Secret key negotiation method based on SD cards
A key negotiation and session key technology, applied in the field of identity authentication, can solve the problems of small character space, PAKE scheme password dictionary attack, limited password length, etc., and achieve the effect of resisting phishing, simple and convenient implementation, and high-strength security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The implementation process of the technical solution of the present invention will be described in detail below with reference to the accompanying drawings and specific examples.
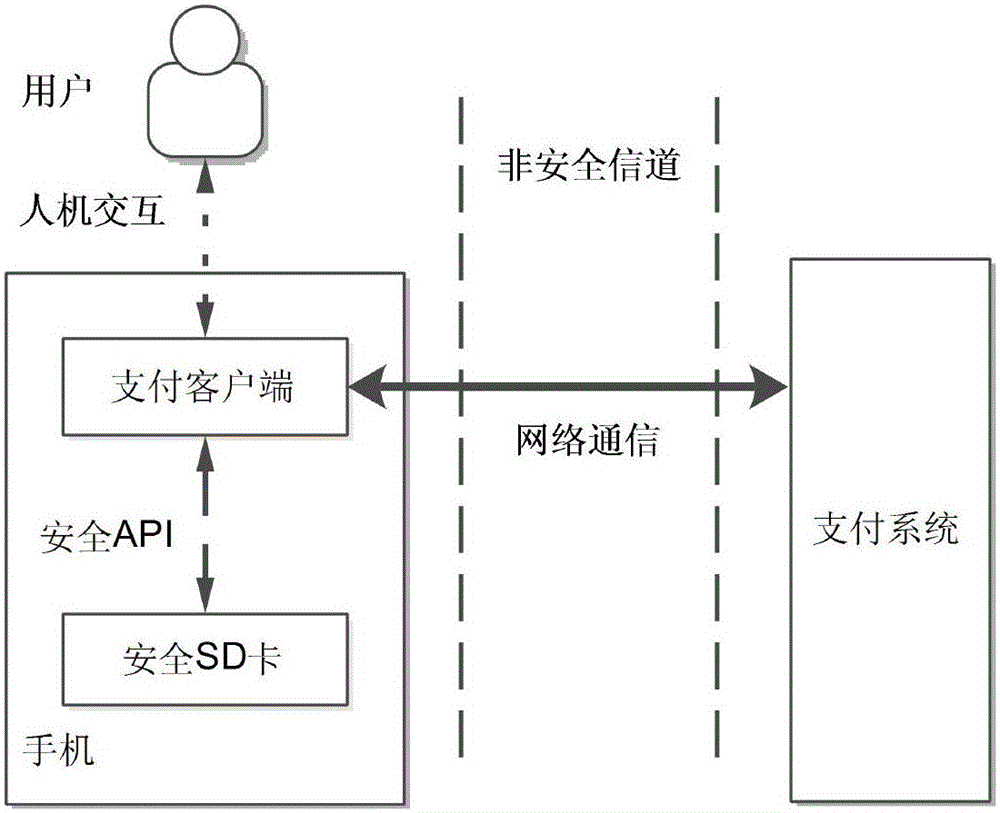
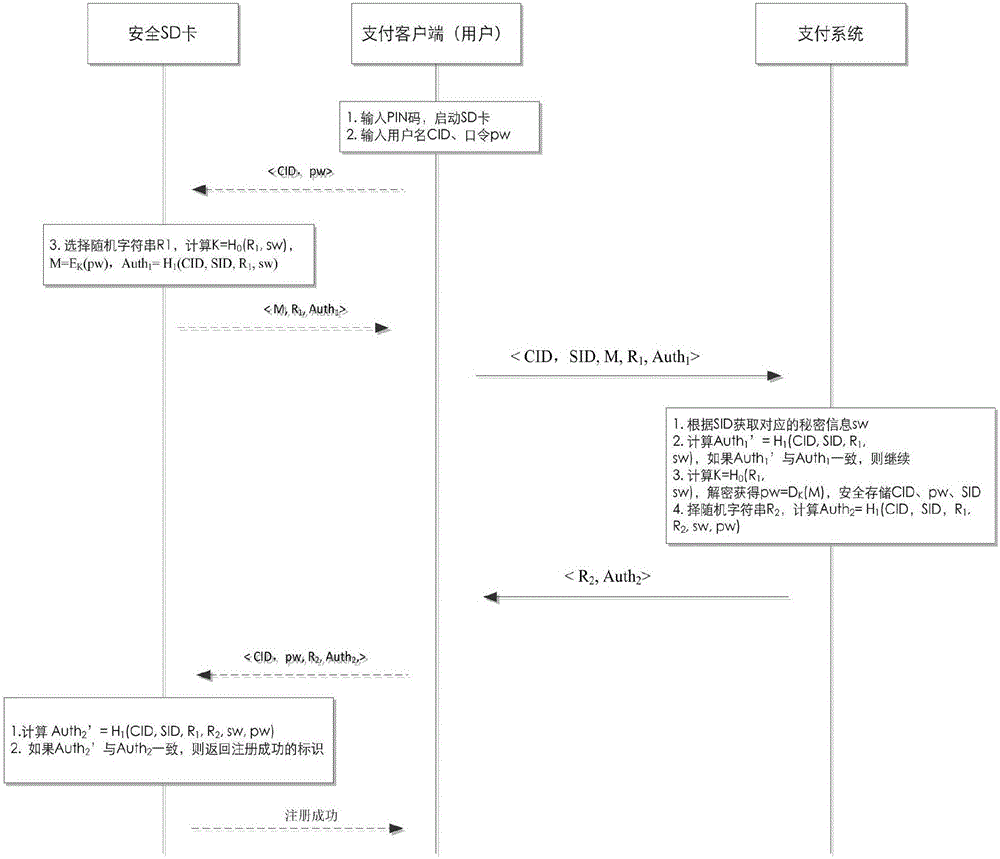
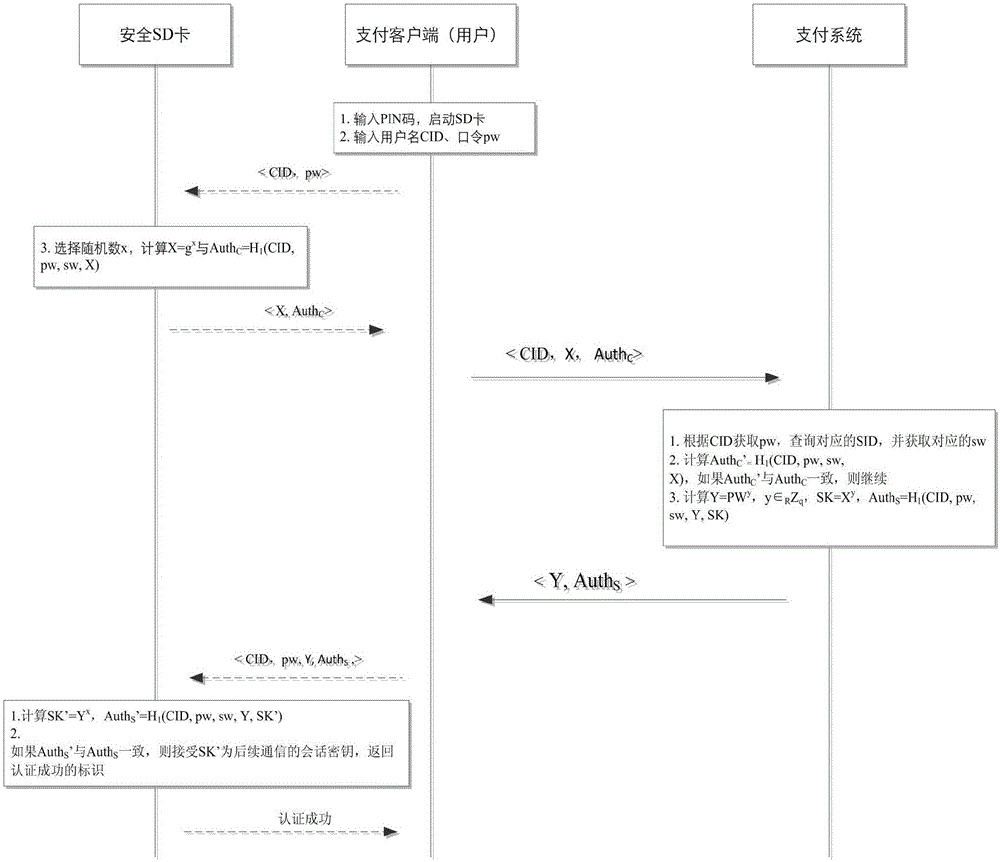
[0036] In the mobile payment scenario, the user communicates remotely with the payment system through the payment client installed on the mobile phone to complete four processes including user registration, authentication and key negotiation, password update, and SD card replacement. The payment client calls the secure API interface of the built-in SD card in the mobile phone to complete the secure computing operation. working model as figure 1 shown.
[0037] The user purchases a secure SD card issued by the payment system in advance. The preset secret information in the secure SD card is sw, and the payment system can obtain sw by querying the serial number SID of the secure SD card. The secure SD card is protected with a PIN code on the phone. Furthermore, the working parameters {q,g,E...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com