Authentication method for telephone subscriber identity
A technology for identity authentication and telephone users, applied in the field of identity authentication, can solve the problems of lack of identity authentication mechanism for callers, automatic identification of callers that cannot be identified, etc., and achieve the effect of reducing deception and harassment, and reducing participation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
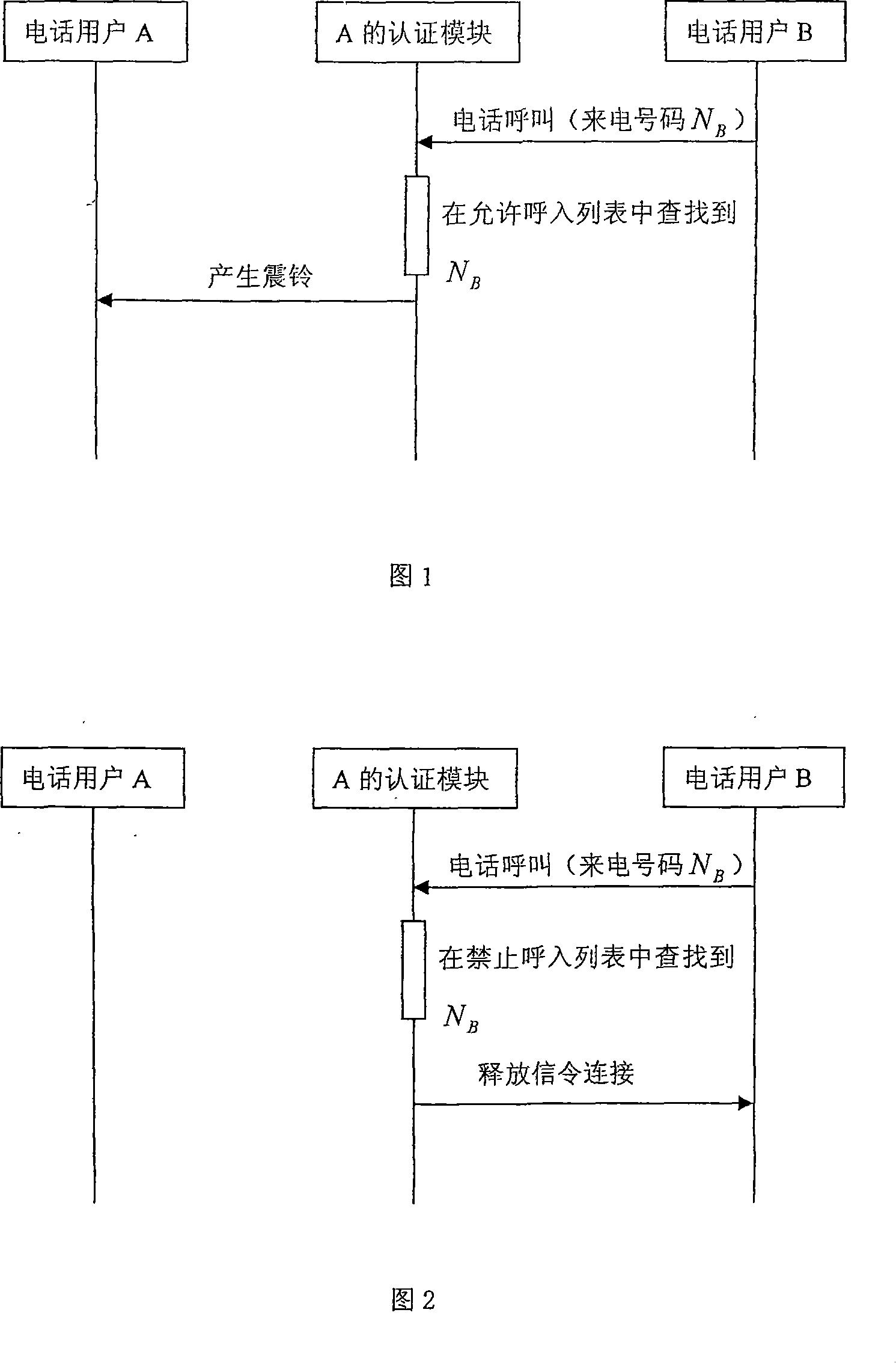
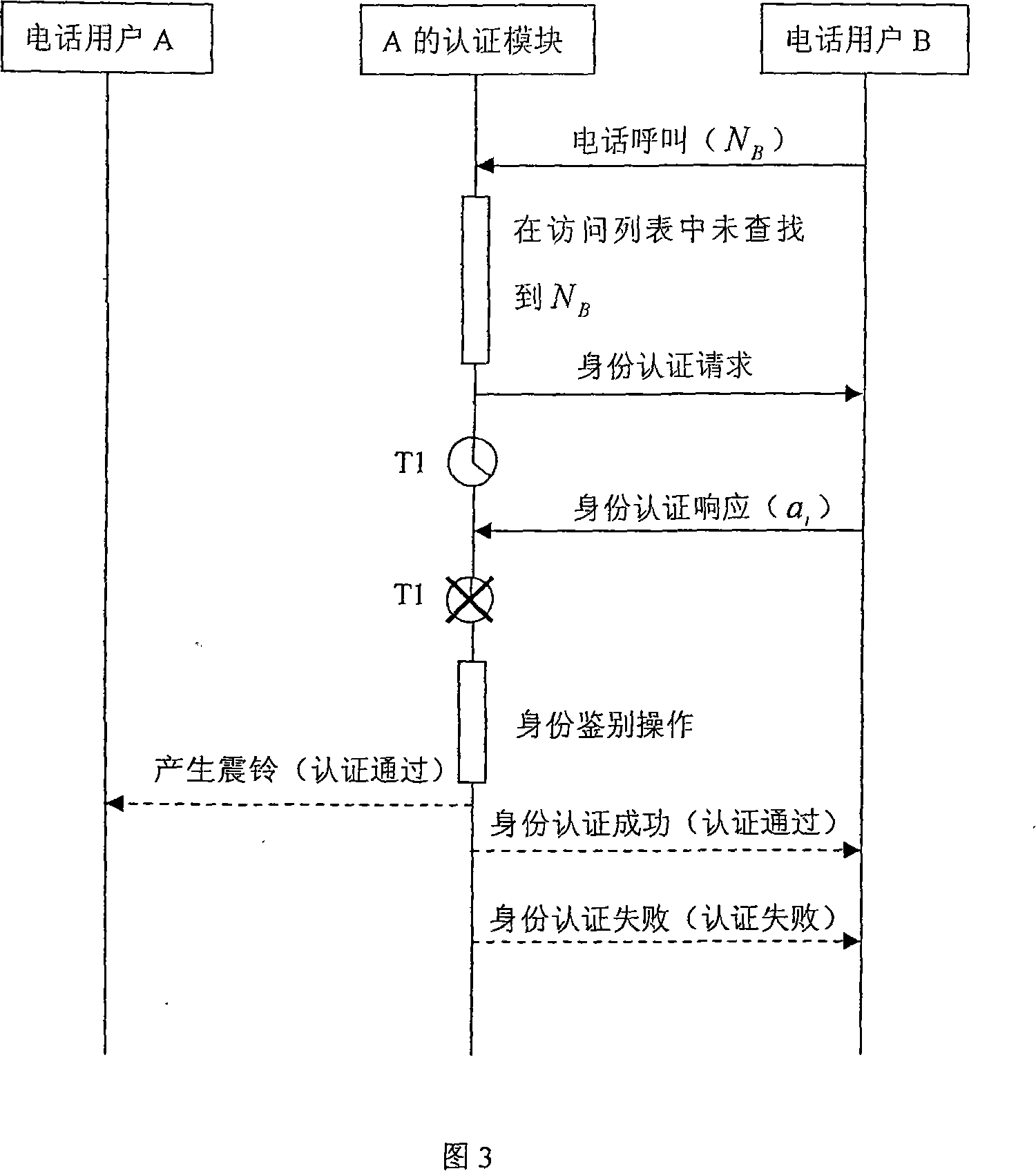
