Anti-symmetric algorithmic based mobile terminal security lock network locking card protection and unlocking method
An asymmetric algorithm and mobile terminal technology, applied in the direction of public key for secure communication, radio/inductive link selection arrangement, user identity/authority verification, etc., can solve problems such as difficult implementation of complex solutions and easy cracking of solutions, etc. Achieve the effect of easy implementation, easy implementation and expansion, and cost saving
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
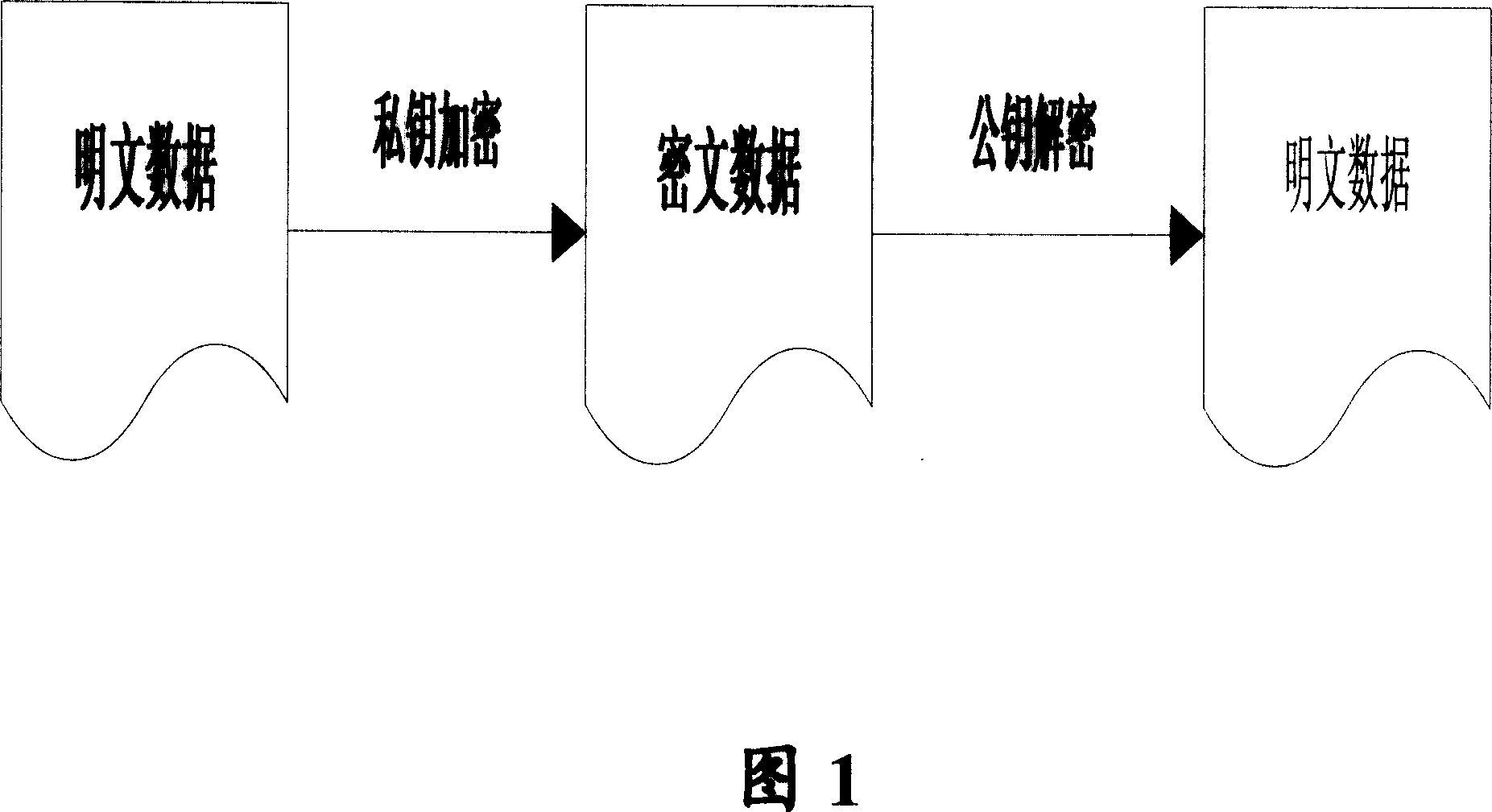
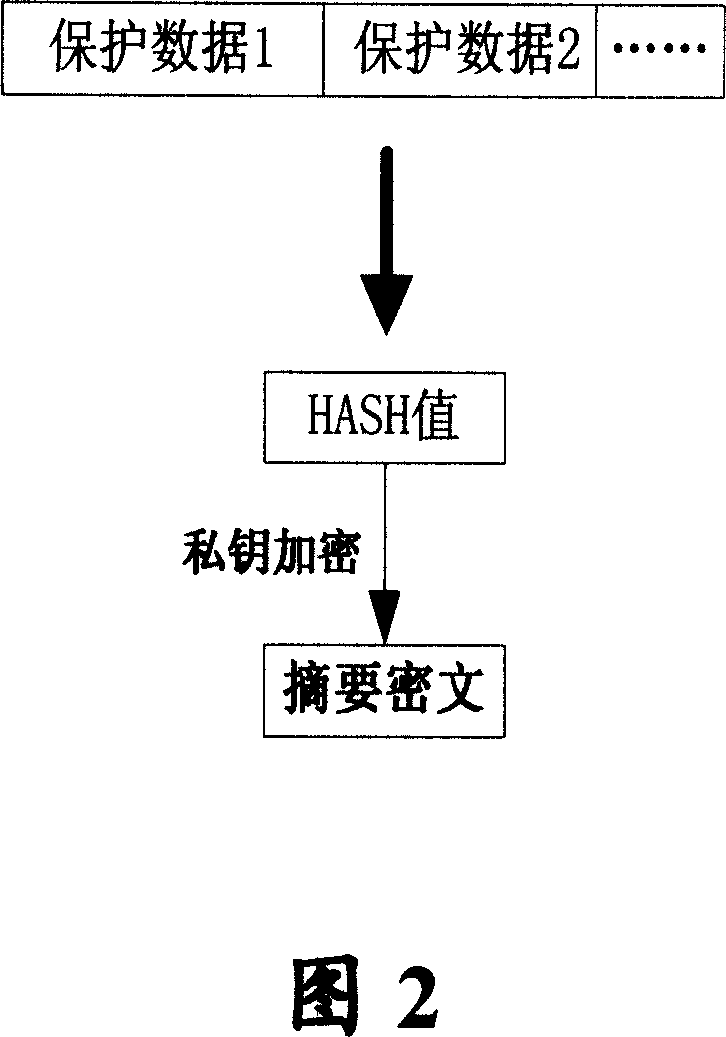
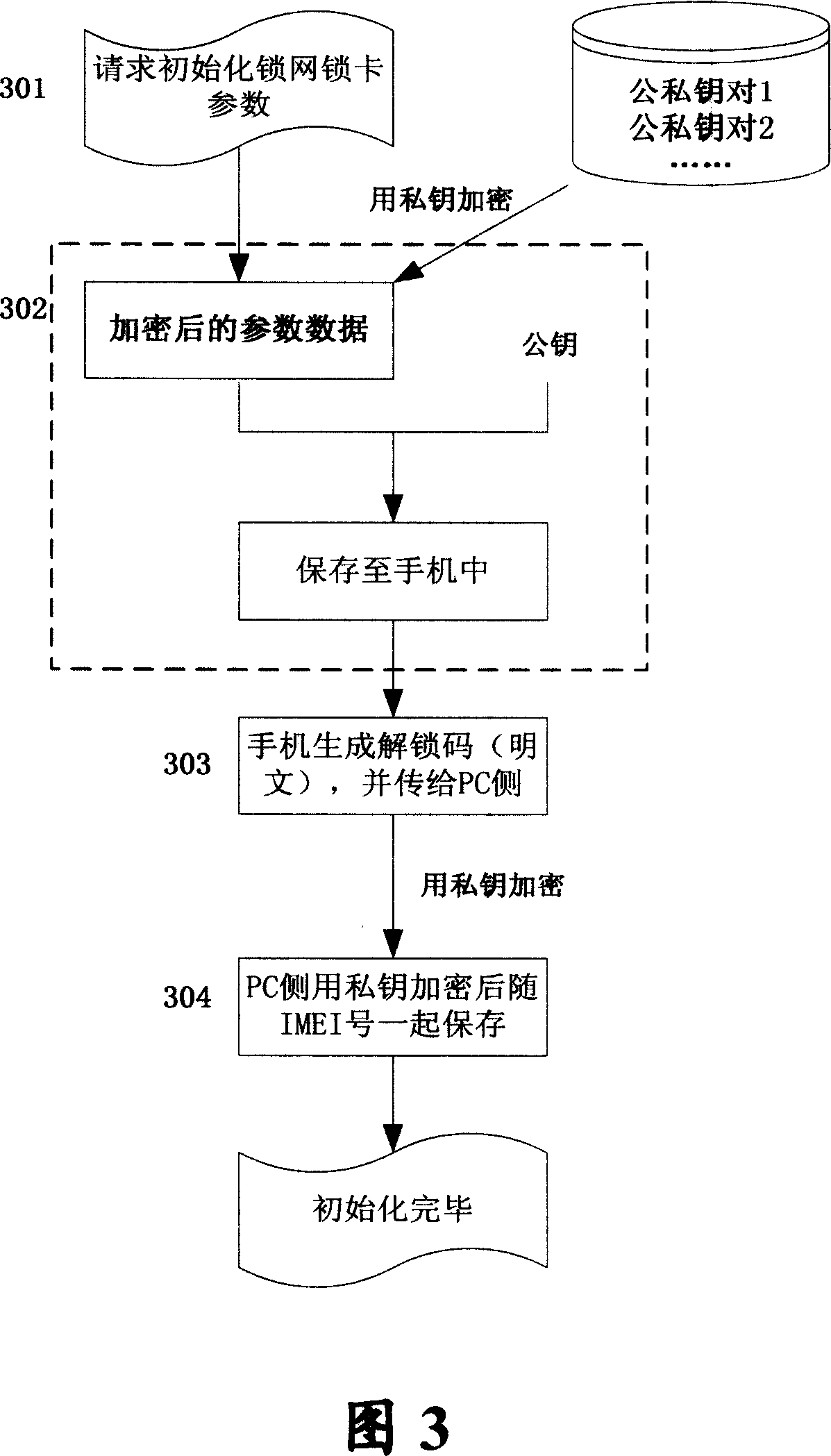
[0037] In order to solve the disadvantages of the traditional technical solutions, the present invention further elaborates a method for protecting and unlocking mobile terminal security lock network lock card protection and unlocking based on asymmetric algorithm through the following specific examples, and the specific implementation methods are described in detail below , but not as a limitation of the present invention.
[0038] The embodiments of the present invention use the storage conditions of ordinary mobile phones without adding special storage hardware or encryption hardware under the hardware conditions of the existing mobile terminal, that is, the mobile phone itself, thereby providing a safe, effective, easy-to-implement, feasible and highly secure Lock network lock card security mobile phone solution. The method proposed in this solution can be implemented on the two kinds of FLASH mentioned in the background art, so there is no need to consider the difference ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com