A method of safety authentication between media gateway and media gateway controller
A media gateway and security authentication technology, applied in the field of authentication management, can solve problems such as network system paralysis, equipment flooding, and impossibility of implementation, and achieve the effect of preventing repeated attacks, preventing counterfeiting events, and a wide range of applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
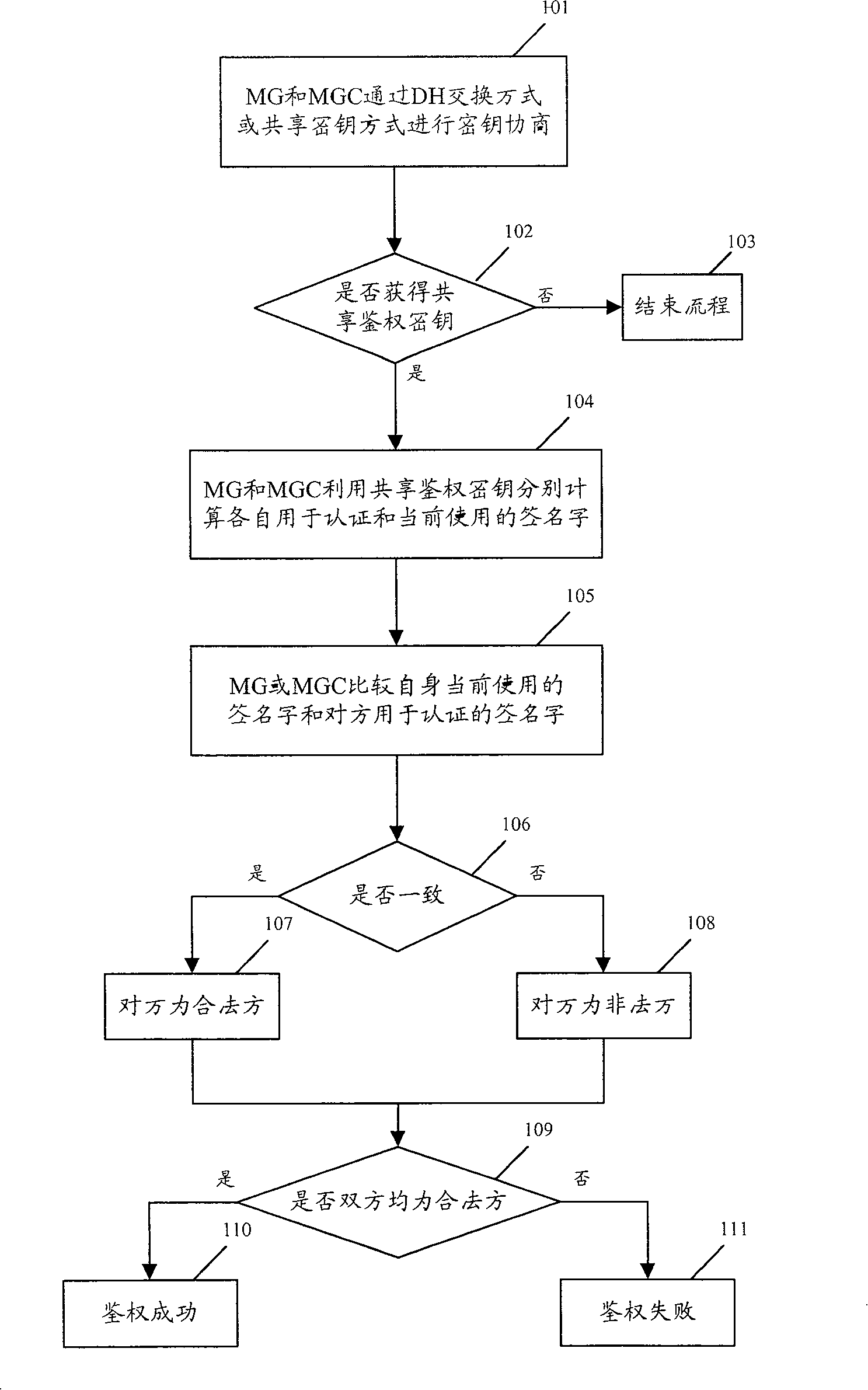
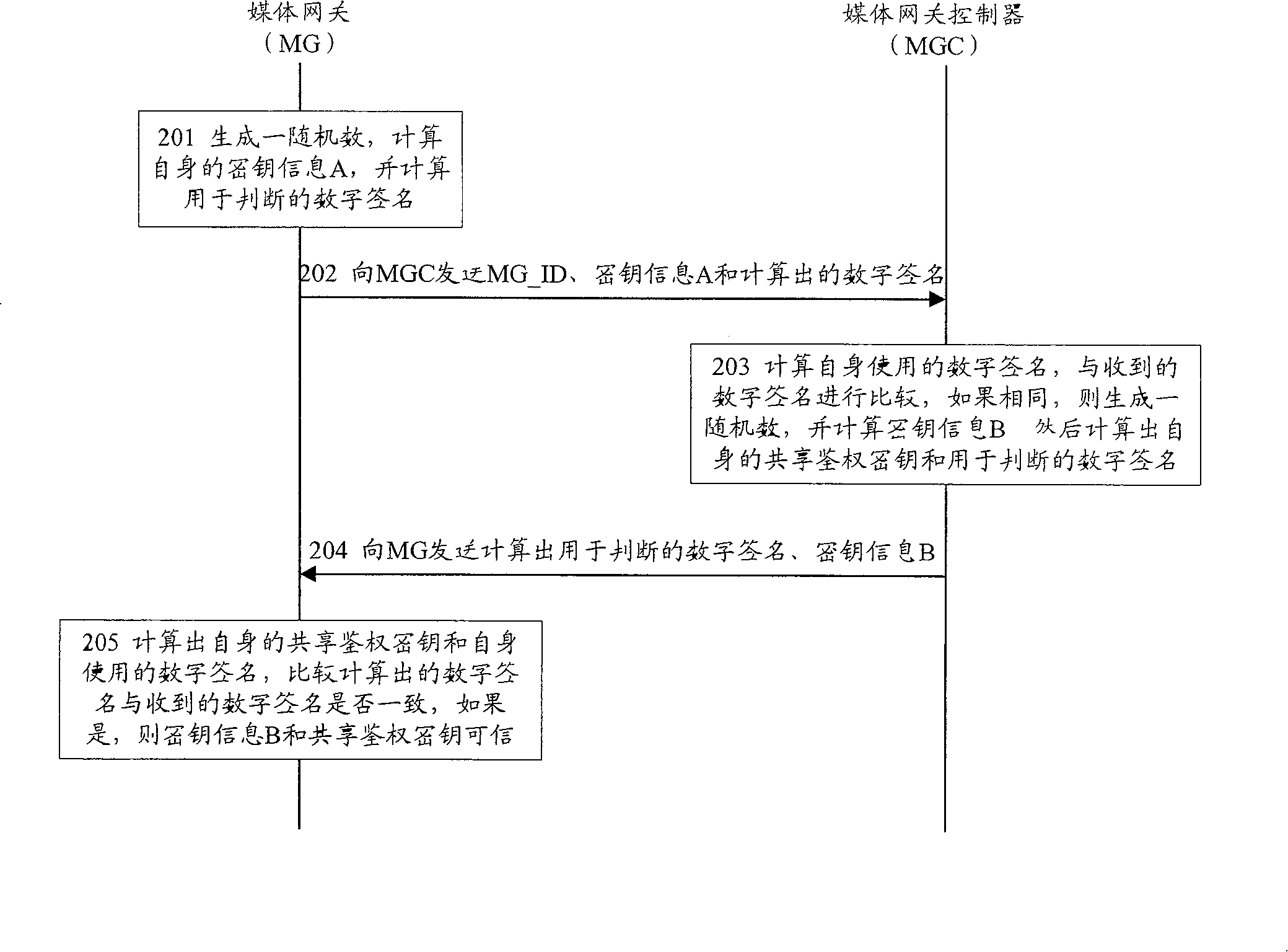