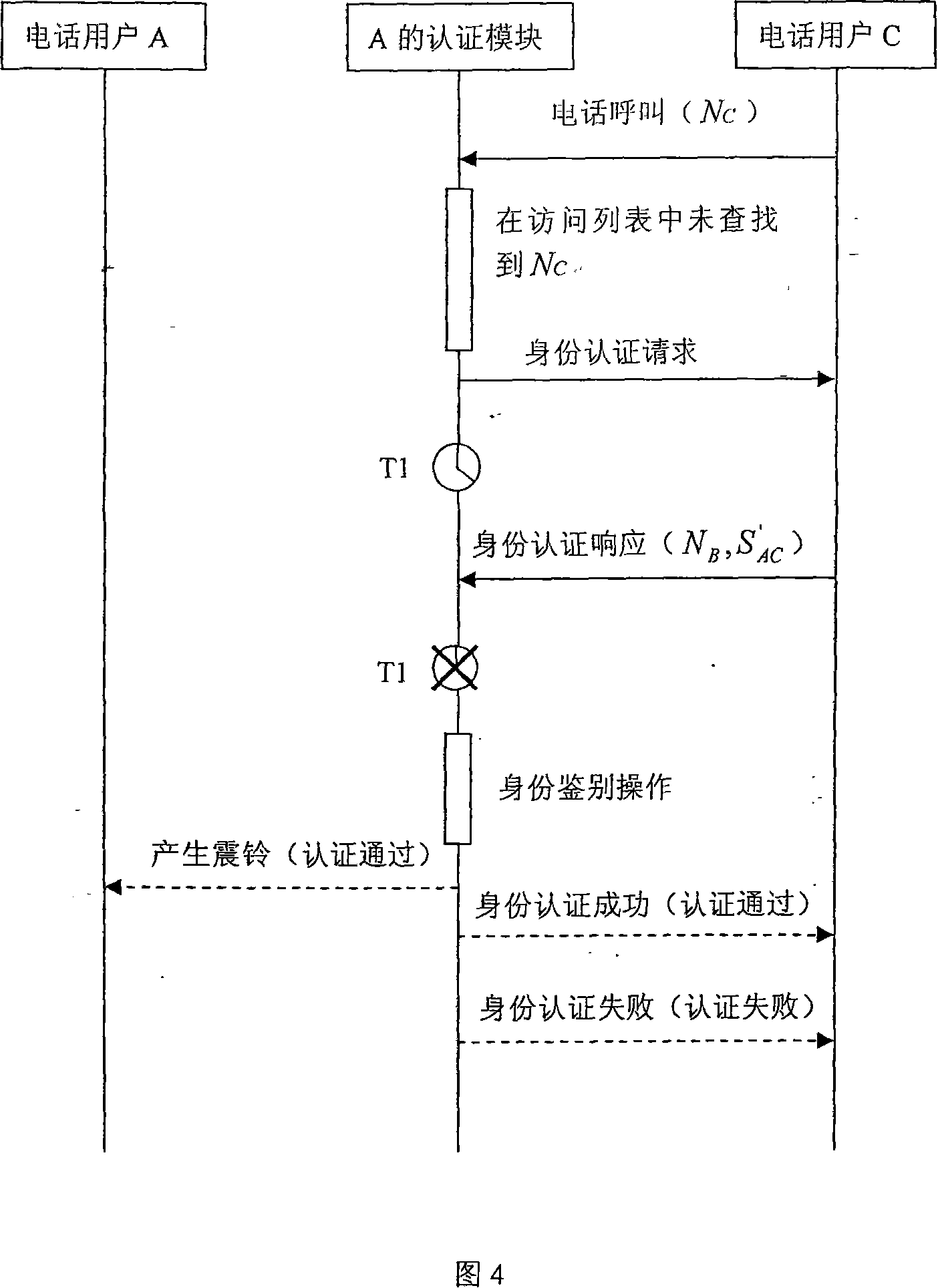
[0045] The telephone user identity authentication method described in the present invention mainly comprises (1) access list, comprises " allowed call-in list " and " barred call-in list "; ) The process of distributing identity authentication codes to users; (3) Identity authentication, which is to identify identity authentication based on authentication codes for phone (or short message) callers. The result of "authentication" is stored in the "access list".
[0046] The telephone user identity authentication method of the present invention (for telephone and short message, this identity authentication method is roughly the same, only introduces with telephone as example here) as follows:
[0047] Step 1: Distribution of identity verification codes
[0048] Before making a call, the initiator of the call first needs to obtain the valid identity authentication code of the call recipient through the process of "distribution of identity authentication code".
[0049] There ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com