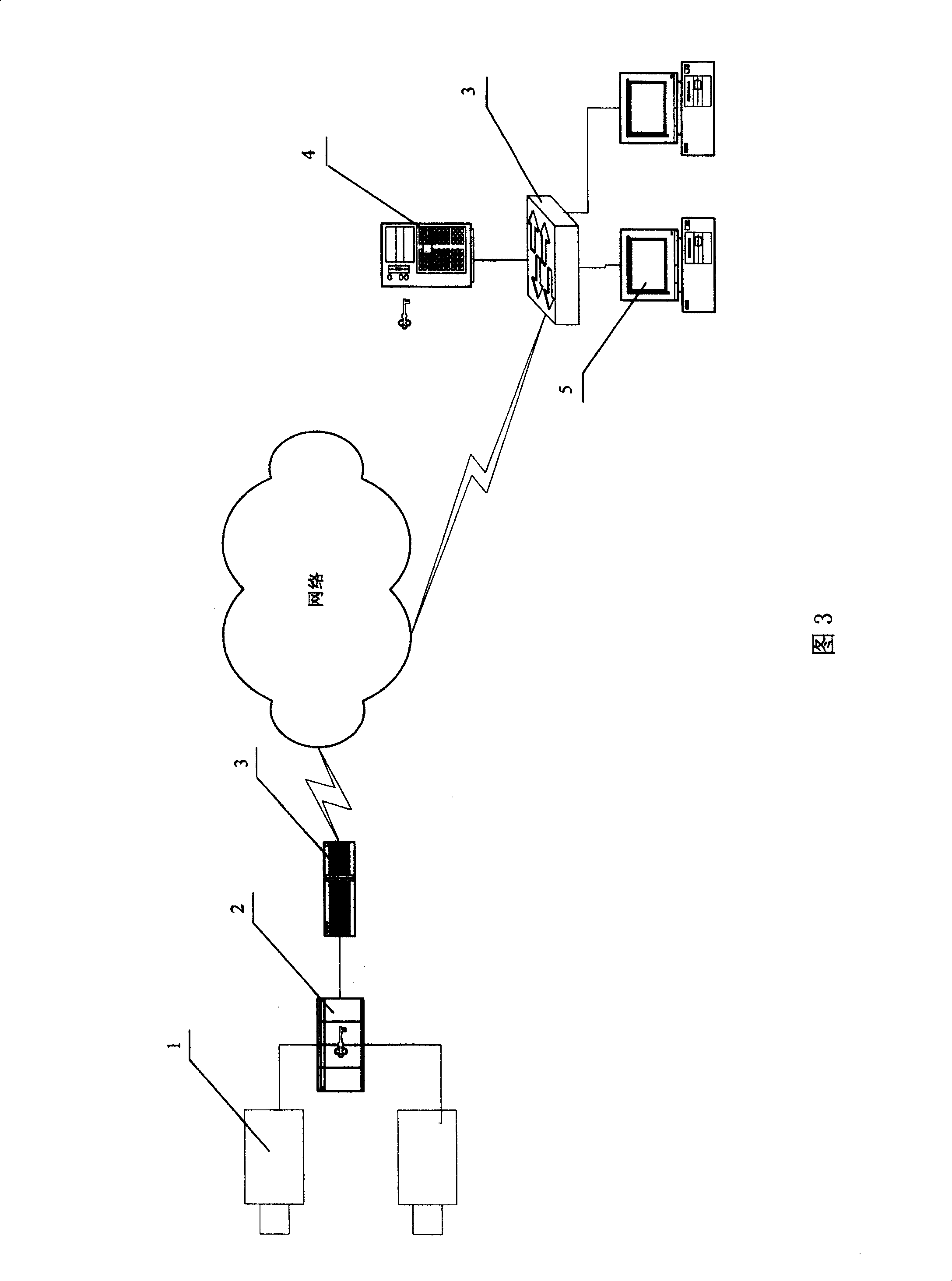
[0052] Embodiment three: see accompanying drawing 3, a simplified logo anti-counterfeiting method for real-time monitoring of the network, using the network to realize real-time embedding and detection of anti-counterfeiting logos, the device it uses is shown in accompanying drawing 3, including:
[0053] 1. Camera 1, used to acquire video images;
[0054] 2. Logo embedding / video compression device 2, wherein the logo embedding can be realized by a program on a dedicated chip, a dedicated computer or a general-purpose computer, which superimposes the logo with structure received from the logo generation and detection device through cryptographic communication onto the original In the video stream, such a video stream is compressed by a dedicated video compression chip or a general-purpose video compression program, and the logo embedding device decompresses the compressed video stream and detects the correlation value, and obtains a correlation value after compression and decom...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com