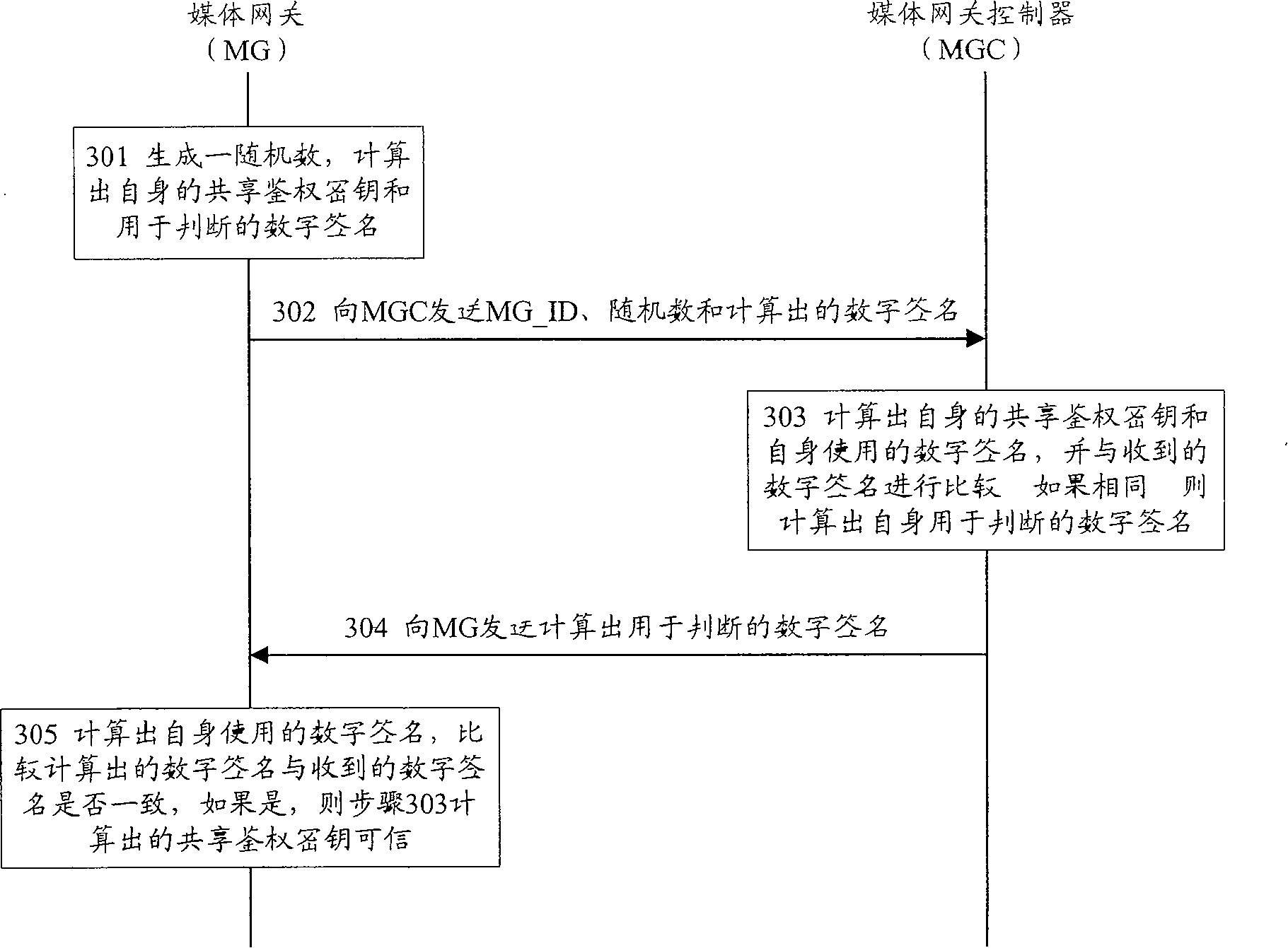
[0039]The basic idea of the present invention is to separate the shared authentication key negotiation and determination process from the authentication process in the entire security authentication process between the MG and the MGC, and perform each relatively independently. More specifically: after determining the shared authentication key of both parties, further use the determined shared authentication key and the random number randomly generated by the MGC to calculate the respective signatures used for authentication and current use by the MG or MGC, Then, by comparing the signature currently used by oneself with the signature used by the other party for authentication, the legitimacy of the other party can be judged, thereby completing the authentication of the other party's security identity. The above ideas can better realize the management of the security authentication mechanism.
[0040] During the negotiation and determination of the shared authentication key, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com